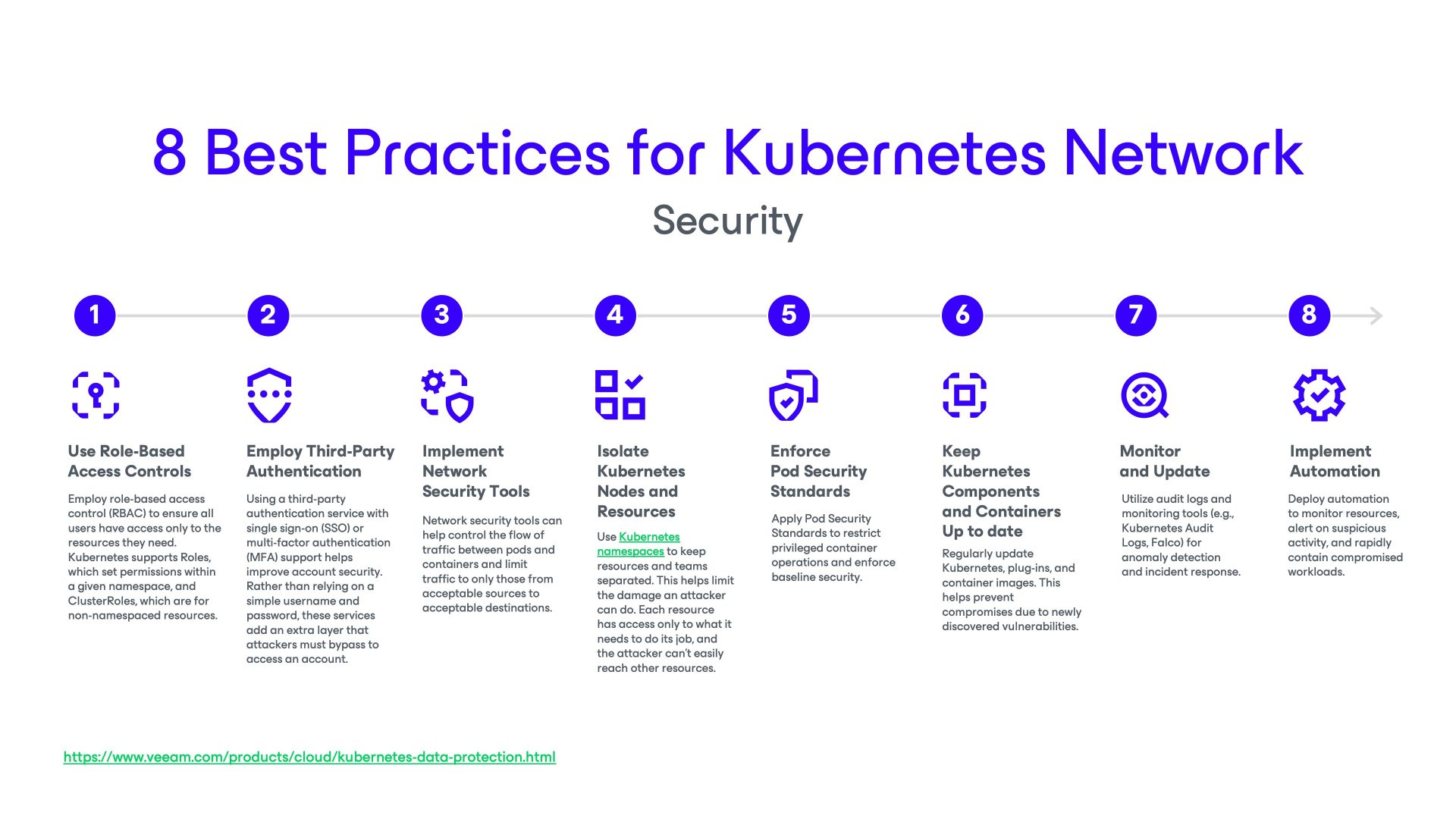
Key Takeaways:
- Network segmentation and policies are essential: Kubernetes networking should be tightly controlled using namespaces and network policies to restrict lateral movement and minimize the impact of potential breaches.
