Data security and encryption is always an important part of a data protection strategy. In other words, your backup data is a copy of your primary data, which should be treated the same in the case of security!
To keep your data safe and protect it from unauthorized access, you can leverage the various encryption capabilities and encrypted jobs provided by Veeam Backup & Replication.
When to use encryption?
There are several use cases where encryption can be useful and needs to be applied. The most common cases are the following:
- Regulatory, policy or company-specific directives to store backups in an encrypted form
- Off-site backups to a Veeam Cloud Connect provider
- Off-site backups using unencrypted tapes (hardware level)
- Off-site backup to a repository that consists of rotated drives
What can I encrypt?
The encryption algorithms are configured at the job level and the media pool level. With Veeam Backup & Replication, you can encrypt the following jobs:
- Configuration backup
- Backup job
- Backup copy job
- Backup to tape job
- VeeamZIP
Encryption standards and algorithms
The encryption standards and algorithms used by Veeam Backup & Replication are industry-standard in all cases. Veeam uses AES-256 bit encryption and public key encryption methods to satisfy those standards. Furthermore, Veeam uses the password-based key derivation function PKCS #5 in version 2.0 for creating user keys based on entered passwords. If you want to learn more about the AES-256 bit encryption and PKCS #5, head over to the Veeam Help Center where you will find all the detailed information.
Five key lessons from the field
Experience has shown that different configurations and constellations regarding the encryption of data have certain influences on the environment. Therefore, I have brought together these five key lessons and experience values that one should consider in any case if it concerns the topic encryption.
1. Use CPUs that support AES-NI for network traffic encryption
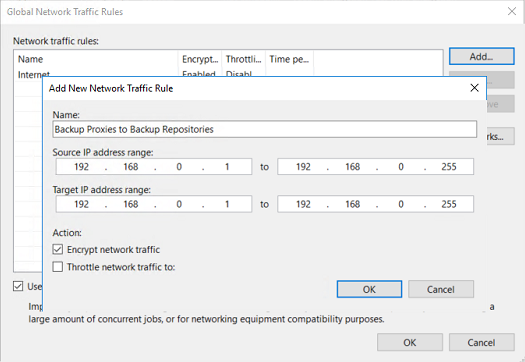
When you plan to encrypt between networks, Veeam uses in-flight encryption, whereby the encryption takes place at the source site. Network traffic encryption is known to significantly increase CPU resources during the encryption phase. A typical scenario would be to send backup data from a Veeam proxy to a backup repository. With the network traffic rules provided by Veeam throughout the general options of a Veeam Backup & Replication server, you can simply in-flight encrypt your subnets.
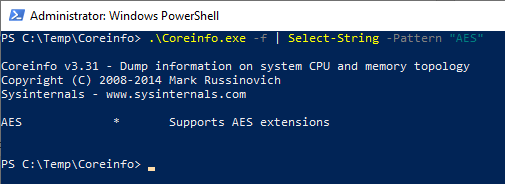
If your proxies support Intel AES-NI hardware instructions, they will be able to take the load off your CPU by using AES hardware instructions. To check if your CPU supports AES-NI, you can use the tool “Coreinfo” from the sysinternals suite. This tool reads your CPU to find all the functions it supports. Any other manufacturer-native tool like the Intel processor identification utility will do just as well. I tend to use “Coreinfo” since it’s portable.
When you plan on buying new hardware for your Veeam environment and are also planning on encrypting, make sure to select CPUs that have the AES-NI hardware instructions available as it can help you in any case.
2. Use hardware encryption when considering tape encryption
If you plan to encrypt tape media, it always makes sense to primarily use library/hardware encryption. On most libraries, this is called “application managed” encryption. If “application managed” encryption is turned on at the library, Veeam will automatically disable its software encryption mechanism, as hardware encryption has a higher priority.
