Protect, Detect and Recover! The three key pillars a backup vendor is expected to offer when it comes to the NIST Cybersecurity Framework. The top priority on that list is protecting your data. A secure backup both on premises and in a private or public cloud offers immense protection. This can protect data from both a hacker accessing the backup server as well as the backup repository. Secondly, the ability to recover quickly is crucial. If the business cannot recover quickly, all the ransomware defense planning you did was for nothing. It is key to view ransomware in the same limelight as disaster recovery in order to meet these demands. Lastly, detecting malware and ransomware is critical for a backup vendor to provide, but it should be viewed as a last resort measure for companies who have other dedicated tools detecting ransomware.
Malware and Ransomware Detection With Veeam
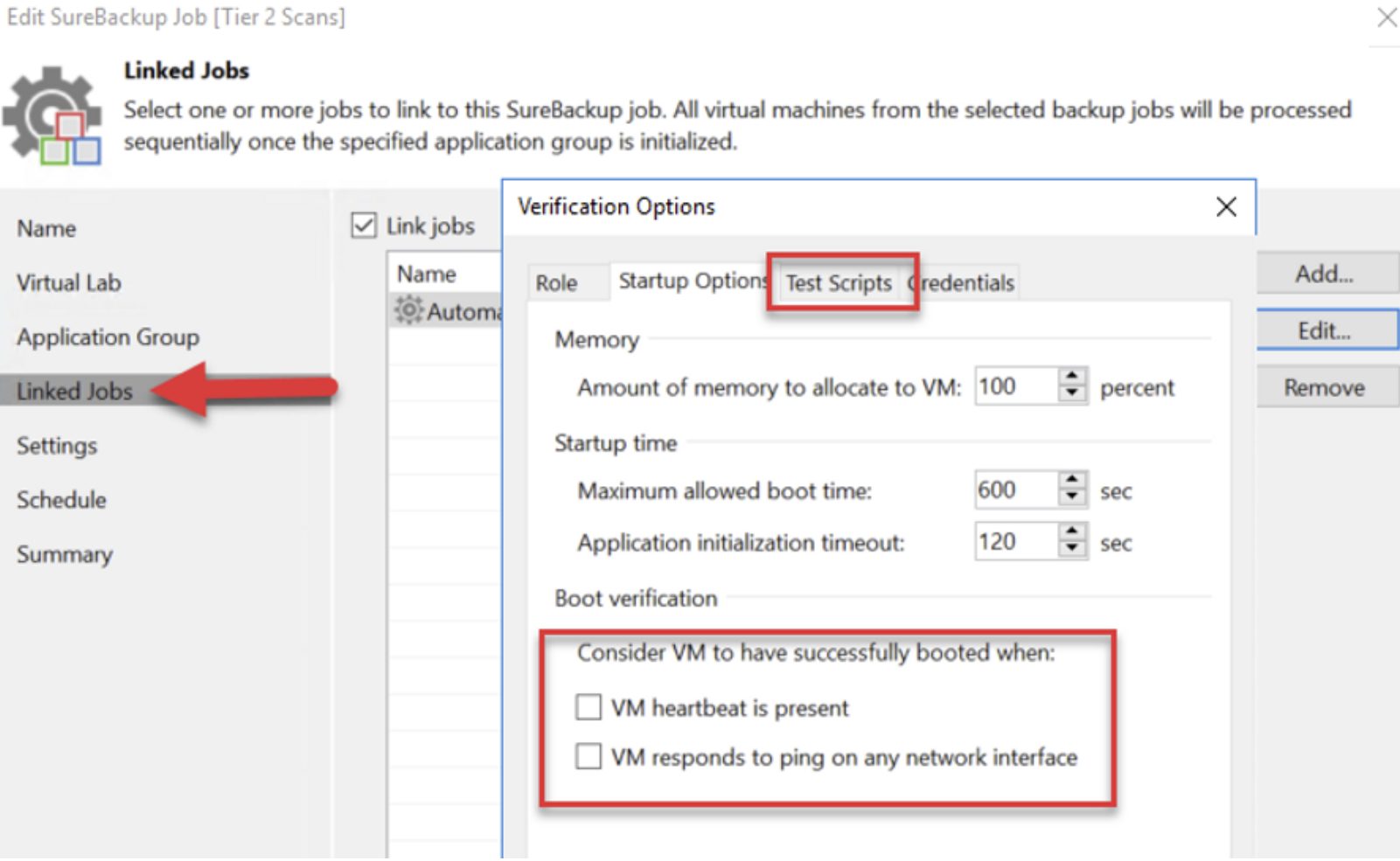
With that said, scanning backup files to assess their health and recoverability is crucial and something Gartner recommends as part of their Isolated Recovery Environment for backup vendors. Verifying backups to ensure no known vulnerabilities get re-injected into the production environment during restores can be a massive timesaver. Veeam can automagically do this with SureBackup. As the name implies, this enables users to verify backups are usable by both scanning the backup contents for malware/ransomware and checking the integrity of the backup via a CRC test. As a side note, you can use any scanning tool that has a CLI. For example, Trend Micro, Bitdefender, Windows Defender, etc. Simply edit the XML file here. I am using ESET.