- Choose and configure CNI plugins wisely: Not all CNI plugins offer the same level of network policy enforcement or security features. Select a CNI that aligns with your security and scalability needs and verify its support for the security controls you require.
- Service meshes enhance security and observability: Integrating service meshes (such as Istio or Linkerd) with Kubernetes provides advanced security features like mutual TLS and fine-grained traffic control-at the application layer.
- Continuous monitoring and timely updates are critical: Regularly update Kubernetes components and container images and use monitoring tools and audit logs to detect and respond to suspicious activity.
- Backup and disaster recovery (DR) are integral to security: Complement network security controls with a robust data resilience solution like Veeam Kasten to ensure rapid recovery and continuity in the event of a security incident, breach, or data loss.
Kubernetes has become the go-to solution for container orchestration, enabling organizations to efficiently deploy, manage, and scale containerized applications. However, as Kubernetes environments grow in complexity, securing them becomes increasingly challenging. This article covers some fundamental considerations, the role of Container Network Interface (CNI) plugins, and best practices for scaling secure networks.
Understanding Kubernetes Networking
Kubernetes networking is foundational to cluster management since it enables communication within and between pods, services, and external systems. Secure networking is crucial to preserve core concepts, components, challenges, and best practices for Kubernetes networking, including how Veeam Kasten enhances your environment’s overall security posture.
In a Kubernetes cluster, every pod is assigned a unique IP address for pod-to-pod communications, and every node also has its own IP address. This architecture allows pods to communicate with each other directly across the cluster without requiring Network Address Translation (NAT). Kubernetes Services, which are logical abstractions that group sets of pods, also have their own IP addresses and can be exposed applications to external traffic.
Kubernetes Networking Components
Kube-Proxy
Kube-proxy manages networking rules on each cluster node and handles service discovery and load balancing for TCP, UDP, or SCTP streams. While Kubernetes abstracts much of the underlying network management, the security of the node-level networking layer remains essential for controlling access and preventing lateral movement in the event of node compromise.
Container Network Interface (CNI) Plugins
CNI plug-ins provide a mechanism for assigning IP addresses and configuring network connectivity for pods. Popular CNIs include:
- Calico: Robust support for network policies, IP whitelisting, micro-segmentation, and encryption.
- Flannel: Simple overlay networking, but limited network policy enforcement.
- Weave Net: Encrypted pod-to-pod communications and automatic topology discovery.
- Cilium: Uses eBPF for fine-grained security, advanced policy enforcement, and deep visibility.
CNI and Static IPs
While Kubernetes typically assigns dynamic IPs to ephemeral pods, static IPs are achievable through services (e.g., ClusterIP, NodePort, LoadBalancer) and StatefulSets, which support scenarios that require predictable addressing.
Service Meshes
Service meshes automate the discovery and secure communication of services at the application layer by adding features like mutual TLS, traffic management, and detailed observability. Kubernetes integrates with third-party service meshes such as Istio and Linkerd. These tools complement CNIs by introducing zero-trust networking, secure service discovery, and advanced inter-service controls.
Why is Kubernetes Network Security Important?
The nature of Kubernetes containers provides some security advantages, since application containers are replaced entirely when an update is due rather than being patched. This makes version control a simpler process. However, the dynamic, distributed nature of Kubernetes clusters brings its own challenges because the runtime environment and network are in a constant state of flux.
Some vulnerabilities and security challenges to be aware of include:
- Untrusted container registries: Mistakenly pulling from an untrusted registry could lead to you installing malware or a backdoor onto your systems.
- Bloated images: Containers should include only the bare minimum needed to run the application. Adding unnecessary libraries, shells, or packages increases the attack surface for malicious actors.
- Excessive privileges: Granting more privileges than required or mounting secrets that aren’t needed for that container increases the damage an attacker could do if they compromised the container.
