- Veeam Support Knowledge Base
- VMware Cloud on AWS - Support, Considerations, and Limitations
VMware Cloud on AWS - Support, Considerations, and Limitations
Cheers for trusting us with the spot in your mailbox!
Now you’re less likely to miss what’s been brewing in our knowledge base with this weekly digest
Oops! Something went wrong.
Please, try again later.
Challenge
VMware Cloud on AWS is an integrated cloud offering developed by AWS and VMware. It requires specific preparation to enable Veeam Backup & Replication to function with it. Apart from the preparation process and the limitations mentioned at the end of this article, you can interact with VMware Cloud on AWS using Veeam Backup & Replication, just as you would with any other vSphere environment, to back up, restore, and replicate VM workloads.
However, not all VMware features and permissions are granted by default with these VMware Cloud offerings. Consequently, some Veeam Backup & Replication features may be limited or non-functional. Depending on updates released by VMware, this situation may change, and the features listed in the table below may become available. Please consult with your VMware administrator for timely updates.
Solution
Implementation Step 1 - Prepare the Veeam Backup Server
- If you do not have a Veeam Backup Server, use a new Windows Server and install the latest version of Veeam Backup & Replication. The Server can run within any VMware Cloud on AWS SDDC, the ENI-connected AWS environment, or on-premises datacenter environments if the network connection to the VMC vCenter/Veeam Servers and potentially the VMs (for Guest processing) is possible.
- Add DNS network settings so that the Veeam Backup Server can resolve Internet DNS names to resolve the fully qualified domain name of the VMC vCenter server.
- Check the below information carefully for any known limitations and configuration steps before you proceed.
Implementation Step 2 - Configure VMware Cloud
Firewall Configuration for vCenter connection
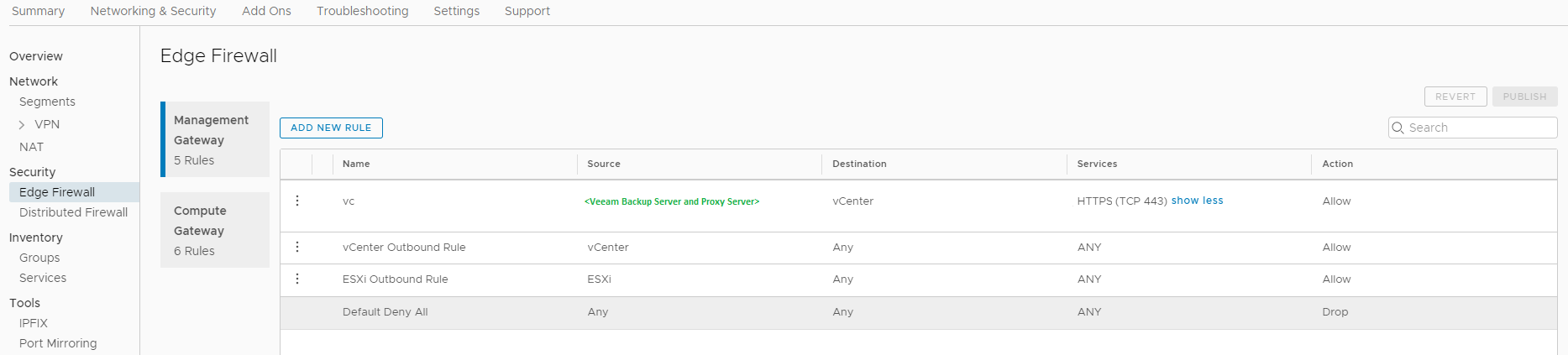
The Veeam Backup Server and VMware Backup Proxy should be connected to the VMware vCenter using HTTPS through TCP port 443. In VMware Cloud on AWS, there is no need to open ports to the ESXi hosts themselves, as the vCenter Server is by the design of VMware Cloud on AWS on another network (Management Network). You will need to configure one of the following 3 options:
Usage of the local connection for customers with VMware NSX-t (default)
NSX-t allows VMC customers to directly access the management network over the built-in firewall. TCP Port 443 needs to be opened from all Veeam Backup and VMware Backup Proxy servers as a Source with the vCenter internal IP as a target.
