Cyberattacks continue to accelerate in scale and sophistication, and backup infrastructure has become a priority target. Threat actors understand that compromising backup environments can limit recovery options, conceal malicious activity, and increase pressure during extortion attempts. As a result, organizations need deeper visibility into servers and systems that support backup and recovery.
Recon, powered by Coveware by Veeam, helps organizations achieve this visibility. It analyzes activity across Veeam Data Platform servers, detects known adversary behaviors that other security tools might miss, and maps those behaviors to the MITRE ATT&CK framework. With lightweight deployment and contextual analytics, Recon enhances the resilience of the entire backup environment.
What’s New: Enhanced Visibility and Faster Investigation
The latest release of Recon introduces several upgraded designs to make threat detection more intuitive and the investigation process faster. These enhancements strengthen visibility across the backup environment and improve how IT and security teams triage, analyze, and respond to suspicious activity.
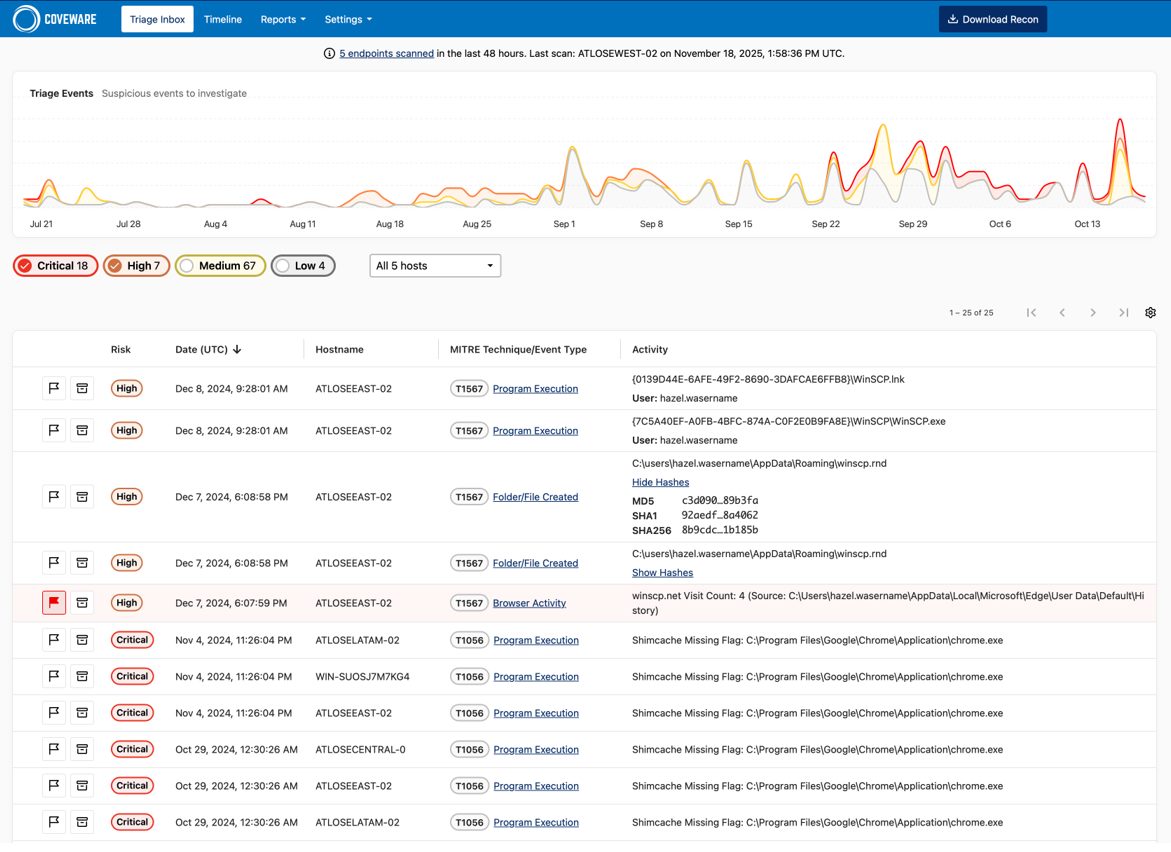
Triage Inbox: A Unified View of Findings
The new Triage Inbox consolidates all Recon findings into a single, streamlined dashboard. Analysts can quickly sort, filter, and prioritize suspicious activity without switching screens or reviewing individual scan reports.
