Read the full series:
|
Ch.1 — Protecting the Active Directory Domain Services |
This blogpost is the third in a three-part series on AD (Active Directory) administration best practices. Have you ever had the horrible realization that you just deleted the wrong computer account from the domain? Or have you ever reset a service-account password for a mission-critical application and the password reset broke an entire application suite and had to rollback? And, worse, you didn’t save the old password? Bad moments like these happen to IT pros just like you. The questions are how to recover and do it quickly. Thankfully, you CAN restore service quickly. All you need are the right tools. And I am sure you’d agree that restoring service quickly is A LOT more pleasant than updating your resume!
Earlier in this series, I touched on the importance of Active Directory Domain Services (AD DS) and the role that properly architecting a robust, resilient and highly available service can play in the modern data center. Even with the best design and architecture, things can and will go wrong. Unfortunately, it just so happens that these issues always seem to arise at either 3 a.m., or just as you’re walking out the door to go home for the day. Simply following a few of the best practices laid out in my earlier posts is not enough to fix things. Instead, it is paramount to have an out-of-band availability solution for AD DS, your infrastructure’s most mission-critical service.
Traditional Domain Controller restore scenarios
Backup and recovery of an AD Domain Controller (DC) has traditionally been a tedious process that involves backing up the system state of the server. It’s a best practice to backup two DCs from each domain, one of which should be an Operations Master role holder, but NEVER the RID Master. When it comes to recovery, you go through the process of rebuilding a brand new server (MUST BE THE SAME EXACT NAME) and restoring the system state, which includes the SYSVOL and actual AD files (ntds.dit), edb.chk and all transaction logs). Then you determine if a Non-Authoritative restore is good or if you need to go through an Authoritative Restore process.
- For a Non-Authoritative restore process: This restores the DC back to the restore point chosen and then allows normal replication to occur and update the DC to the latest iteration.
- For an Authoritative restore process: First you must go through an Authoritative Restore and then go one step further. Authoritative restores effectively update all objects in the domain, making the newly restored DC the authoritative copy. Each of the other DCs are then updated via standard replication.
This process can get so complicated that it very quickly makes the steps outlined earlier even MORE important. Remember to only give the exact permissions that are required to do the job, do not OVER-permission. Do leverage the lag site for delaying replication of changes. In addition, do leverage RODCs for branch/satellite office locations. Steps can and should be taken to mitigate as much risk as possible. Bottom line? Always adhere to best practices!
To simplify things, as long as there is a single surviving DC in the infrastructure, you should build a new DC (a virtual machine) and promote via the normal procedures. This allows AD replication to update it to the current state.
Native Microsoft tools (ldp.exe or Get-ADObject and Restore-ADObject) do not make it easy to recover individual User Objects, let alone the associated attributes!
Veeam’s here to help!
For years, Veeam has been aiding the virtualization community with tools that help make the job easier! Veeam Explorer for Active Directory simplifies the entire process associated with traditional Domain Service Restoration by allowing browsing of the AD database to locate containers, objects and their associated attributes. This is all possible through a single-pass, image-level backup! Yep, that’s right, 100% agentless Backup & Recovery!
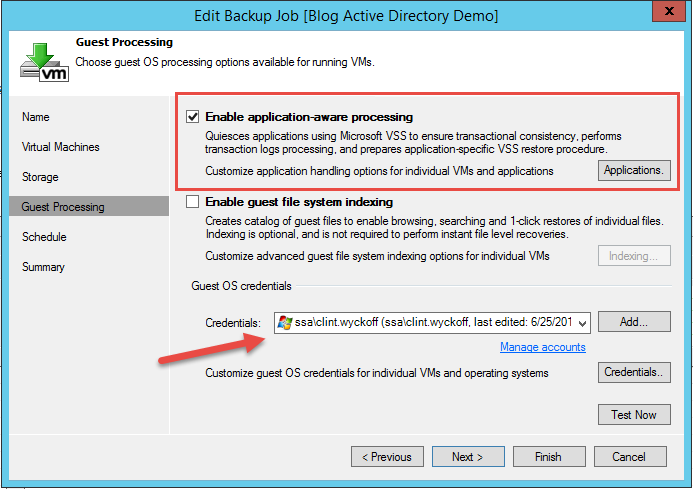
How’s it done? It’s simple, during the creation of your Veeam Backup Job, select Enable application-aware processing and pass through the Guest OS (operating system) credentials that are an Administrator on the server. In this case for a DC, you’ll need to pass Domain Admin credentials. Through the backup process, Veeam will leverage Volume Shadow Copy (VSS) to place the DC in a consistent state. You can check the application logs on the DC during the time of backup for validation.
Figure 1: Guest processing settings within backup job
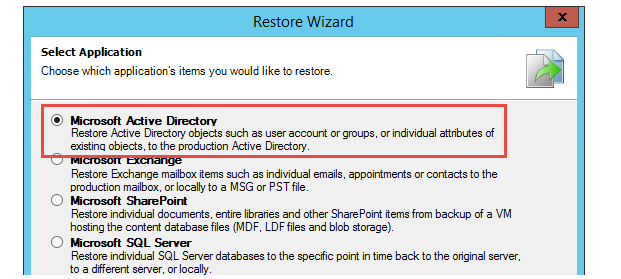
When the backup job is complete and you run through the Restore Wizard, just choose Microsoft Active Directory and the associated restore point you’d like to restore from.
Figure 2: Application Item Recovery Wizard
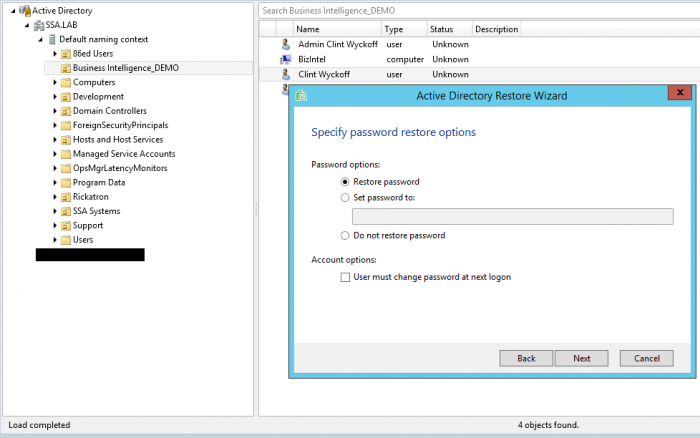
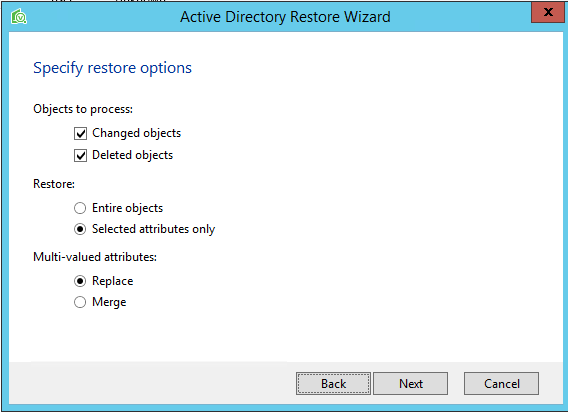
Maybe you’re looking to recover an entire object or container such as a user, computer or organizational unit? Just right-click on the object and restore back to the original location. Are you looking to restore individual attributes, like a service account password or perhaps a PowerShell script that went rogue and updated all Domain Users email addresses? Within the same Restore Wizard, simply restore selected attributes and whether or not you need to replace or merge the changes.
Note: Not all object attributes are visible through Active Directory Users and Computers (dsa.msc). Don’t be shy about checking out ADSI Edit if you’re unfamiliar with this information.
Figure 3: Veeam Explorer for Microsoft Active Directory Restore Wizard
Figure 4: Veeam Explorer for Microsoft Active Directory Restore Wizard
Testing, testing and more testing!
One commonly overlooked best practice is to test the application restoration process. Veeam makes this simple through SureBackup. SureBackup leverages the patented vPower technology to power on your VMs from their compressed and deduplicated backup image within a fenced off lab environment (Veeam creates a separate VMware vSwitch and / or equivalent Hyper-V Private Virtual Network). This lab is a great way test to see if your DC backups are in a good place and it’s also a fantastic application test bed. Consider it a best practice to fire up all associated VMs within an application suite and test in an automated fashion to leverage the data you have. CIOs love that this is easy to audit and provides complete visibility into the availability of the environment.
Conclusion
AD Domain Services is one of the most mission-critical applications in the environment. All aspects of application communication and authentication processes require AD. IT professionals are faced with challenges on a daily basis. Availability should not be one of those challenges! This best practices series is intended to aid you in the successful design, implementation and ongoing availability of your AD DS.
Veeam continues to provide high-speed recovery for all AD Services through its Veeam Explorer for Microsoft Active Directory, which is even available in Veeam Backup FREE Edition! Veeam strives to provide valuable tools that help make IT professionals’ lives easier. It’s in our blood.