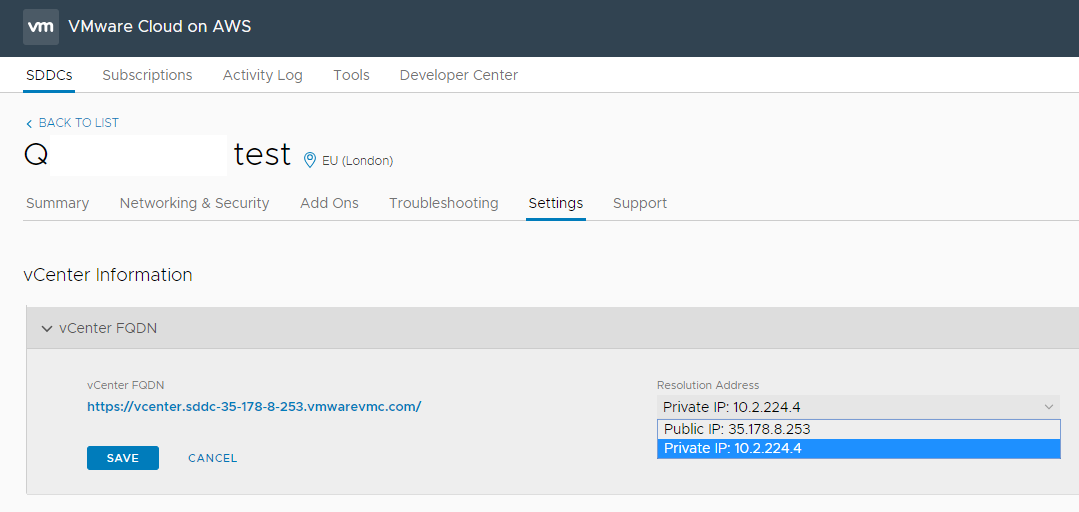
- Configure the DNS entry of the vCenter for local IP address usage.
Go to your SDDC Management – Settings – vCenter FQDN and select the Private vCenter IP address.
Hint: If you configure the vCenter DNS record for the internal IP address, you will lose the VMC connection from the Backup and Replication Server outside of VMC. You can use the local hosts file or any other DNS method to resolve the vCenter FQDN with the public IP address on the Veeam Server outside of VMC. Optionally, you can use the Public IP address for the VMC internal and external Veeam Server.
- Open firewall ports for vCenter Server access.
- On the Management Network:
- On the Compute Gateway:
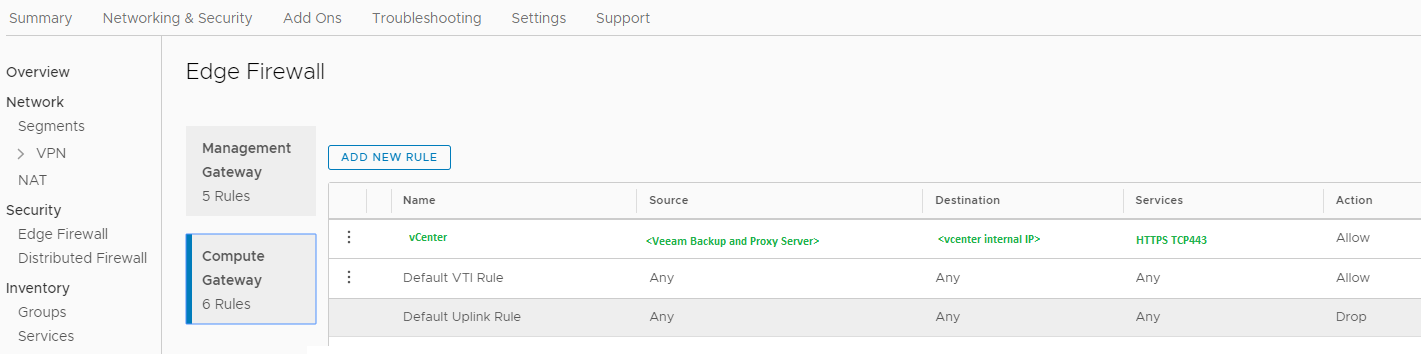
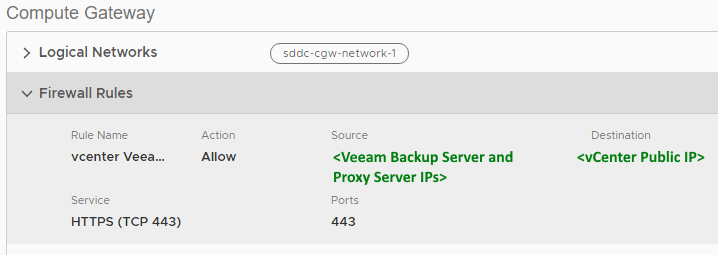
Usage of the vCenter public IP for customers with NSX-v
- Open Port TCP 443 from the Veeam Backup Server and VMware Backup Proxy to the predefined vCenter object on the Compute Network.
