Key Takeaways:
- Critical infrastructure (energy, water, healthcare, and communications systems) is increasingly targeted by ransomware and state‑sponsored actors
- Attacks on operational technology (OT) can cause real‑world disruption, not just data loss
- Governments are moving from guidance to law, enforcing frameworks like NIST CSF, IEC 62443, and EU NIS2 to strengthen resilience
- A robust strategy blends prevention and recovery: Continuous monitoring, immutable backups, and tested restoration
Critical infrastructure cybersecurity protects the essential systems that keep society running: Power grids, water treatment plants, hospitals, transportation networks, and communications. These environments face constant threats from ransomware groups and state‑sponsored attackers seeking to disrupt operations or test national defenses.
When a single system goes offline, the ripple effects can halt supply chains, endanger public safety, and undermine trust. In recent years, incidents like the Colonial Pipeline shutdown and Ukraine power grid attack have shown how digital breaches can trigger physical consequences, proving that protecting critical infrastructure is now a matter of national resilience, not just IT security.
Veeam helps critical infrastructure operators strengthen cyber resilience by combining immutable backup, rapid recovery, and automated orchestration within the Veeam Data Platform — ensuring critical systems can be restored quickly and consistently after incident. These capabilities ensure that essential data, workloads, and control systems remain protected and recoverable across on‑premises, cloud, and hybrid environments. Designed to support alignment with leading frameworks, such as the NIST Cybersecurity Framework and IEC 62443, Veeam helps organizations strengthen compliance readiness, recover quickly from ransomware or insider attacks, and maintain operational continuity — even under regulatory pressure or cyber disruption.
The Stakes and Risk Landscape for Critical Infrastructure
Cybersecurity for critical infrastructure isn’t just about protecting data. It’s about protecting people, economies, and essential services. As power grids, water utilities, hospitals, and transportation networks become more connected, their exposure to cyber risk grows. A single breach can ripple across supply chains, halt production, or even endanger public safety. Understanding who targets these systems and how attacks unfold is the first step toward resilience.
Why Infrastructure Is a Unique Target
Critical infrastructure is different from typical enterprise IT. It blends operational technology (OT), the systems that run turbines, pumps, and sensors, with information technology (IT) that manages data and connectivity. This convergence creates efficiency but also opens new pathways for attackers.
Threat actors know that downtime in these environments has immediate, real‑world consequences. A manufacturing line can stop, a city can lose power, or a hospital can delay care. That urgency makes infrastructure operators prime targets for ransomware groups, who count on organizations paying quickly to restore operations.
At a geopolitical level, nation‑state actors see infrastructure as a strategic lever: disrupting utilities or communications can weaken an adversary without firing a shot. For attackers motivated by financial gain or political influence, critical infrastructure delivers both visibility and leverage.
Emerging Threat Vectors Specific to Infrastructure
While ransomware dominates headlines, it’s just one piece of the threat landscape. Infrastructure organizations face a mix of technical vulnerabilities and operational challenges that complicate defense.
- Legacy Systems: Many control systems still run on outdated software that can’t be patched or easily replaced. Once isolated, these networks are now connected for remote monitoring, exposing them to modern malware
- Supply Chain Compromise: Attackers increasingly target trusted vendors or software updates to gain access to industrial environments
- Insider Threats and Misconfiguration: Human error, weak credentials, or privileged‑access abuse can trigger major outages
- Ransomware and Double Extortion: Attackers not only encrypt data, but also threaten to leak it, intensifying pressure to pay
- Nation‑State Intrusions: Advanced Persistent Threat (APT) groups have been known to infiltrate systems to gather intelligence or establish long-term access that could be leveraged for future disruption
Many utilities once benefited from “security by obscurity,” relying on legacy systems few outsiders understood. That protection no longer holds. Modernization and cloud connectivity are essential. But they must be paired with modern cyber resilience strategies.
Recent Incident Examples and Trends
Over the past decade, several high‑profile cases have underscored how cyberattacks on infrastructure can escalate into national headlines:
- Colonial Pipeline (2021): A ransomware attack on a corporate IT system prompted precautionary shutdown of fuel operations, leading to widespread gas shortages across the U.S. East Coast
- Ukraine Power Grid Attacks (2015 and 2016): State‑sponsored actors caused power outages affecting hundreds of thousands of citizens. It was the first confirmed incident of cyber‑induced blackouts
- Ukraine 2022: A series of DDoS attacks targeted government and financial institutions, disrupting online services and demonstrating how cyberattacks can affect national stability during conflict
- Littleton Water System Breach (2024): Malicious code linked to foreign actors was found in a small U.S. town’s water infrastructure, proving that even local utilities are vulnerable
Each incident reinforces a pattern: Attacks are becoming more strategic, targeted, and consequential. In response, governments are tightening regulations, mandating faster incident reporting, and holding operators accountable for resilience.
