Read the full series:
|
Ch.1 — Backing up Domain Controller |
This post is part four of a series where I discuss granular recovery of Active Directory objects and different scenarios and tools for such operations.
In the previous article, I described the cases where administrators worked with Domain Controllers running Active Directory off a functional level of Windows Server 2003 and Windows Server 2008. I detailed the steps they had to do in order to reanimate the tombstone objects using LDP and Veeam Explorer for Microsoft Active Directory utilities.
Today, I’m moving on to newer systems with the Active Directory recycle bin feature enabled.
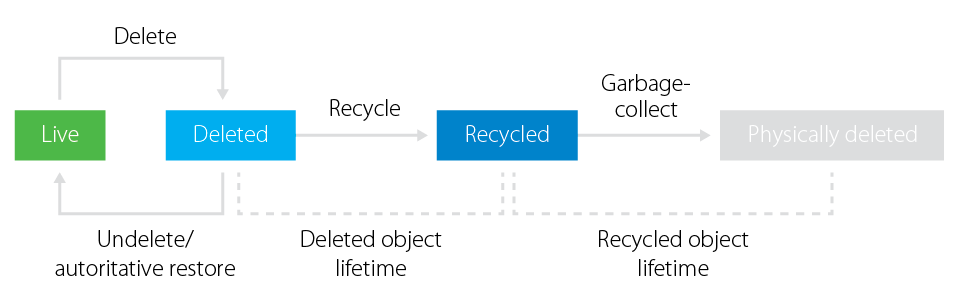
With Windows Server 2008 R2, Microsoft implemented a long-awaited Active Directory recycle bin. This extended the standard life cycle of an Active Directory object and changed the logic of object deletion. With this feature enabled, the object started going to the deleted objects container right after deletion, where it stays for the lifetime of the deleted object (equal to recycled object lifetime by default). Most important, the system is able to preserve all of the object’s link-valued and non-link-valued attributes for the same lifetime period. This means you can easily restore an object with those attributes during this period.
Once the lifetime is over, the system changes the object status to recycled and drops most of its attributes. Additionally, the object becomes logically equal to what used to be tombstone in Windows Server 2003 and Windows Server 2008. The only difference is that you can’t restore or reanimate the recycled object now. A garbage collector removes it automatically after a recycled object lifetime expires (180 days by default).
Figure 1. Active Directory object life cycle with Active Directory recycle bin enabled
Enabling Active Directory recycle bin
So far, the Active Directory recycle bin is not enabled by default on any Windows Server OS. To utilize this tool, you should prepare your environment, make sure that every DC in your forest is running Windows Server 2008 R2 and newer, and set your forest functional level to Windows 2008 R2 or above.
NOTE: Enabling the Active Directory recycle bin as well as any other substantial change to Active Directory (or other production systems) may be an intimidating task. You can use Veeam Virtual Lab technology to test schema upgrades or any other potentially impactful change before you do so in production. Additionally, the virtual lab can hold other VMs you have which are critical, so that they can go through the change as well and test multi-tiered applications for compatibility after the changes. The virtual lab can run from backups, replicas or even storage snapshots (depending on configuration). This way, there are no surprises in production.
Before using the Active Directory recycle bin, keep in mind that:
- Enabling the Active Directory recycle bin changes all current tombstone objects into recycled objects, so you won’t be able to restore them once enabling is done.
- The process of restoring multiple dependent objects can be difficult, because it requires a strict order of restore, starting from the higher-placed objects.
- In Windows Server 2008 R2, every operation related to the Active Directory recycled bin should be done via PowerShell cmdlets, no GUI provided. Windows Server 2012 and above introduce Active Directory Administration Center (ADAC), where all recycle bin operations can be performed via GUI.
- The recycle bin doesn’t have anything in common with Active Directory backup, and it won’t help to restore a whole DC if it is damaged.
Figure 2. Enabling Active Directory recycle bin in Windows Server 2012 via ADAC
The Pros & Cons of Active Directory recycle bin
When you enable the Active Directory recycle bin, you will notice a new Deleted Objects container visible via the Active Directory Administration Center. By browsing this container, you can see all deleted but not recycled objects, check their properties and restore them to a default or custom place.
Figure 3. Navigating through the Deleted Objects container in the Active Directory recycle bin
Even though it looks much easier to perform granular recovery operations using this functionality than using LDP utility or performing authoritative restore of a domain controller, it also has some considerations. Below, I outlined the pros and cons of using Active Directory with the recycle bin feature enabled.
Pros:
- A universal method for Windows Server 2008 R2 functionality level (or newer) domains
- Great lifetime period (180 days by default is a sufficient time for majority cases)
- Object attributes are preserved for a lifetime period
- Recovery doesn’t require a reboot of a DC
- GUI for Windows Server 2012 and newer
Cons:
- Doesn’t work for Windows Server 2008 functionality level (or older) domains
- Doesn’t work for changed objects (object can be restored if deleted, not changed)
- Recovery is limited by a lifetime period value
- Doesn’t protect against issues with DC itself (never be good as a backup copy)
- No automation for hierarchy recovery
The second drawback is the most disturbing. What if the object wasn’t deleted, but occasionally changed, and the mistake is noticed after a while? Unfortunately, recycle bin won’t help here, and you have an issue to solve.
Solving recycle bin limitations with Veeam
Considering cons of recycle bins, they might not be a deal-breaker for some of you. However, those who want an ultimate solution should look somewhere else. Here comes Veeam, offering the same Veeam Explorer for Active Directory, which was previously discussed. This tool simply eliminates limitations of Active Directory recycle bin. With this utility, your Active Directory objects are protected as long as you keep backups around. It works for domain controllers with forest functional level of Windows Server 2003 and newer. Most importantly, it is a part of Veeam Backup & Replication, and is included in the Free Edition.
With a combination of Veeam Backup & Replication and Veeam Explorer for Active Directory, you can restore the entire DC at once and recover individual Active Directory objects: OUs, computer and users accounts with their passwords, GPOs, DNS records and more. Besides that, it’s easy to launch the Explorer and compare objects in a backup copy with live objects in production to notice the difference and changed objects attributes.
The example below shows a situation in which an administrator noticed a change in attributes of a user account and was asked to recover the user account to a previous condition.
Figure 4: Recovering changed Active Directory objects
Either way, thinking about possible Active Directory disasters in advance and testing different tools to prevent and fix these disasters will help you sleep soundly at night.
Hope this series triggered your mind and made you recheck your Active Directory protection strategy. Feel free to reach out to me in the comments to discuss more.