Each finding includes a severity score, behavioral context, and associated MITRE ATT&CK tactics. Users can flag findings for follow-up, archive completed investigations, and filter results by time and risk level. This unified workflow reduces investigation time and gives teams a clearer understanding of what’s happening across their Veeam environment.
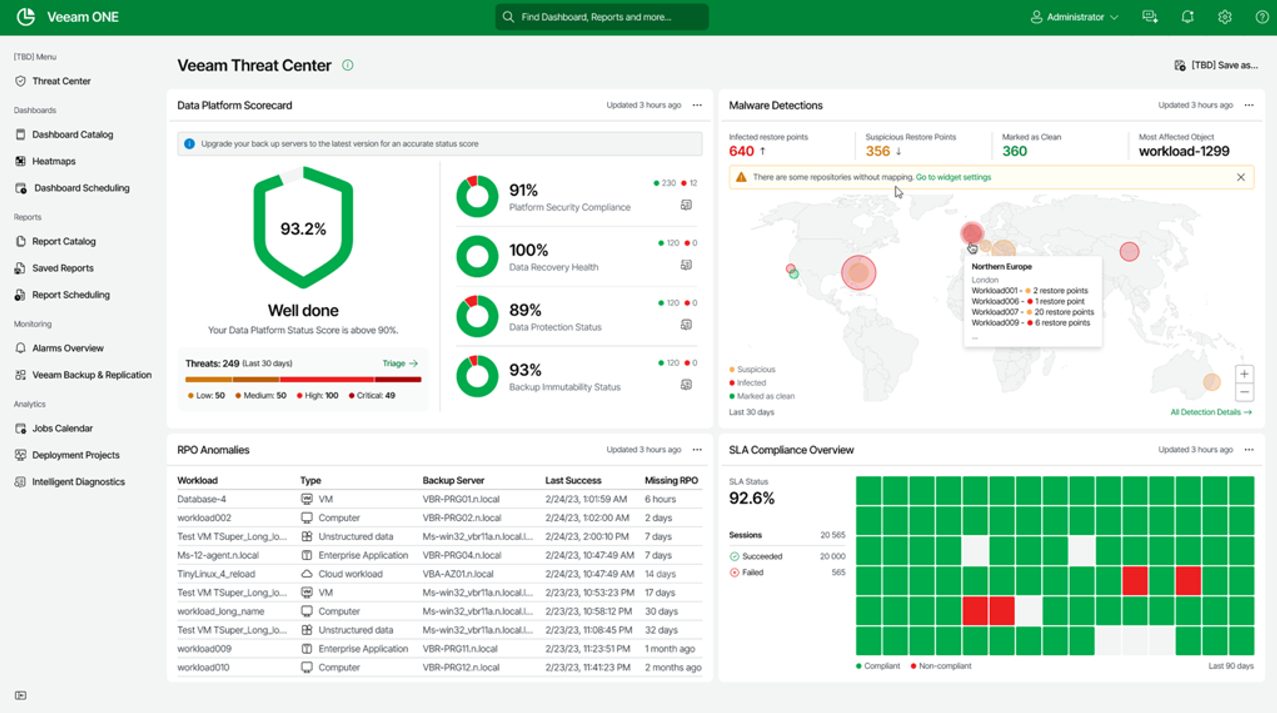
Integration with Veeam ONE and Microsoft Sentinel
Recon findings now feed directly into Veeam ONE Threat Center and Microsoft Sentinel, giving organizations consistent visibility across both their IT operations and SOC.
- In Veeam ONE, Recon findings join operational insights, configuration checks, and backup monitoring to provide a holistic view of your environment health and security.
- In Microsoft Sentinel, analysts can correlate Recon detections with broader security telemetry, including identity activity, endpoint events, and network behavior.