The takeaway is clear: defense alone isn’t enough. Critical infrastructure requires verified recovery capabilities and a tested continuity plan.
Foundational Frameworks and Standards for Infrastructure Cybersecurity
Critical infrastructure organizations face one of the most regulated cybersecurity landscapes in the world. From power grids and water systems to healthcare and telecom, operators are required to follow internationally recognized frameworks that define how to identify, protect, detect, respond, and recover from cyber threats. These standards don’t compete; they complement each other, providing a shared foundation for resilience.
NIST Cybersecurity Framework (CSF) and ICS Extensions
The NIST Cybersecurity Framework (CSF) is the cornerstone of most global infrastructure security programs. Initially developed for U.S. critical infrastructure, its guidance is now applied worldwide. The framework organizes cybersecurity activities into five core functions:
- Identify: Understand assets, risks, and business context.
- Protect: Apply safeguards to maintain service delivery.
- Detect: Monitor for anomalies and malicious activity.
- Respond: Contain incidents and communicate effectively.
- Recover: Restore systems and data to normal operation.
And the new CSF 2.0, released in 2024, expands its scope beyond critical infrastructure to all sectors and introduces a sixth, cross‑cutting function:
- Govern: emphasizing leadership, policy alignment, and accountability.
For industrial and operational environments, NIST provides ICS extensions and collaborates with CISA to tailor guidance for control systems. These include recommendations for asset inventory, network segmentation, and coordinated response between IT and OT teams.
By following NIST CSF, organizations create a blueprint for compliance that also supports frameworks like IEC 62443 and NIS2.
IEC 62443 & ICS/SCADA Security Standards
The ISA/IEC 62443 series focuses specifically on industrial automation and control systems (IACS), including SCADA environments used in energy, manufacturing, and utilities. Developed jointly by the International Electrotechnical Commission (IEC) and the International Society of Automation (ISA), these standards define how to secure devices, networks, and system architectures throughout their lifecycle.
Key principles include:
- Zone and Conduit Model: Segment networks into secure zones and control data flow between them
- Defense‑in‑Depth: Layered security combining physical, network, and application controls
- Role‑Based Access Control (RBAC): Limit privileges to reduce insider risk
- Secure Development and Maintenance: Ensure that vendors and integrators build cybersecurity into product design
IEC 62443 is increasingly recognized by regulators and procurement agencies as a baseline for OT security. It complements NIST CSF by translating broad risk-management principles into technical control requirements for industrial systems.
Organizations using Veeam Data Platform can align with these standards through immutable backup storage, air‑gapped replication, and secure restore workflows, all of which support IEC 62443’s recommendations for validated recovery capability.
Regulatory and Directive Context (NIS2, NERC CIP, Others)
Regulations now give these frameworks legal weight. Governments worldwide are moving from voluntary guidelines to mandatory cybersecurity laws for operators of essential services.
- EU NIS2 Directive (2023): Expands scope to 18 critical sectors and requires initial incident notification within 24 hours of detection, followed by detailed reports within 72 hours and one month. It mandates comprehensive risk-management measures aligned with NIST CSF and IEC 62443, plus executive accountability for cybersecurity programs
