- Veeam Data Platform
- Sovereignty, Governance & Compliance
Take Charge of Data Sovereignty
Keep data local, simplify audits, orchestrate verified recovery anywhere.
Choose a time to connect with an expert
- Sovereignty, Governance & Compliance
- Overview
- Capabilities
- Platform Editions
- Insights & Trends
Proof On Demand
Audit-Ready in Minutes
AI-generated documentation delivers audit-ready evidence of recoverability and policy compliance with no manual work required.
Built-In Data Sovereignty
Placement policies and portable backups keep data in your chosen regions while letting you recover anywhere you operate.
Tested, Trusted, Ready
Schedule testing with clear pass/fail results, approvals, and evidence ensure you can perform under real-world pressure.
Pass Audits, Avoid Penalties
Instant Audit Docs
AI generates audit-ready PDFs with test runs, signoffs, pass/fail status, and recovery points, eliminating the need for manual compilation.
Automated DR Testing
Schedule end-to-end failover tests with runbooks, change control, and approvals to prove repeatable recovery.
Compliance Gap Dashboard
Live dashboards and configuration checks highlight policy gaps, allowing you to address issues before auditors arrive.
Enforced Data Residency
Lock backups to specific regions with placement policies that guarantee sovereignty and regulatory alignment.
Portable, Catalog-Free Backups
Self-describing backups restore to any approved platform with no dependency on external catalogs or appliances.
Tamper-Proof Offsite Storage
Send copies to Veeam Data Cloud Vault for immutable, locked retention in the region you choose.
Isolated Cleanroom Recovery
Restore in a sandbox with inline malware and YARA scans to confirm data integrity before production release.
Enhanced Access Security
SAML SSO, MFA, and RBAC enforce least-privilege access across every team and workflow.
One-Click Audit Exports
Export policies, test history, and recovery outcomes in a single click for consistent, trustworthy proof.
Your Next Win



True Data Resilience
Available in three comprehensive enterprise-grade editions — our most powerful premium option delivers the complete, secure protection and best-in-class orchestration that can only be achieved with Veeam Data Platform.
FoundationFoundation
ResilienceAdvanced
ResiliencePremium
Add On
Add On
Add On
Add On
Add On
Add On
How Your Peers Stay Protected

at Scale
evidence, validates recovery, and keeps
sensitive data under control.


Audit
audit-ready docs, and meets strict governance
with less effort.

recoverability on demand.

Learn More, Protect Better
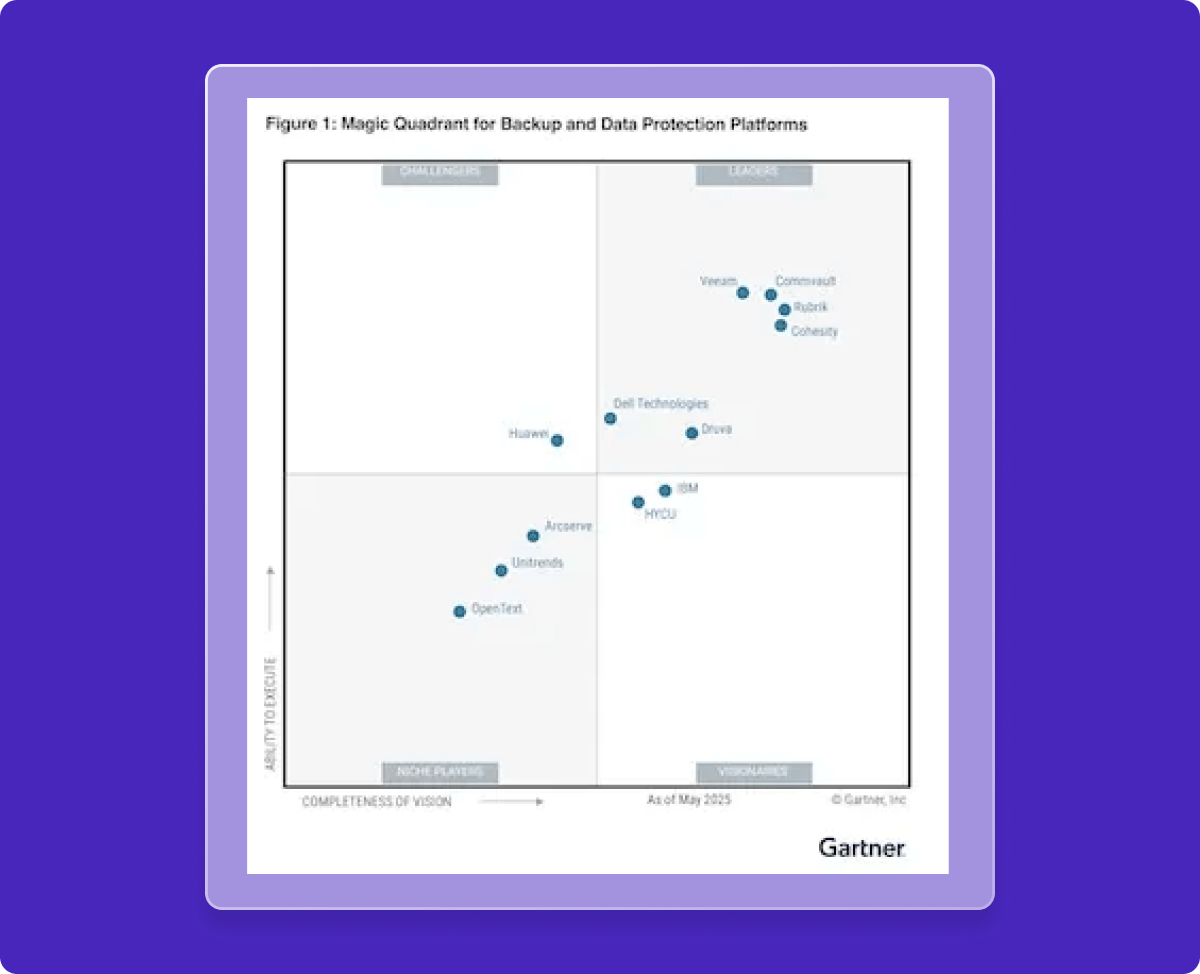
Gartner® Magic Quadrant™
Highest in Ability to Execute 2025 Gartner® Magic Quadrant™ For Backup and Data Protection Platforms
Veeam Data Resilience Maturity Model
74% of enterprises are not prepared for modern data risks. Are you?
2025 Ransomware Trends Report
We surveyed 1,300 organizations, with 900 experiencing at least one ransomware attack in the past 12 months. Here’s what we found.
VMware Customers Weigh Alternatives
Foundry and CIO.com's comprehensive survey of over 550 enterprise IT leaders provides an in-depth analysis of this landscape change.
FAQ
What does data sovereignty mean with Veeam?
How do I prove recoverability to auditors?
Can I ensure clean recovery before going back to production?
How does Veeam help with configuration and policy drift?
Do I need a special sovereign cloud to meet requirements?
What identity features support governance?
Can I export audit evidence on demand?
Radical Resilience is Our Difference
hybrid cloud and the confidence you need for long-term success.
Trends in Ransomware Protection
Our annual report with insights and strategies from thousands of IT leaders
Book Meeting
Choose a time that fits your schedule and connect with a Veeam expert to learn how to achieve data resiliency