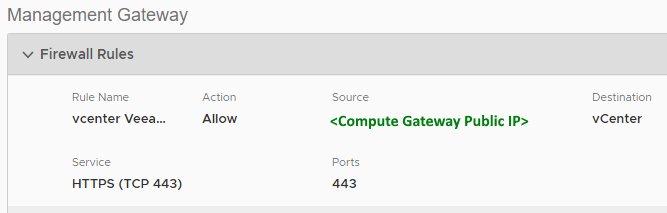
- Allow the Compute Gateway Public IP to communicate over TCP 443 with the predefined vCenter object on the Management Network.
Usage of a VPN tunnel for customers with VMware NSX-v
To access the vСenter within VMC directly, please follow the VMC internal guidelines to create a VPN tunnel from the compute network to the management network.
Please update your DNS Servers to resolve the FQDN of the vСenter to its private IP address. If you want to use hosts entries on the Veeam Servers for it, add them on the Veeam Backup Server and all associated VMware Backup Proxies.
If your Veeam Backup & Replication (Management) Server is outside the VMC cluster, please implement the same VPN connection for it.
Implementation Step 3 - add the vCenter to Veeam Backup & Replication
When adding the vCenter server, specify the fully qualified domain name (FQDN) that ends with either vmwarevmc.com or vmc.vmware.com, depending on the URL displayed in the VMC interface for the vCenter.
For the credentials, you can use:
- The cloudadmin@vmc.local account.
or - An account with the same permissions as the cloudadmin user. However, you must ensure that you have an external identity source configured in vCenter and that the user or group you want to assign these permissions to is assigned the CloudAdmin role.
Implementation Step 4 - add a VMware Backup Proxy
For any VMware Cloud on AWS Software-Defined Data Center (SDDC) Cluster, it is recommended to deploy at least one VMware Backup Proxy server to utilize the Virtual Appliance (HOTADD) transport mode. If the Veeam Backup Server is deployed within the SDDC Cluster, it can also function as a VMware Backup Proxy.
Please note that Linux-based VMware Backup Proxies are not compatible with VMware Cloud on AWS, as they do not support certain mandatory VMware Virtual Disk Development Kit (VDDK) settings.
Implementation Step 5 - add a Veeam Repository
Given that VMware Cloud on AWS provides access to only one vSAN disk, it would be inadvisable to use this disk for both production workloads and backup storage. Therefore, it is recommended to use an external storage device for storing backup files. The method for achieving this can vary based on the use case and economic factors.
For example:
- Send data directly to Amazon S3 object storage, if applicable.
- Use an EC2 VM as a backup target and then tier to Amazon S3
- Send backup data to a repository in a different location, depending on the bandwidth and throughput available.
Remember, you may need to configure network security groups to allow Veeam repository traffic. Veeam - Backup Repository Connections.
Example of Linux EC2 w/ EBS Storage

To connect the EC2 Server(s) used as Veeam Repositories, the following Firewall configuration is needed:
-
On the Compute Network:
-
Open the TCP port 22 (SSH) from the Veeam Backup Server and VMware Backup Proxy to the Amazon VPC, where the EC2 Server was installed. You can also define the exact IP addresses of the repository server as Destination.
-
Open TCP 2500-5000 ports for Veeam Data Transport in both directions for the same servers. Using the VMware Cloud on AWS integrated high throughput/low latency ENI network connection is recommended to avoid traffic costs.