- NERC Critical Infrastructure Protection (CIP): Applies to North American bulk power systems; sets detailed standards for asset identification, electronic security perimeters, and recovery planning
- Global Adoption: Similar laws are emerging in Singapore, Japan, and Australia, each enforcing stricter reporting timelines and documentation requirements
Framework for Improving Critical Infrastructure Cybersecurity
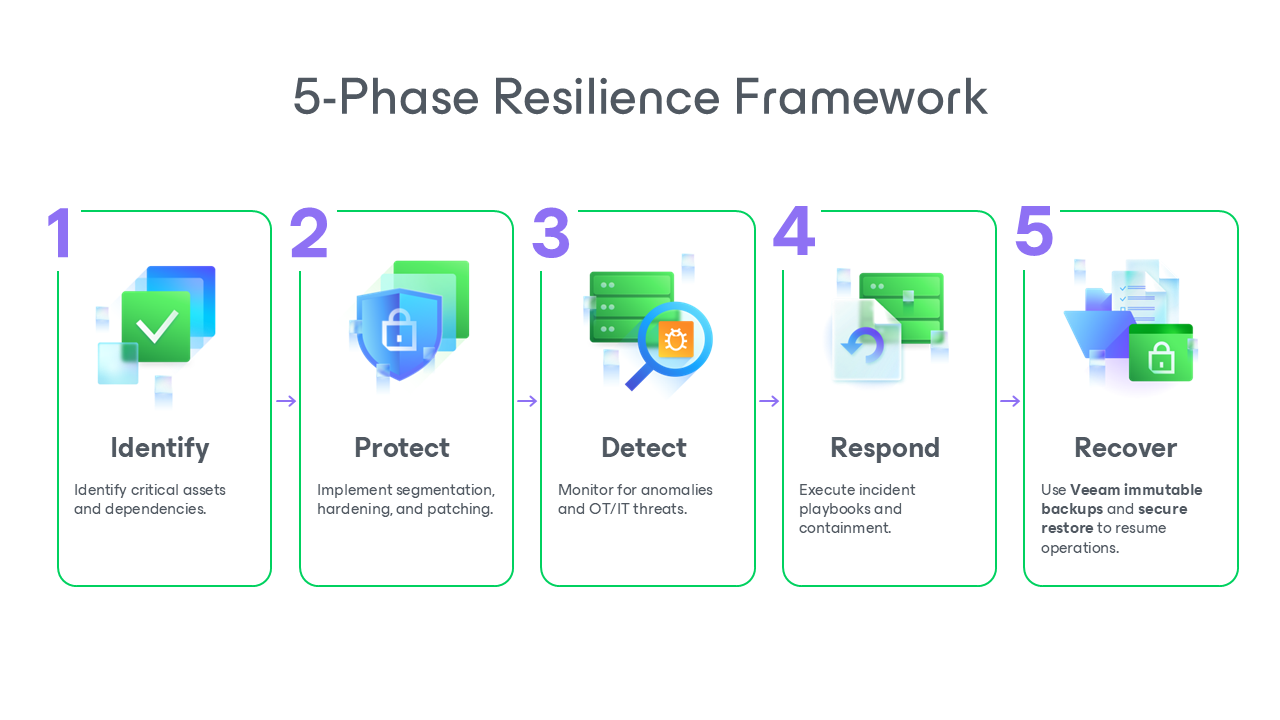
A practical way to build that resilience is through a structured framework that balances defense, detection, and recovery. The most widely adopted model, based on the NIST Cybersecurity Framework 2.0, organizes activities into five core phases: Identify, Protect, Detect, Respond, and Recover.
Each phase represents a layer of resilience that operators can strengthen with modern tools and tested processes. Together, they create a repeatable cycle of preparation, protection, and restoration — exactly what today’s interconnected energy, water, and communications systems need to stay secure and operational.
Identify — Know What You Need to Protect
Everything begins with visibility. Critical infrastructure organizations must understand which assets, systems, and data are essential to operations and how they connect across IT and OT environments.
- Maintain an accurate inventory of hardware, software, and data flows
- Map dependencies between control systems, IT networks, and external vendors
- Assess risk by impact, not just likelihood. A single outage can have national consequences
Veeam helps strengthen this phase through centralized monitoring and reporting tools like Veeam ONE, which provide real‑time visibility into backup status, performance, and risk indicators.
Protect — Defend and Prepare for Disruption
Protection means implementing safeguards that maintain service delivery even under attack.
- Segment networks between IT and OT systems to limit lateral movement
- Apply multi‑factor authentication (MFA) and least‑privilege access policies
- Use immutable backups to ensure recovery points cannot be altered or encrypted
- Keep one copy offline or air‑gapped to prevent ransomware propagation
With Veeam Backup & Replication, organizations can automate these protections, ensuring data is secure, immutable, and ready for recovery.
Detect — Spot and Respond to Anomalies Early
Detection is about speed and situational awareness.
- Implement continuous monitoring across IT and OT networks
- Use behavioral analytics to identify unusual activity before it escalates
- Share telemetry between operations and security teams for unified visibility
Veeam integrates with modern threat‑detection platforms to share backup telemetry and provide built‑in backup verification tools that help teams confirm recovery copies are clean and uncompromised.
Respond — Contain and Communicate Effectively
When an incident occurs, clarity and coordination matter most.
- Activate incident‑response playbooks that define roles, escalation paths, and communication channels
- Isolate affected systems quickly to contain spread
- Notify regulators and stakeholders within mandated timeframes, as required under NIS2 and NERC CIP
- Document actions for audit and lessons‑learned reviews
Veeam Recovery Orchestrator automates these response steps, ensuring every action is recorded and repeatable. It helps operators meet reporting and documentation requirements with minimal manual effort.
