Media coverage on the various versions of encryption Trojans are coming fast and furious. These threats are meant to extort money out of the infected and are otherwise known as ransomware.
Trojan malware like Locky, TeslaCrypt and CryptoLocker are the variations currently used to attack companies. The breach gateways are often security loopholes in web browsers and their plugins or inadvertently opened email attachments. Once inside the company, the ransomware can spread at breakneck speeds and begin to encrypt valuable data. The FBI recommends companies implement a solid ransomware protection strategy to avoid data loss caused by CryptoLocker or any other Trojan.
Another area of focus for IT Security Professionals looking to enable ransomware protection are network shares. According to Bleeping Computer, the ransomware is also being used to access network shares.
Given the criticality of the workloads and data within the environment, the “1” in the 3-2-1 rule continues to play an important role. According to this rule, 3 copies of the company data should be saved on 2 different media and 1 copy should be offsite.
The backup architecture recommended by Veeam ensures that a primary backup storage device is used for quick backup and restore processes at which time backups are then copied to a secondary backup storage device using a native Backup Copy Job. In this blog, you’ll see how Veeam helps build a reliable ransomware protection strategy with backup and quickly recover your data after the ransomware attack.

Data export options to strengthen your backup strategy against the ransomware threat
1. Backup Copy Job to disk
As mentioned above, the first option is to transfer the data from one location to another using Backup Copy Job. Here, a file is not just copied, but the individual restore points within the backup are read and written to a second disk destination. Should the primary backup be encrypted or become corrupt, the Backup Copy Job would also fail because Veeam would not be able to interpret the data.
In such a scenario, one can only hope that the second backup repository has been separated from the rest of the IT environment. One could also use a Linux-based backup repository to secure against Windows Trojans.
2. Removable hard disks
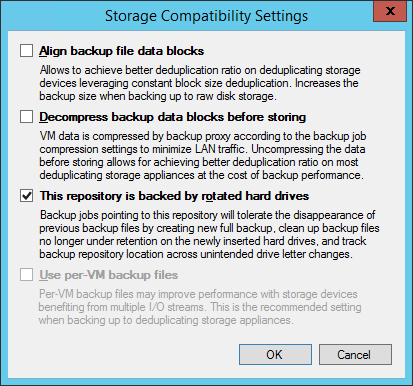
Another option for ransomware protection is to use a removable storage device as the secondary repository. This is usually done with removable hard drives such as USB disks. With the help of the Veeam option for media rotation (see User Guide), Veeam will detect when an old piece of media is re-inserted and automatically ensure that old backup files are deleted and a new backup chain is started.
What’s important to note here is that removable media (conventional USB hard disks, etc.) should be interchanged regularly and should not be kept connected to the system permanently.
3. Tape
The once “condemned” tape option is becoming an increasingly popular option for IT to leverage again in regards to encryption Trojans. This is because tapes do not enable direct data access, and thus provide ransomware protection. Just like rotatable media, tapes should be exported to a secure location for optimum protection.
4. Storage snapshots and replicated VMs
Organizations can enjoy additional Availability and ways to implement the 3-2-1 rule with storage snapshots and replicated VMs. These are “semi” offline instances of data that can be resilient against malware propagation; much like the Veeam Cloud Connect technology explained below.
