For the last few years, I have spent a lot of effort along with others at Veeam carefully watching the industry behavior when it comes to ransomware and its devasting impact it can have on an organization. I’ve also spent a lot of time putting together a lot of great works in the form of whitepapers, webinars and other assets to get the word out. For example:
- A recap of Veeam’s ransomware capabilities
- A deep and dive on the Veeam hardened repository
- From a monitoring perspective, Veeam ONE can help to detect and respond to ransomware
The important takeaway is that today, it is easier than ever to have backup copies ready to restore from ransomware with Veeam.
What are the Immutability Options?
I say there are more options than ever, but in fact, I’ve made a word for a backup copy that is in a state where recovery from ransomware is favorable: a copy on an ultra-resilient media. Ultra-resilient is a media type that is offline, air-gapped or immutable. Some media can in one state be all three at once, take for example WORM tape media when removed from the library.
Today, it doesn’t have to be cloud or tape only to get these levels of data comfort, there are more ways than ever to have ultra-resilient backup copies. Here’s the quick list:
- Tape media, especially when media is removed from library or WORM
- Veeam Cloud Connect backups with Insider Protection
- Rotating media or removable drives that are offline
- Immutable backups that are in a cloud target that is Veeam-Ready Object with Immutability
- The Veeam hardened repository
What is Double-Play Immutability?
This is a way of implementing the 3-2-1 Rule with exceptional modern standards, even doing better than the 3-2-1-1-0 Rule. Check out a recent blogpost I did explaining the 3-2-1 and 3-2-1-1-0 Rule.
Double-play or even triple-play Immutability is where the implementation has two backup copies that are ultra-resilient. Let’s walk through a few examples so you can see both how easy this is and how resilient this is against ransomware. Each example has the explicit ultra-resilient copies identified with a number of first copy, second copy, third copy, etc.
Double-Play: Hardened Repository and Veeam-Ready Object with Immutability
This configuration would be leveraging the following configuration:
- One Scale-out Backup Repository configured as followed:
- One extent being a hardened repository
- The capacity tier targeting a Veeam-Ready Object with Immutability provider (AWS S3 for example)
- Copy mode configured
This is a robust configuration visualized in the diagram below:
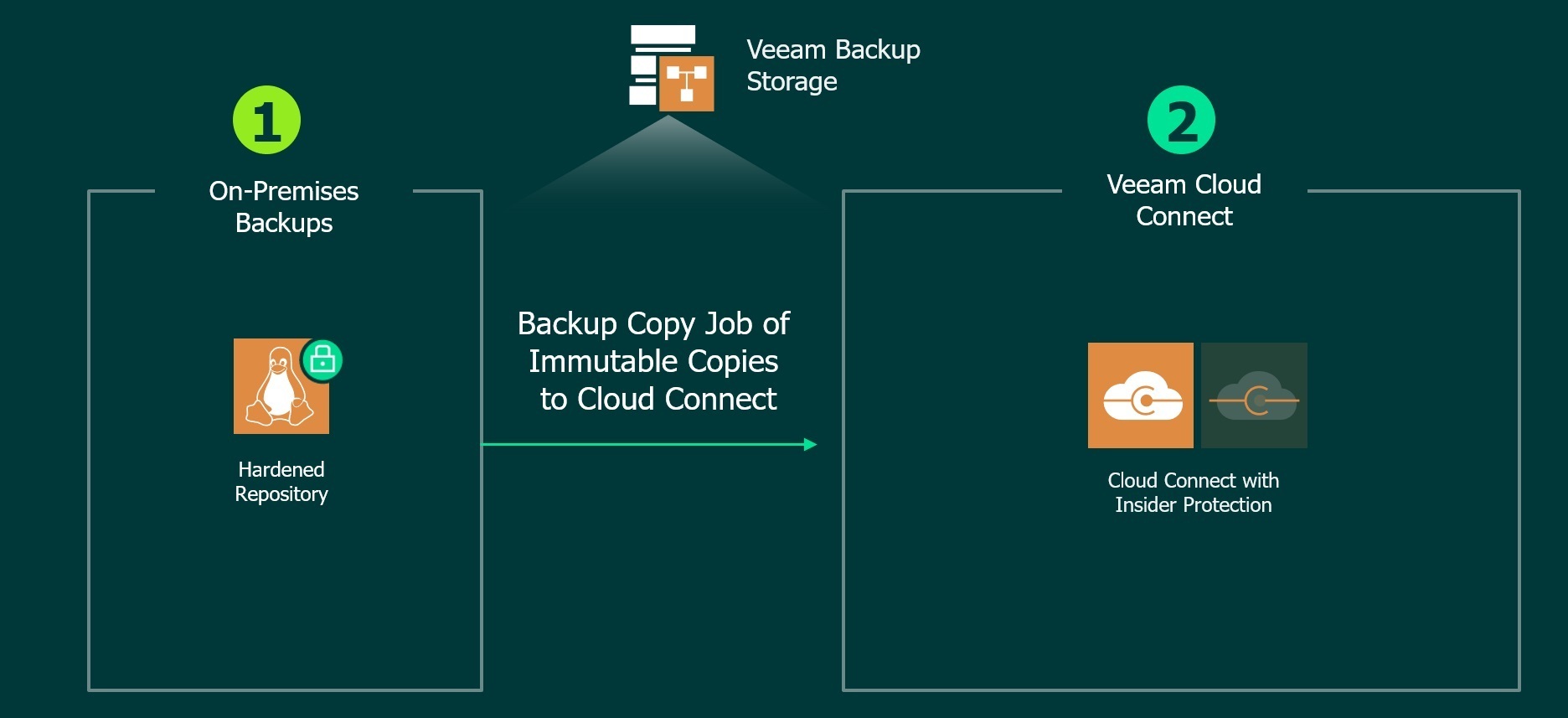
Double-Play: Hardened Repository and Veeam Cloud Connect Backup with Insider Protection
This configuration would be leveraging the following configuration:
- One backup repository being a hardened repository
- A backup copy job to a Veeam Cloud & Service Provider partner offering Cloud Connect with Insider Protection