Recover — Restore and Validate Operations
Recovery closes the loop, turning preparation into resilience.
- Restore systems and data from verified, immutable backups that cannot be altered or deleted — even if production systems are encrypted or compromised
- Validate recovery points before re‑deployment to prevent reinfection
- Conduct post‑incident testing to confirm operational readiness
- Update plans and controls based on findings
With Veeam Data Platform, recovery becomes both fast and trustworthy. Features like Instant VM Recovery, Secure Restore, and automated testing help organizations meet strict RTO/RPO targets and demonstrate alignment with frameworks such as NIST CSF and IEC 62443.
Governance, Organizational, and Operational Alignment
Strong technology is only half of the resilience equation. The other half is governance: How people, processes, and policies work together to protect and recover critical systems. In complex infrastructure organizations, success depends on clear ownership, cross‑department collaboration, and a unified understanding of risk.
Cyber resilience requires alignment between IT, OT, and security teams. In many utilities and public‑sector environments, these groups operate in silos: IT manages data, OT runs industrial controls, and security oversees compliance. When a cyber incident occurs, that separation can slow containment and complicate recovery. Bridging these gaps is one of the biggest challenges facing critical infrastructure operators today.
1. Start with Clear Ownership: Resilience Begins with Accountability
Every team should know who’s responsible for prevention, response, and recovery.
- Assign a cyber resilience leader or CISO with authority across both IT and OT
- Define who decides and who acts during an incident
- Document escalation paths and communication channels in advance
This clarity eliminates confusion when time matters most.
2. Unify IT and OT Visibility: You Can’t Protect What You Can’t See
Critical infrastructure blends legacy control systems with modern data platforms. To manage risk effectively:
- Combine monitoring for IT and OT to get a single view of backup health and system status
- Encourage joint review sessions between operations and security teams
- Run tabletop exercises that simulate both cyber and physical disruptions
3. Test, Review, Improve: Governance Is Only as Strong as Its Last Test
Static policies don’t work in a threat landscape that changes daily.
- Schedule regular recovery tests and update plans after major system or staff changes
- Capture lessons learned after every incident or exercise
- Keep evidence ready for audits under NIST CSF, IEC 62443, or NIS2
4. Turn Coordination into Culture
When communication becomes routine, resilience becomes culture. Encourage:
- Shared goals between IT, OT, and security
- Continuous learning through cross‑team drills
- Executive support for ongoing cyber resilience investment
Unified governance doesn’t just meet compliance requirements. It builds trust, speeds up recovery, and keeps critical services available when they matter most.
Protect What Matters Most: Build Resilience for Critical Infrastructure
Resilience means being ready for the unexpected: An outage, a ransomware attack, or a system failure that could ripple far beyond the network. Regulations like NIS2, NERC CIP, and frameworks such as NIST CSF all point to the same truth — organizations must prove they can recover fast and recover clean.
That’s where Veeam comes in.
With the Veeam Data Platform, critical infrastructure operators can:
- Protect data with immutable, air‑gapped backups that can’t be altered or encrypted
- Recover systems quickly and confidently through secure restore and automated orchestrationValidate compliance with built‑in reporting and testing tools that demonstrate readiness
Resilience is a continuous cycle of protection, detection, and recovery. By integrating these practices into daily operations, teams turn cybersecurity from a reactive task into a proactive safeguard for essential services.
Ready to modernize your infrastructure protection?
Explore the Veeam Data Platform — your foundation for cyber‑secure resilience.
FAQs
What distinguishes critical infrastructure cybersecurity from general enterprise cybersecurity?
Critical infrastructure cybersecurity protects systems that power essential services: Energy, water, healthcare, transportation.
Unlike enterprise security, it covers both digital and physical operations, where downtime can threaten safety and stability. It also demands collaboration between IT and OT teams and compliance with stricter regulations like NIS2 and NERC CIP to ensure national resilience.
How do immutable backups help in critical infrastructure settings?
Immutable backups create recovery copies that can’t be changed or encrypted, even if attackers breach production systems.
They guarantee a clean restore point for rapid recovery after ransomware or data corruption.
Which frameworks are most relevant to infrastructure operators?
The most common frameworks include NIST CSF 2.0, IEC 62443, NERC CIP, and the EU NIS2 Directive.
Together they guide risk management, compliance, and recovery planning across critical sectors. Following these standards helps operators align cybersecurity with resilience goals supported by Veeam solutions.
How often should infrastructure operators test recovery and resilience?
Operators should test recovery at least twice per year or more frequently based on risk and system criticality — and after major changes.
Frequent testing validates backup integrity, confirms recovery time objectives, and ensures compliance.