These integrations eliminate manual data handoffs and make it easier for teams to understand the full lifecycle of suspicious activity, from initial behavior in the backup environment to downstream impact across production systems.
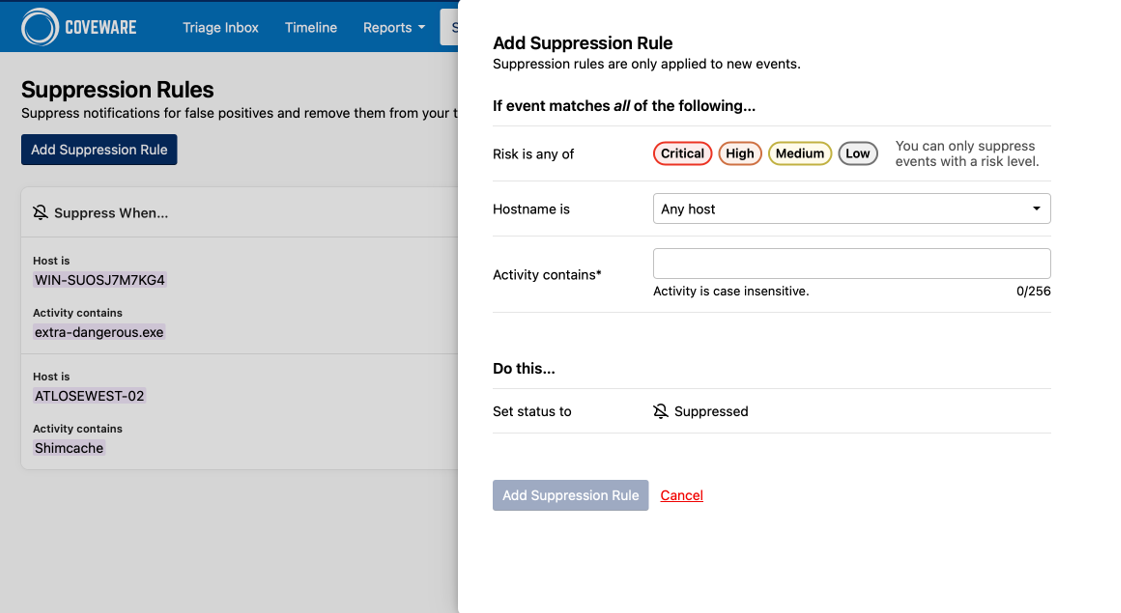
Limit Noise with Suppression Rules and Archiving
To reduce alert fatigue and maintain cleaner workflows, the latest release of Recon includes suppression rules and archiving capabilities.
- Suppression rules hide alerts triggered by known or expected activity to help teams focus attention on true anomalies.
- Archiving allows users to remove findings that have already been reviewed or resolved, keeping your Triage Inbox organized and manageable over time.
These enhancements streamline daily operations and ensure that analysts stay focused on the findings that matter most.
Additional Capabilities That Strengthen Detection
Beyond the new features, Recon continues to provide several core capabilities that enrich detection and improve visibility across the backup environment:
- MITRE ATT&CK Mapping: Recon aligns findings with the MITRE ATT&CK framework, helping teams quickly understand potential intent behind suspicious behaviors. This includes tactics such as brute force attempts, unauthorized file execution, unusual network connections, and potential reconnaissance or exfiltration activity.
- Threat intelligence from Coveware: Detection logic is continuously updated with real-world ransomware insights from Coveware. As new indicators of compromise emerge from active investigations, Recon automatically incorporates them to ensure customers stay aligned with evolving attack patterns.
- Lightweight deployment with minimal impact: Recon uses minimal system resources and operates independently from backup processes, making it safe to run across production environments. It’s simple deployment and low overhead helps organizations enhance visibility without introducing operational risk.
Getting Started with Recon
Recon is included with Veeam Data Platform Advanced and Premium Editions at no additional cost. With deeper visibility, streamlined investigation, and enriched threat context, Recon strengthens organizations’ ability to detect and respond to suspicious activity that’s targeting their backup environment. This helps teams stay one step ahead of evolving threats and reinforces the resilience of their backup and recovery strategy.
