Exchange Backup Fails With: "Failed to get folder properties. Not allowed to access Non IPM folder"
Challenge
A backup job in Veeam Backup for Microsoft 365 processing Exchange data fails with the error:
Failed to get folder properties. Not allowed to access Non IPM folder
Cause
During Exchange backup, Veeam Backup for Microsoft 365 requests the properties of all mailbox folders, including the properties of hidden and legacy folders (e.g., ‘TeamsMessagesData’).
Due to a recent change in Microsoft 365, the properties of the ‘TeamsMessagesData’ folder cannot be retrieved using the EWS API, which is used by Veeam Backup for Microsoft 365 to process Exchange data backup.
Solution
More Information
Workaround
This workaround is provided for customers who are not ready to upgrade to the latest version of Veeam Backup for Microsoft 365 and are using at least build 6.1.0.1015.
If a build of Veeam Backup for Microsoft 365 older than 6.1.0.1015 is presently installed, we suggest upgrading to the latest version of Veeam Backup for Microsoft 365, which will resolve the issue and ensure that a supported version is in use.
There are two options to implement this workaround; choose only one:
Option 1: PowerShell Script to Update Config.xml
The script below was created by Veeam and is provided as a courtesy. Note, however, that if any problems occur with the script, Veeam Support will recommend upgrading to the latest version of Veeam Backup for Microsoft 365 to resolve the issue.
- Execute the following PowerShell script as Administrator on the Veeam Backup for Microsoft 365 server:
Note: Any active Restore Session(s) will be halted when this script restarts the Veeam Backup for Microsoft 365 Service service. Backup jobs should not be affected because running jobs are managed by the Veeam Backup Proxy for Microsoft 365 Service service, which is not restarted by this script. After the Veeam Backup for Microsoft 365 Console is launched, the status of running jobs may take a moment to update.
$configFilePath = "C:\ProgramData\Veeam\Backup365\Config.xml"
$xmlContent = [xml](Get-Content $configFilePath)
if ($xmlContent.SelectSingleNode("//Archiver/Proxy[@SkipTeamsMessagesDataFolders='True']")) {
Write-Output "SkipTeamsMessagesDataFolders setting already exists. No changes made."
} else {
Copy-Item -Path $configFilePath -Destination "$configFilePath$($(Get-Date -Format '.yyyyMMdd')).old"
$newElement = $xmlContent.CreateElement("Proxy")
$newElement.SetAttribute("SkipTeamsMessagesDataFolders", "True")
$archiverNode = $xmlContent.SelectSingleNode("//Archiver")
$archiverNode.AppendChild($newElement)
$xmlContent.Save($configFilePath)
Write-Output "SkipTeamsMessagesDataFolders setting added."
Restart-Service -Name "Veeam.Archiver.Service"
}- Retry the job(s).
Option 2: Manually Update Config.xml
- Update the Config.xml file to skip the TeamsMessagesData folder.
Only the config.xml file on the main Veeam Backup for Microsoft 365 server needs to be updated.
- Open the folder: C:\ProgramData\Veeam\Backup365\
The ProgramData folder is hidden by default. Copy and paste the folder path into the Explorer address bar. - Within that folder, create a copy of Config.xml with the extension .old (i.e., Config.xml.old).
If the Config.xml file is not present, double-check the folder path (i.e., ProgramData not Program Files). - Launch NotePad as an Administrator, and open C:\ProgramData\Veeam\Backup365\Config.xml
- Add the following line withinAnywhere below and above . the <Archiver> section and save the file.
- Open the folder: C:\ProgramData\Veeam\Backup365\
<Proxy SkipTeamsMessagesDataFolders="True" />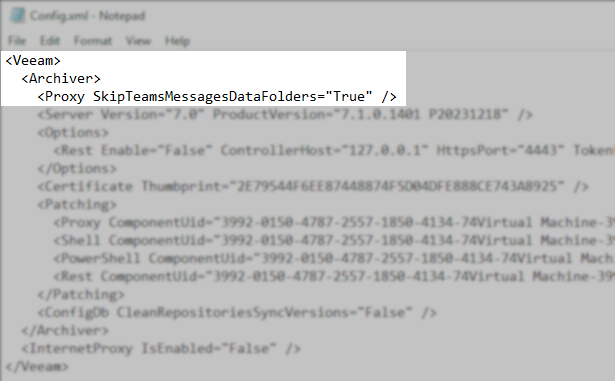
- Restart the Veeam Backup for Microsoft 365 Service service.
Note: Restarting the Veeam Backup for Microsoft 365 Service will cause any active Restore Session to halt. Active backup jobs should not be affected because once they are started, they are managed by the Veeam Backup Proxy for Microsoft 365 Service service, which does not need to be restarted. After the Veeam Backup for Microsoft 365 Console is launched, the status of running jobs may take a moment to update. - Retry the job(s).
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.