This is a robust configuration visualized in the diagram below:
Triple-Play: Hardened Repository and Veeam-Ready Object with Immutability and Tape Jobs
In baseball, a triple-play is a thing of beauty — it’s just as awesome if leveraging the following example configuration:
- One Scale-out Backup Repository configured as followed:
- One extent being a hardened repository
- The capacity tier targeting a Veeam-Ready Object with Immutability provider (AWS S3 for example)
- Copy mode configured
- A backup to tape job configured as well
This is a robust configuration visualized in the diagram below:
You can get the point that between the capabilities of the backup copy job (which there is a whole double-play immutability story there with the hardened repository site-to-site), the value of Veeam Cloud & Service Provider partners and the Veeam Ready Object with Immutability partners, it becomes very easy to add the second or third immutable copy.
Adding ultra-resilient copies without complete reconfiguration of your backup infrastructure
The examples above and some of the other ones that may make sense to you do not have to be a heavy lift to get started. This is where the Backup Copy Job and the Scale-out Backup Repository can help you out big time!
- You can configure backup copy jobs to a newly created hardened repository or a Cloud Connect Backup target without reconfiguring your backup jobs
- You can create a Scale-out Backup Repository and add your existing repositories to it to incorporate the copy mode as well as introduce the hardened repository with seal mode for the existing repositories.
It’s somewhat ironic that the Scale-out Backup Repository can play such a critical part in this double-play immutability story. It was initially designed to handle the situation of a backup target being full, then it was expanded to accommodate the lower cost opportunities by policies for object storage — here it is being the hero for ransomware resiliency.
Absolute Portability Drives Complete Recovery
What is really powerful here is that each copy is absolutely portable and self-describing. You only need to have the password the backups were encrypted with as part of the Veeam backup job. No part of the Veeam infrastructure is required, no servers on premises or in the cloud are needed either. These backup copies are each complete and fully recoverable only from the data they are. Additionally, there is no persistent connection back to the Veeam infrastructure to protect these copies in a ransomware scenario.
When it is this easy to have multiple ultra-resilient copies of backup data, there really is no reason not to have one, two or even three copies. Having copies that are ultra-resilient is by far the strongest best practice to drive high confidence for data recovery in a ransomware scenario.
What do you think about double-play or triple-play immutability? Share your comments and the configurations you would recommend below.