Here is an example of an “application managed” encryption on an IBM TS4500 library:
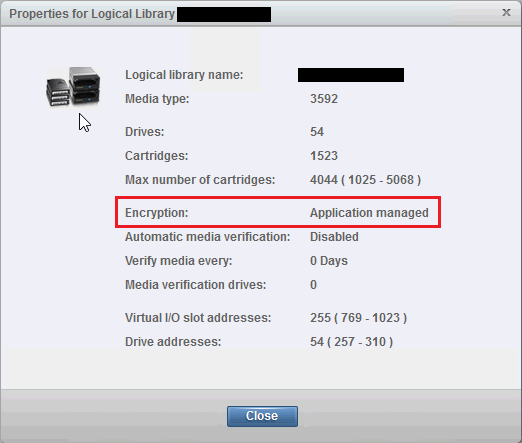
The primary advantage of using “application managed” encryption is Veeam’s ability to send the session key via SCSI commands to the tape drive which then performs the encryption itself. By using the “application managed” encryption you can perform encryption with almost no impact on the CPU of your tape server.
If “application managed” encryption is not available, Veeam will automatically fall back to software-based encryption, which also means a higher impact on the CPU because data is getting encrypted prior to writing to tape.
3. Protect and configure Veeam Enterprise Manager
The Veeam Backup Enterprise Manager plays an important part in the encryption of backups. If you have lost or forgotten your password, you can use Veeam Enterprise Manager to unlock it. Therefore, the Veeam server needs to be connected to Veeam Enterprise Manager and the password loss protection feature must be enabled (it is enabled by default, but you can disable it).
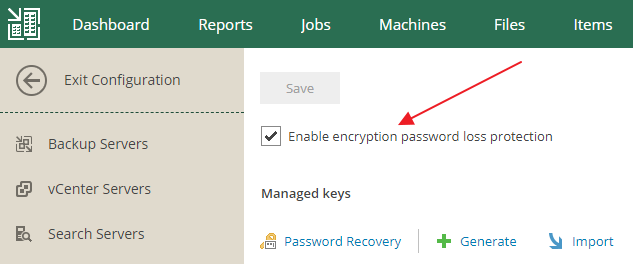
If you experience a situation where the password has been lost, you can easily unlock your data by leveraging an encryption key restore request through the corresponding wizard. The encryption request then gets verified by Veeam Enterprise Manager and you’ll get a response key that can be used to unlock the content of your data!
Ultimately, it’s extremely important to protect the Veeam Backup Enterprise Manager and the activated keysets, as these in turn serve as the basis for all encryption. Therefore, please pay attention to these two things! First, make sure that you always have an application-aware image-level backup or SQL database backup of Veeam Backup Enterprise Manager. Second, make sure that you always have an export of the current active keysets out of Veeam Backup Enterprise Manager. You can always export the active keyset within the Veeam Backup Enterprise Manager “key management” interface.
4. Do yourself a favor and protect your configuration backups in any case
As soon as you start to encrypt backup or backup copy jobs, you will need to encrypt your Veeam configuration backups as well. Due to the fact that some encryption keys and meta keys are stored in the configuration databases, Veeam will automatically disable the configuration backup by default to protect your configuration in case the configuration backup has been created without encryption! To overcome this you can enable the encryption of your configuration backup in the configuration backup settings.


In large environments with many components, hypervisors, managed servers and a complex configuration of application awareness backup, encrypted configuration backup is a true blessing. As soon as the configuration backup is encrypted, the credentials are also written to the configuration backup. The idea of having to manually re-enter each individual user and each individual password in the event of a disaster is terrible. Also, make sure to use the Veeam file copy job to place the configuration backup on different backup repositories to archive the highest amount of safety for this specific kind of backup file.
5. Don’t simply turn on encryption for your backup jobs!
When it comes to the encryption of backup and backup copy jobs, you should always get an overview of your current situation. This means that in this account, you should always know how busy your backup proxies and backup repositories are.
The reason for this is that even though the amount that performance decreases due to the activation of encryption is minimal, your backup proxies could still be overprovisioned. The other way around, if you simply enable backup job encryption for one or more jobs, Veeam will automatically do an active full backup on the next job run to apply encryption settings. This applies to backup jobs only. In case of backup copy jobs, you will need to manually trigger an active full. In limited or highly provisioned environments with much space consumed, this could cause in overprovisioning of the backup repositories or imbalanced extents on a Scale-out Backup Repository.
I hope you found these points helpful and I would love to hear your experiences from the wild. If you have any questions, feel free to ask them below.
