Key Takeaways:
- Ransomware threats are growing: attacks are up year-over-year, with backup repositories targeted in 89% of incidents.
- Cloud workloads are at risk: nearly half of businesses store data in a public cloud, which creates a wider attack surface.
- Veeam’s in-line malware scanning detects threats during backups and restores, flagging compromised files early.
- Daily malware definition updates: Veeam’s protection stays current with automatic updates and customizable rules.
- Backup integrity is critical: marked restore points as clean or infected help admins choose safe recovery points.
- Compliance and audit readiness: detailed reporting supports regulatory compliance and audit trails.
- Proactive protection strengthens resilience: Veeam’s malware detection tools protect cloud, virtual, and physical workloads, providing confident recovery after a cyber incident.
How Veeam’s Malware Protection Safeguards Your Cloud Workloads
Ransomware attacks are surging, with cybercriminals targeting cloud-based workloads to encrypt critical data, disrupt operations, and demand hefty ransoms. The Veeam 2025 Ransomware Report revealed that 89% of attacks target backup repositories, making robust data protection a business imperative. Veeam’s advanced malware detection and backup solutions empower organizations to secure cloud workloads, ensure rapid recovery, and maintain business continuity.
The Growing Threat to Cloud Workloads
Cloud adoption is accelerating, with 60% of organizations storing data in public clouds, according to Network. While the cloud drives digital transformation, it also expands the potential attack surface. Sophisticated tactics like double extortion, where attackers steal and encrypt data, amplify the risk. The Allianz Risk Barometer 2025 ranks cybercrime as the top business risk for 38% of large and medium-sized companies, with ransomware attacks up 143% from Q1 2022 to Q1 2023 according to Akamai.
Cybercriminals often target backups to maximize disruption, knowing that compromised backups can hinder recovery. Without clean, secure backups, organizations face prolonged downtime, financial loss, and reputational damage. A multi-layered defense that combines proactive threat detection and immutable backups is essential to protect your cloud environment.
Veeam’s Multi-Layered Malware Protection
Veeam Backup & Replication delivers cutting-edge malware detection to safeguard cloud workloads. By integrating real-time scanning, behavior analysis, and secure recovery options, Veeam ensures your data remains resilient against evolving threats. Here’s how:
1. In-Line Malware Scanning
Veeam’s in-line scanning analyzes data during backup and restore processes by flagging suspicious files in real time. Key features include:
- File system activity analysis: Detects malicious file extensions, renamed files, or unusual deletions by using over 4,000 indicators of compromise (IoCs). Daily updates ensure protection against zero-day threats.
- Inline entropy analysis: Identifies encryption patterns by analyzing file randomness and triggering alerts for ransomware-like behavior (e.g., a spike from 10% to 30% encrypted data).
2. Immutable Backups
Immutable backups are locked and unchangeable to protect against malicious encryption. Veeam recommends the 3-2-1-1-0 rule:
- Three backup copies on two different media.
- One copy off-site and one air-gapped.
- Zero errors verified for reliable recovery.
3. Compliance and Governance with SIEM Integration
Veeam enhances compliance and governance by integrating with Security Information and Event Management (SIEM) systems, providing centralized monitoring and reporting. Key aspects include:
- Veeam SIEM integration: Seamlessly connects with leading SIEM platforms (e.g., Splunk, Rapid7, etc) to aggregate and analyze security events and enable proactive threat detection and audit-ready reporting.
- Policy enforcement: Supports adherence to regulatory standards (e.g., GDPR, HIPAA) by maintaining immutable audit logs and tracking data access.
- Alerting and incident response: Real-time alerts from SIEM integration allow rapid response to potential threats and ensure compliance with governance frameworks.
This approach ensures a clean restore point, even if primary systems are compromised.
By embedding Veeam’s malware detection into your cloud infrastructure, you gain proactive threat detection, enhanced security, and compliance assurance. Daily activity reports and instant alerts keep you informed, while integration with SIEM tools like CrowdStrike Falcon, Microsoft Sentinel, Splunk, Rapid7 and many more provide comprehensive visibility.
Setting Up Veeam’s In-Line Scanning for AWS and Azure
Securing cloud workloads is straightforward with Veeam:
- Create a protection group: Enter AWS or Azure credentials, select the region, and choose cloud machines as the protection group type.
- Select workloads: Pick individual machines or use tags for scalability. Veeam can auto-assign necessary permissions for AWS roles.
- Enable scanning: Activate entropy and file system analysis in global settings. Suspicious detections appear in job properties, inventory, or Syslog if event forwarding is enabled.
To secure your cloud workloads with Veeam’s in-line scanning, follow these steps:
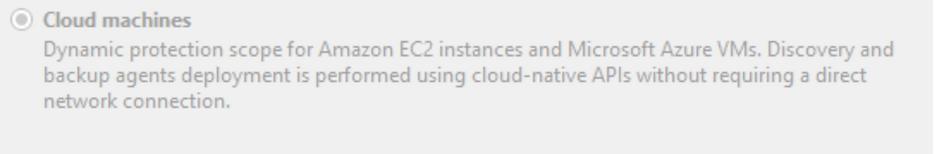
Create a Protection Group
Enter the credentials for your AWS or Azure account subscription and select the region of the machines you want to protect. Make sure you choose cloud machines as the protection group type, which involves using specific agents for cloud workloads.

