Along with the new functionality of Windows Server 2016, another essential element of any domain administrator — Active Directory — has been updated with some very important and great features. One of the updates that aims to improve the environment’s protection against external and internal threats to accounts is called privileged access management (PAM). This functionality is based on the idea of Just Enough Administration (JEA), which is a security technology that allows the delegation of administration rights with the help of PowerShell.
The idea is to grant the administration rights only for a certain period. With PAM, we can set the time limit on a group membership by setting a Time to Live (TTL) value. In other words: You can add a user to a group that will be active for a limited time only. This comes in handy in situations when you need to grant access to your AD environment to a third party or to help desk personnel who are troubleshooting problems in the environment but don’t need elevated permissions on a permanent basis. And it’s only logical to limit the time they have the access rather than do the manual clean-up after they’re done, which is doomed to be forgotten.
Let’s dive into the procedure. Be aware that, as with Active Directory Recycle Bin, this function is not enabled by default and once enabled, you can’t turn it off.
Requirements and how to enable
To enable PAM, we need to ensure that the forest functional level is at Windows Server 2016. You can do so like this:
- Get the Active Directory Forest functional level
(Get-ADForest).ForestMode - Get the Active Directory Domain functional level
(Get-ADDomain) .DomainMode - Get the Active Directory Domain suffix:
Get-ADDomain | Select-Object DNSRoot | fl - Enable “Privileged Access Management Feature”
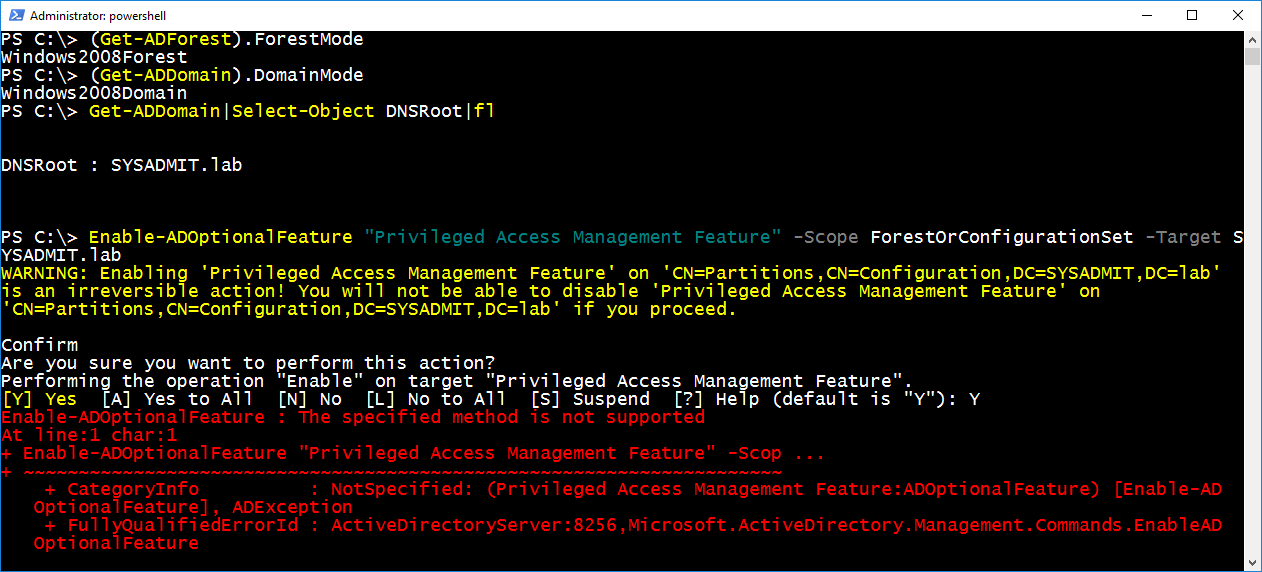
Enable-ADOptionalFeature "Privileged Access Management Feature" -Scope ForestOrConfigurationSet -Target SYSADMIT.lab - Check “Privileged Access Management Feature” status:
Get-ADOptionalFeature -filter {name -like "Privileged*"}
If we try to activate this feature with a lower forest functional level than Windows Server 2016, we will get the error (see Figure 1).
To increase the functional level of both the domain and the forest, there are several tools that we can use:
- Active Directory Domains and Trusts (domain.msc) — We can find this tool starting from Windows Server 2000
- Active Directory Administrative Center (dsac.exe) — We can find this tool from starting from Windows Server 2008 R2
- PowerShell (Active Directory Module)
Since we’re on Windows Server 2016, we will use PowerShell to increase the domain and forest functional level.
In the example, the name of the DC is S1 and the domain is SYSADMIT.lab.
- Raise the Domain Functional Level to Windows Server 2016
Set-ADDomainMode -identity S1.SYSADMIT.lab -DomainMode Windows2016 - Raise the Forest Functional Level to Windows Server 2016
$ Forest = Get-ADForest
Set-ADForestMode -Identity $ Forest -Server $ Forest.SchemaMaster -ForestMode Windows2016
Helpful things to know:
- To enable the PAM feature, you only need to raise the forest functional level to Windows Server 2016, but not the domain functional level.
- As a rule, Active Directory functional levels cannot be reversed. The exception would be Windows Server 2008 R2 where the forest functional level can be reversed back to 2008 level if the Recycle Bin hasn’t been enabled. In case of 2016, this operation would be irreversible.
- Special attention is required when raising a functional level for applications like Exchange Server. Each version of Exchange Server requires a specific functional level.
Temporary group membership in action
To run a quick test of the temporary group membership, we will create a group and a user who we will add to that group by setting a TTL value.
- Add AD User (in the example, the username is: Xavi)
New-ADUser -Name "Xavi" -UserPrincipalName Xavi@SYSADMIT.lab - Set AD user password
Set-ADAccountPassword -Identity "Xavi" - Add AD global group (in the example, the group name is: Temp-MemberShip)
New-ADGroup -name "Temp-MemberShip" -groupscope Global - Enable AD User
Enable-ADAccount -Identity "Xavi" - Add the User “Xavi” into “Temp-MemberShip” only for 2 days
$variable = New-TimeSpan -Days 2
Add-ADGroupMember -Identity "Temp-MemberShip" -Members Xavi -MemberTimeToLive $variable
That’s it! After two days, the user “Xavi” will no longer be a member of the group “Temp-MemberShip,” and no manual action is required.
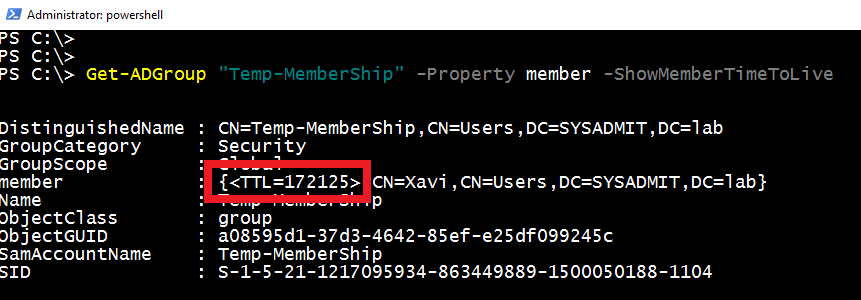
You can check the user group membership TTL value with the following command (see example in a Figure 2):
Get-ADGroup "Temp-MemberShip" -Property member -ShowMemberTimeToLive