- Lack of segmentation: Use namespaces to separate resources and prevent a malicious actor from gaining access to other applications or resources.
Implementing Network Policies for Security
By default, pods in a Kubernetes cluster can communicate freely. Network policies allow administrators to define rules that govern which pods can communicate on which ports, thereby achieving segmentation and access control.
Note: Network policies are only enforced if supported by the chosen CNI plug-in.
Here’s an example of a simple network policy that allows communication between pods with the label “frontend” and the service “backend”:
yamlCopy code
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: frontend-to-backend
spec:
podSelector:
matchLabels:
app: frontend
ingress:
– from:
– podSelector:
matchLabels:
app: backend
ports:
– protocol: TCP
port: 80
This network policy allows pods with the label “app: frontend” to communicate with the service “backend” on port 80.
Achieving Network Segmentation and Isolation
Network segmentation divides the cluster into smaller, isolated subnets, while network isolation restricts communication between network segments. In Kubernetes, this is achieved through a combination of namespaces and network policies. For example, you might:
- Create separate namespaces for development, testing, and production.
- Use network policies to restrict traffic between these namespaces.
This limits the impact of security incidents and enforces least-privilege access.
Real-World Kubernetes Networking Security Incidents
Kubernetes networking security incidents can have severe consequences. In one case, an attacker exploited a misconfigured Kubernetes cluster to mine cryptocurrency. The attacker then gained access to the cluster by exploiting an insecure API server and using it to deploy malicious containers. This incident highlights the importance of securing your Kubernetes networking, implementing network policies to restrict access, and having a disaster recovery policy to turn to if the worst should happen.
Conclusion
Securing Kubernetes networks is vital for protecting your applications and data. By implementing network policies, achieving network segmentation and isolation, and monitoring your network for security incidents, you can ensure the security and integrity of your Kubernetes environment. Using tools such as Veeam Kasten, a purpose-built Kubernetes data management platform, you can further enhance your Kubernetes security strategy by providing data backup, recovery, and application mobility across your clusters.
With Veeam Kasten, teams achieve radical resilience against ransomware attacks.
FAQs
1. What is Kubernetes networking in simple terms?
Kubernetes networking is the system that connects applications, services, and resources inside a Kubernetes cluster and to the outside world. It ensures that containers, called pods, can communicate with each other, with other services, and with users or systems outside the cluster.
2. How do pods communicate with each other in Kubernetes?
In Kubernetes, every pod gets its own IP address, and all pods within the cluster can talk to each other directly using that IP, without the need for network address translation. This flat network model is managed by a Container Network Interface (CNI) plug in, which handles routing and connectivity between pods across different nodes.
3. What are Kubernetes network policies and why are they important?
Kubernetes network policies are rules that control which pods can communicate with each other and with external endpoints. They are important because, by default, all pods can freely exchange traffic, which can expose workloads to unnecessary risk. Network policies help enforce zero‑trust principles by allowing only the communications that are explicitly permitted.
4. Which CNI plugins are most popular for Kubernetes networking?
Some of the most popular Kubernetes CNI plugins are Calico, Flannel, Cilium, and Weave Net. Calico is known for strong network policy enforcement, Flannel for simplicity and ease of setup, Cilium for advanced security and observability, and Weave Net for automatic network topology management. The right choice depends on your performance, security, and scalability needs.
5. How do you secure Kubernetes network traffic?
You can secure Kubernetes network traffic by implementing network policies to restrict pod‑to‑pod communication, encrypting data in transit using TLS, and segmenting workloads based on trust levels. Using a CNI plugin that supports encryption and enforcing RBAC for network configurations also helps reduce the risk of unauthorized access.
6. What are common Kubernetes networking challenges and how do you solve them?
Common Kubernetes networking challenges include DNS resolution issues, misconfigured network policies that block legitimate traffic, and latency caused by inefficient routing. These can be solved by using a reliable CNI plug in, thoroughly testing network policies before deployment, monitoring traffic with observability tools, and optimizing cluster topology for performance.