Make sure you choose cloud machines for your type of protection group, as these are special kinds of agents.
Select Machines
You can select machines individually or use tags to cover cloud workloads. For AWS, a role with specific permissions needs to be attached. Veeam can automatically create and assign these roles, which simplifies the process for organizations with numerous workloads.

A role with the following cloud permissions must be attached to the instances you want to protect in the case of AWS. Veeam can automatically create and assign those roles, which simplifies the process for organizations with hundreds or thousands of workloads.

Enable Scanning Features
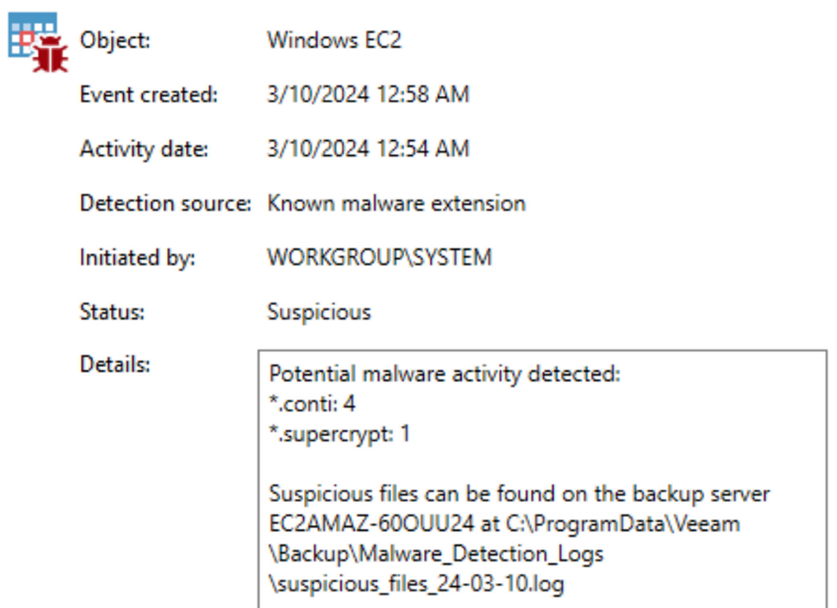
Enable both entropy and file system analysis in global settings. Once the backup job is created, in-line malware scanning occurs by default. Suspicious detections will be shown in the job properties, inventory menu, and Syslog server if event forwarding is enabled.
Stay Ahead of Ransomware with Veeam
As ransomware grows more sophisticated, proactive protection is non-negotiable. Veeam’s in-line scanning and immutable backups deliver real-time threat detection, secure recovery, and data resilience. Don’t let cybercriminals hold your business hostage; act now to safeguard your cloud workloads.
Learn how Veeam protects multi-cloud environments today.
Frequently Asked Questions
- What is Veeam malware detection?
Veeam malware detection is a multi-layered security feature within Veeam Backup & Replication that scans backup and restores for malware, ransomware, and suspicious activity. It uses advanced analysis and threat detection techniques. - How does Veeam detect malware in cloud backups?
Veeam detects malware through in-line scanning file system activity and entropy analysis by using cloud agents. These tools identify encrypted files, unusual behavior, and known malware patterns. - What is in-line malware scanning?
In-line malware scanning analyzes data in real time during backup and restore operations and flags infected files before they can compromise backup integrity or restoration processes. - How does Veeam’s entropy analysis work?
Veeam’s inline entropy analysis measures file randomness during backups to detect encryption patterns that are common in ransomware, triggering alerts when anomalies are found. - Can Veeam help protect cloud workloads like AWS and Azure?
Yes. Veeam enables in-line scanning for AWS and Azure workloads by creating protection groups, assigning roles with necessary permissions, and activating scanning features such as entropy and file system analysis. - How often does Veeam update its malware definitions?
Veeam updates malware definitions daily, ensuring that detection methods remain effective against emerging threats and zero-day vulnerabilities. - Why is backup malware detection important?
Detecting malware in backups prevents restoring compromised data, ensures clean recovery points, and strengthens an organization’s overall cyber resilience and compliance posture.
