Clone Job Fails Due to Security Context Constraints (SCC) Issue
Challenge
Cloned-restore jobs time out and eventually fail because an application's security context provides permissions in the original application namespace. This results in the application's pod being in a non-running state.
Example:
Namespace = quay-enterprise SCC (during deployment) = anyuid SA = default Cloned namespace = quay-enterprise-restore
$ oc logs postgres-856bf449fb-p7r6t chmod: changing permissions of '/var/lib/pgsql/data/userdata': Operation not permitted $ oc get pods NAME READY STATUS RESTARTS AGE postgres-856bf449fb-p7r6t 0/1 CrashLoopBackOff 5 3m40s quay-enterprise-app-dff657895-nvh8n 1/1 Running 1 3m40s quay-enterprise-config-app-74f5cd5558-94w6d 1/1 Running 0 3m40s quay-enterprise-redis-65fb758bff-l2c8l 1/1 Running 0 3m40s
Cause
Like RBAC (Role-Base Access Control) resources control user access, administrators can use Security Context Constraints (SCCs) to control pod permissions. Veeam Kasten for Kubernetes allows applications to be restored in-place (overwriting) or cloned-restore (to a different namespace) on the same cluster.
Generally, an SCC is added to a Service Account (SA) in the application namespace. Depending on how an application is configured with SCC permissions, cloned-restores may fail because application resources are returned to a new namespace.
Solution
- Identify the SCC used for this application in the appropriate Service Account and find the serviceaccount that is being used by the workloads.
Example:
- Run the following command to patch the default Service Account:
- Deploy the application into a target namespace and use K10 to recover all data:
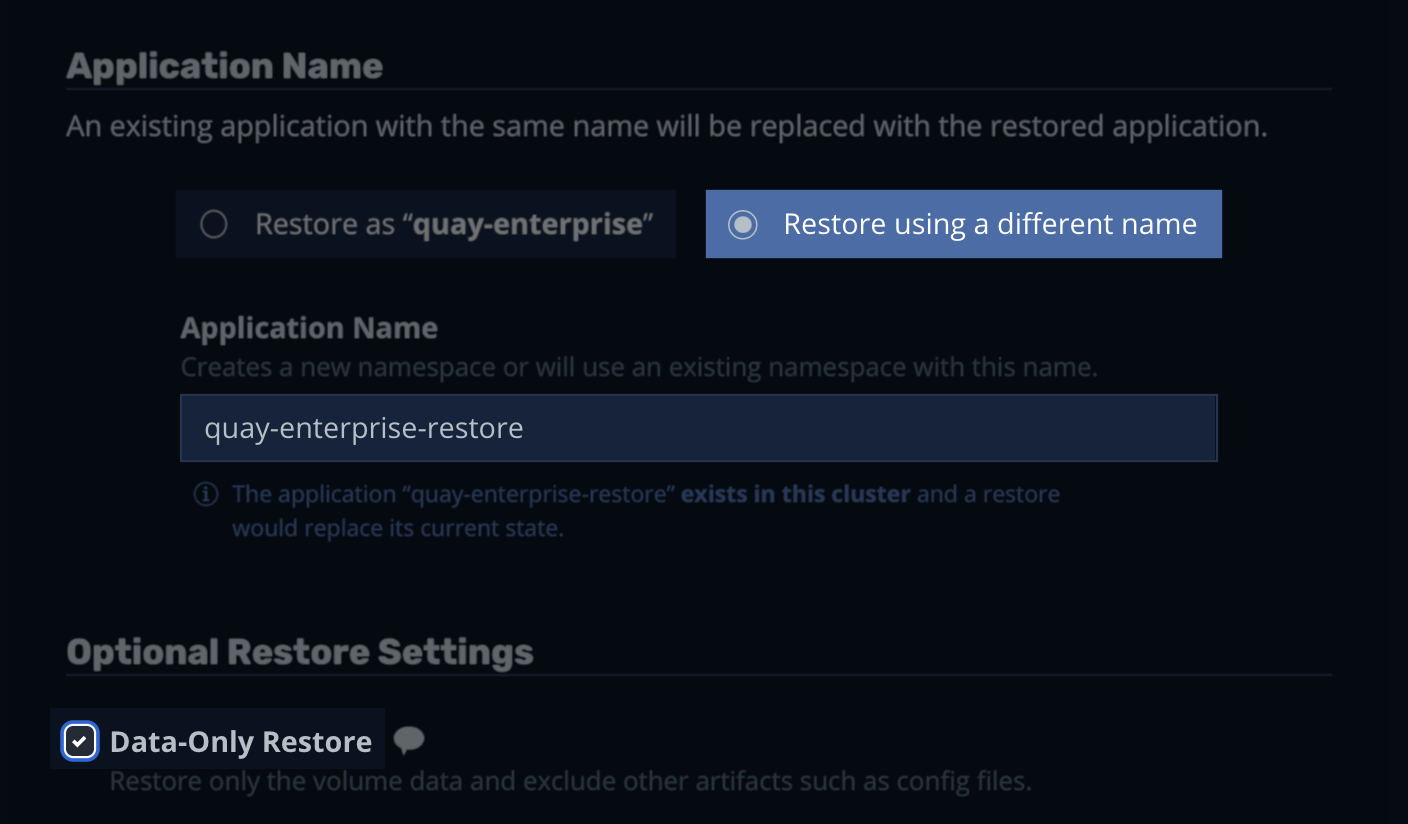
- Go to the K10 dashboard --> Applications
- Select restore under the original namespace (quay-enterprise)
- Select the restorepoint
- Click Restore using a Different Name
- Enter the name: quay-enterprise-restore
- Select Data-Only Restore --> Restore
If this KB article did not resolve your issue or you need further assistance with Veeam software, please create a Veeam Support Case.
To submit feedback regarding this article, please click this link: Send Article Feedback
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
Spelling error in text
KB Feedback/Suggestion
This form is only for KB Feedback/Suggestions, if you need help with the software open a support case