5. Veeam Cloud Connect
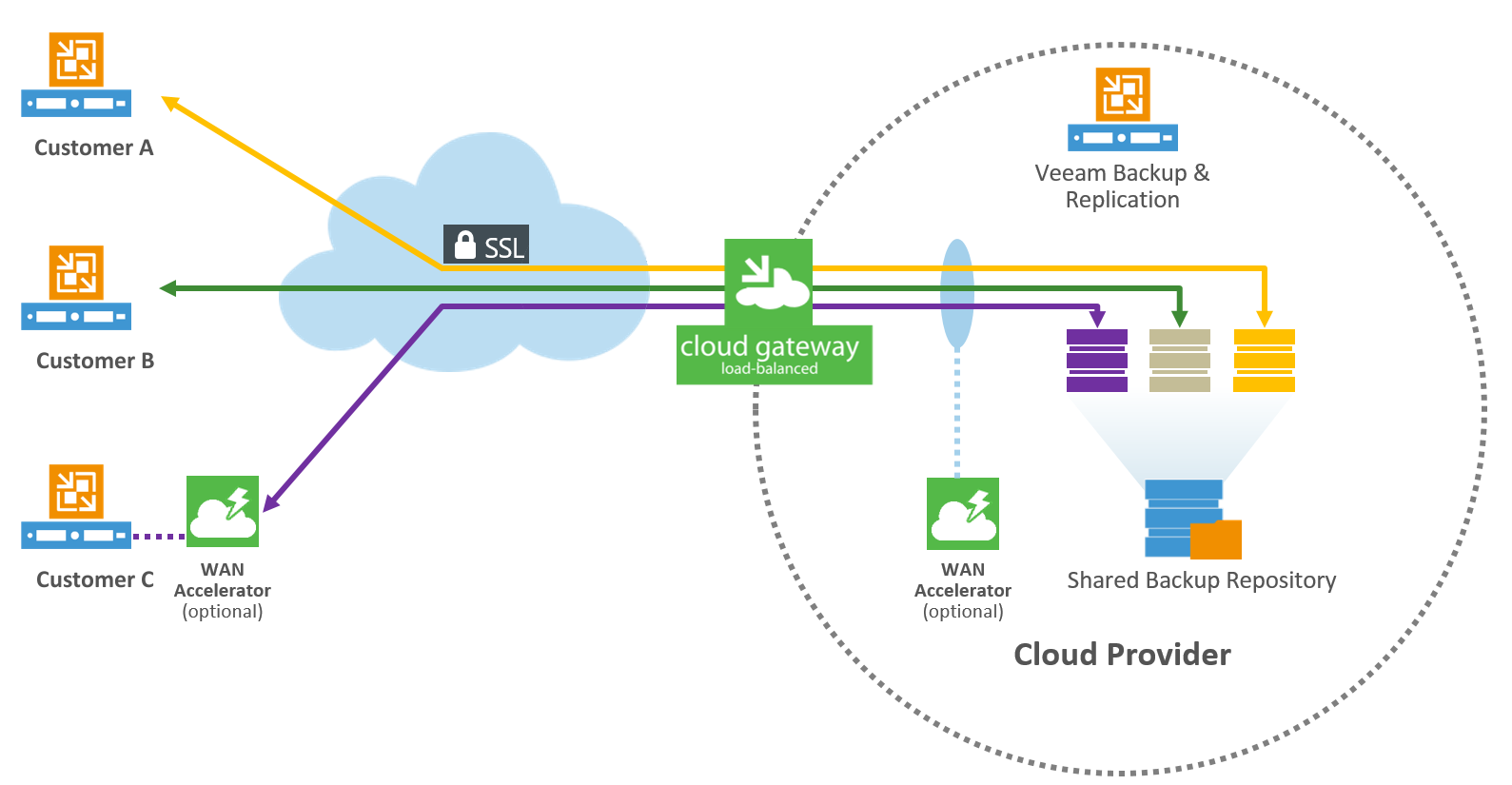
The best solution is for complete out-of-band protection such as Veeam Cloud Connect. Here, backups are taken via the same Backup Copy Job and automatically sent off to a service provider via the Veeam Cloud Connect mechanism.
The Veeam Cloud Connect service is offered through the Veeam Cloud & Service Provider program, and is being offered by service providers and IT resellers. You can consult your local partner and learn about their offerings.
To see which partners and service providers in your area offer the Veeam Cloud Connect service, visit the Find a Veeam Cloud & Service Provider directory.
Safeguarding Backup Repositories from ransomware
The backup repositories should also be safeguarded as much as possible in order to protect them from ransomware encryption attacks.
The access rights to the Backup Repository Server should be restricted such that only the Veeam service account has access to the Repository Server and the file system.
In case of NAS systems, only the Veeam service account should be provided with the permissions for the Backup Repository.
For security reasons, working on a local desktop with a domain administrator is absolutely not recommended because this can lead to the ransomware spreading around the network very quickly.
Many administrators by default deactivate the Windows Firewall as soon as the installation of Windows is complete. This built-in mechanism can provide protection against ransomware attacks from the network via the Windows security loopholes. It’s considered to be a best practice that you take a little time out and activate the necessary inbound and outbound requirements in the Windows Firewall. This documentation contains a list of the ports used.
A virus scanner with an activated real-time search should also be installed on all Windows systems. After installing a new server, often times a customer forgets to install their antivirus software. However, since virus scanners access a system deeply, they might block Veeam services. This knowledge base article provides information about the exceptions to be defined.
Summary
The tips provided here can help you considerably enhance your backup and recovery strategy for ransomware protection. Your backups will remain secure against infections and allow you to avoid any data loss in case of attacks. Always ensure that your local and remote Veeam Backup Repositories are being safeguarded. In conclusion, validate that your backups are also regularly exported in such a manner that the data is not directly accessible. By following these simple steps, you’ll be protecting your environment from the spread of malware such as CryptoLocker.
See also: