Third-party software that interacts with VMware vCenter must store credentials somewhere. These credentials are the target of attackers as they often provide high privileges on one of the central components of a busines IT infrastructure. This blog post shows how a “least privilege model” implementation with Veeam Backup & Replication can work.
To set realistic expectations: the protection of the backup server is key. If an organization lacks capabilities to secure the Windows Active Directory domain, then a locked down standalone system in a workgroup is the better solution. Reducing vCenter permissions to a “high security” level is not a silver bullet, as it also reduces functionality.
Veeam Backup & Replication as backup software is just an example. The same concept applies to any other software that interacts with vCenter. This could be any other backup software, deployment software, PowerShell scripts, a monitoring software, or other types of management software. All these applications store credentials and an attacker could get them. Possible ways, for example, are directly from RAM, from an encrypted file/database or simply from clear-text password files.
Overview: How to secure in three steps
In theory, it’s an easy concept how to implement reduced access permissions for vCenter. The following three steps will be discussed in detail later:
- Create a vCenter role that only has minimum permissions that are required for backup
- Have a dedicated user for backup (administrator@vsphere.local must not be used for obvious reasons). That can be a local vCenter user, or from a directory service.
- Add a permission for the user to vCenter. In most cases, the permission is assigned at vCenter level.
The main challenge is defining the role. Simply adding all cumulative permissions from the user guide is probably too much in many situations. Depending on the level of security you need, multiple roles are required for backup and restore of virtual machines. There are also different requirements for different backup modes that will be discussed in the next section.
Finding the permissions for the new role
The Veeam Backup & Replication user guide lists all required permissions for all possible operations in the Required Permissions for VMware vSphere section. For backup, different permissions are required depending on the backup mode. “Hot-Add” or “Virtual Appliance” mode requires “remove disk” permissions. This requirement limits the backup modes to NBD and direct SAN, because the “remove disk” permission would give an attacker the chance to delete disks from production.
Examples like the one above lead to the biggest challenge in defining a role. On the one hand, functionality is needed for proper operations. On the other hand, some permissions can be used for malicious activities. As a result, some customers define a different role for restore and assign it only “on-demand” (for example for full-VM restores).
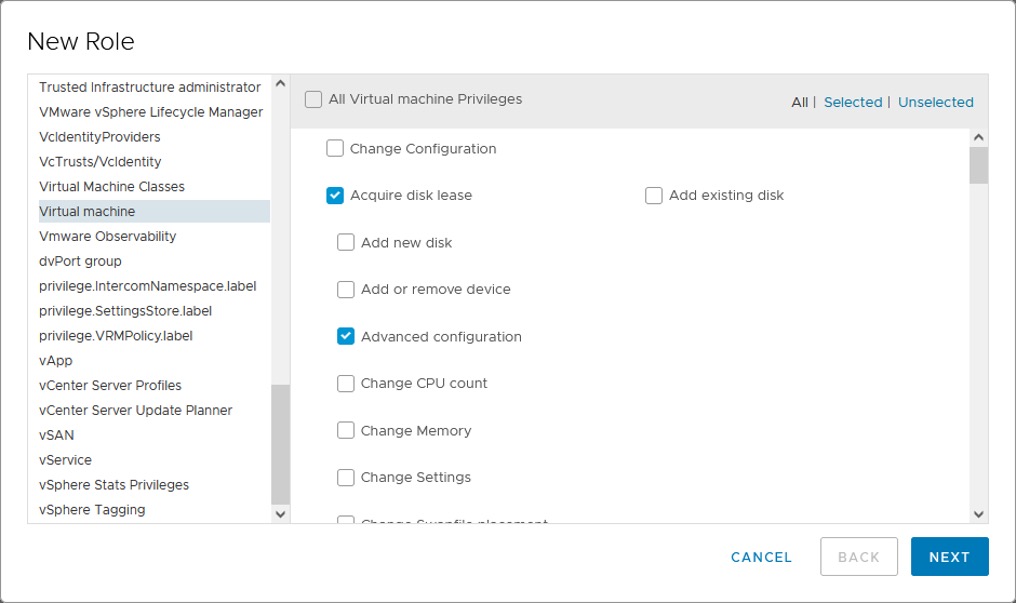
Configure a role in vCenter
The configuration of roles is available in the Main menu -> Administration -> Access Control -> Roles section in the vCenter web client. Use the “plus” sign to create a new role and assign the required permissions according to the needs of your role.
Once all permissions have been assigned, give the role a name and finish the wizard.
Add a user to vCenter
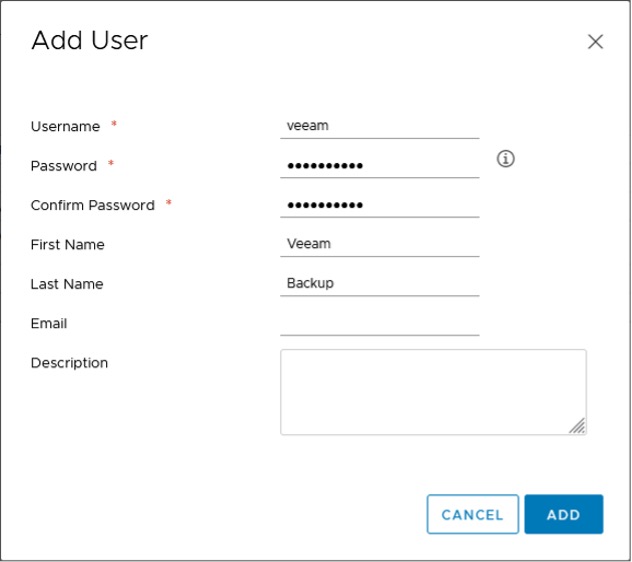
Once the role configuration is done, a user that will be used in Veeam Backup & Replication is needed. If a directory service is already configured for vCenter, this step happens outside vCenter. In this example, a local user “@vsphere.local” is used. Again, in the main menu, go to Administration -> Single Sign On -> Users and Groups. In the “Users” section, select “vsphere.local” as Domain. Then use the “Add” button to add a new user.
Insert all needed information and finish the wizard.
Assign permission to a vCenter resource
The final step on the vCenter side is assigning the permissions. In most scenarios, permissions are assigned globally. If you plan to assign at lower levels (e.g., per data center), you might still need to assign permissions on the root level depending on which features you are using.
In the configuration window, assign the user to a role and “Propagate to children.” By doing that, the permissions will also be applied to all components (VMs, datastores, networking, etc.).
Once that’s finished, you can check the reduced permissions by logging into the vSphere web client with the credentials of the Veeam backup user. Many operations are forbidden now.
Configure Veeam Backup & Replication with reduced permissions
In the steps before, all permissions were configured and assigned on the vCenter side. Now Veeam Backup & Replication needs to be configured to use the account with the reduced permissions. To do that, go to Backup Infrastructure -> Managed Servers -> VMware vSphere and edit (or add) your vCenter.
Summary
Many products that interact with VMware vCenter can work without administrator permissions. Veeam Backup & Replication can easily be used with reduced permissions on vCenter to increase security.
If you’d like to learn more about security-related topics around Veeam, please have a look at “5 Ransomware Protection Best Practices” whitepaper by Rick Vanover and Edwin Weijdema and Veeam Hardened Repository blog.