Linking SureBackup jobs with a daily backup policy means you can come into work not only with finished backups, but also backups that have been inspected. As you can see below, there are many other possibilities with SureBackup. This post is specifically leveraging the tool to scan backup contents, but you could also create a small DR test by ensuring VMs are connected to the network in a restore and inserting any custom scripts.
Results of the SureBackup job are in the task log of the UI and/or the emailed report. Below is a glance of the UI. We can see the AV scan took a little over 12 minutes and the CRC test was less than a minute. Not only is this helpful for compliance purposes to prove backups are tested regularly, but also for peace of mind.
Lastly, below is what an emailed report will look like if you instructed SureBackup to send a notification. You can send emails to a group or to multiple addresses.
This Is Great, but How Would a Larger Organization Use This?
A great way to set this up in the real world if you’re a larger business is to run a weekly SureBackup on a handful of your important VMs in each backup policy. For example, create a SureBackup for each backup job and stagger them throughout the week. This will keep the load balanced on the server you’re mounting the file to. In addition, you can increase the performance if you have the compute resources to mount backup files to multiple servers. This will allow you to scan multiple backups in parallel.
Conclusion
Nearly all meetings lately are about a ransomware defense strategy. During these conversations though, nobody acknowledges the gigantic elephant in the room shouting, “If your backup vendor is the one detecting ransomware, you’re probably opening a Coinbase account.” Don’t get me wrong, a backup solution should absolutely provide a way to help detect ransomware, but companies need a holistic approach for this fight. There is an entire industry dedicated to detecting ransomware. Having a secure copy you can quickly recovery from should be a company’s top priority in a backup solution. After all, it doesn’t matter what you detect if you can’t recover a safe copy quickly.
I Hate Uis. I Want to Script.
If you prefer scripting, you can run the script below and link it to your backup policy under the post-script option.
Connect to your Veeam backup server.
Add-PSSnapin VeeamPSSnapin -ErrorAction SilentlyContinue
Connect-VBRServer -Server "servername"
Create variables for the VMs you want to scan. You will want to change the name of the VM and target server that will be used for inspecting and cleansing.
$restorepoint = Get-VBRRestorePoint -Name "VMname" | Sort-Object -Property CreationTime -Descending | Select-Object -First 1
$targetServerName = "servername"
$targetAdminCredentials = Get-VBRCredentials -name "credentials" | where {$_.description -eq "description"}
$restorepoint = Get-VBRRestorePoint -Name "ATLNIMBLE_WIN" | Sort-Object -Property CreationTime -Descending | Select-Object -First 1
Now that your variables are set, you’re ready to mount the VM to the server.
$session = Publish-VBRBackupContent -RestorePoint $restorepoint -TargetServerName $targetServerName -TargetServerCredentials $targetAdminCredentials
Below is an example using ESET to scan the contents of the mounted disks and dump the script output to “ecls.txt.” Fun fact, starting your PS command with “&” allows you to run CLI commands in PS. The mount will always be under C:\VeeamFLR\.
& "C:\Program Files\ESET\ESET Security\ecls.exe" /base-dir="C:\Program Files\ESET\ESET Security\Modules" /subdir "C:\VeeamFLR\" /log-file=c:\ecls.txt /aind /unsafe /unwanted /suspicious /clean-mode=standard
Unmount the server and mark the script as complete.
Unpublish-VBRBackupContent -Session $session
If you want to run it all at once:
$restorepoint = Get-VBRRestorePoint -Name "VM-name" | Sort-Object -Property CreationTime -Descending | Select-Object -First 1
$targetServerName = "servername"
$targetAdminCredentials = Get-VBRCredentials -name "creds" | where {$_.description -eq "description"}
$session = Publish-VBRBackupContent -RestorePoint $restorepoint -TargetServerName $targetServerName -TargetServerCredentials $targetAdminCredentials
& "C:\Program Files\ESET\ESET Security\ecls.exe" /base-dir="C:\Program Files\ESET\ESET Security\Modules" /subdir "C:\VeeamFLR\" /log-file=c:\ecls.txt /aind /unsafe /unwanted /suspicious /clean-mode=standard
Unpublish-VBRBackupContent -Session $session