-
- Open the same ports on the Inbound Firewall of the Amazon EC2 server acting as a repository server. As the Firewall Rule Source, you should add all Veeam Backup Servers (including Proxy/Repository/MountServer/Console/…) instead of 0.0.0.0/0
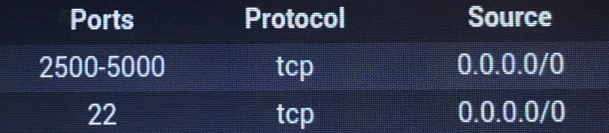
| Ports |
Protocol |
Source |
| 2500-3300 |
tcp |
0.0.0.0/0 |
| 22 |
tcp |
0.0.0.0/0 |
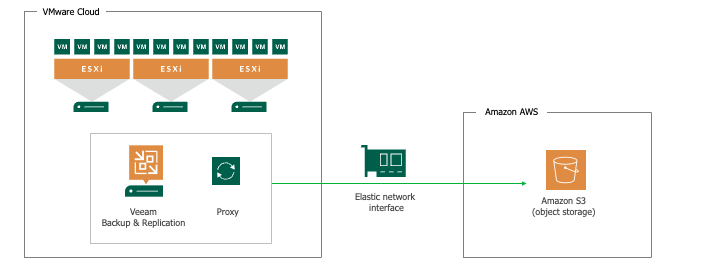
Example of Direct Backup to Object Storage
Note: Any supported object storage can be used. The example below utilizes Amazon S3 to keep all traffic within the AWS environment and assumes that the Gateway Server assigned to the AWS S3 Repository is located in the VMware Cloud on AWS.
Below is an example of an Amazon S3 bucket used as a backup target over the VMware Cloud on AWS integrated ENI network connection.
Implementation Step 6 - add a secondary backup target
It is suggested to create a backup copy in an additional place. Depending on the use case, there are several ways to achieve this with different economic factors. Among other ways, the following technologies can be used:
- Veeam Scale-out Backup Repository – CapacityTier usage. This feature can be used in copy mode to create additional backup copies in Amazon AWS S3. Make sure to use the internal interface of the S3 target to avoid internet traffic costs.
- For VMware Cloud on AWS, a Veeam Backup Copy Job to a second EC2 Server can be used as an additional Repository. The second EC2 Server can be placed on another AWS Availability Zone or AWS Geo-Location.
- AWS Storage Gateway Software in VTL mode can emulate a Tape Library to write data to S3. Veeam Backup to Tape Jobs can be used with it. For details, review Veeam Backup & Replication using AWS VTL Gateway - Deployment Guide.
- Veeam Backup Copy Job to an on-premises or Veeam Cloud Connect (Enterprise). No particular configuration is needed for this use case besides network and firewall connections. For standard Repository usage on-premises, creating a VPN tunnel from VMware Cloud on AWS to the on-premises datacenter is recommended. This can be done by the VMC-integrated VPN functionality or third-party VPN solution.
Additional Scenarios
- VMware Cloud on AWS is used as a Restore target.
- Implementation steps 1-4 are needed.
- Veeam VM Replication.
- Implementation steps 1-5 are needed. The Repository Server (when NOT used for Backups, can run within the VMware Cloud on AWS SDDC to store the Veeam Replication data. On-premises standard datacenter to VMC, VMC to VMC, and VMC to on-premises standard datacenter is possible. Usage of Veeam Recovery Orchestrator is possible in specific scenarios. See the Veeam Recovery Orchestrator Deployment Guide.
VMware Cloud (VMC) - Problems and Solutions:
- VMware internal monitoring reports access violations to ESXi host hardware sensors when Veeam ONE is used.
Contact support to obtain registry vale to correct this. - When performing an Entire VM restore, using the Restore to a new location mode, to VMware Cloud on AWS with VMware NSX-t, the Network tab's Networks... selector is empty.
To solve the issue, upgrade to Veeam Backup & Replication 11.0.0.837 P20210525 or later. - Impossible to add the VMware Cloud on AWS vCenter server to the managed server. VMs within this vCenter are not visible in the list of VMs, or an Error is displayed in the Veeam Jobs “Processing SQL Error: File does not exist or locked. …”
Create a vCenter User with the required rights (Active Directory linked mode) described here, or use the cloudadmin@vmc.local user.
When adding the vCenter server, specify the fully qualified domain name (FQDN) that ends with either vmwarevmc.com or vmc.vmware.com, depending on the URL displayed in the VMC interface for the vCenter. - When working with the Restore or VM Replication wizard, users may face issues accessing VMware Cloud on AWS vCenter server. By design, VMware does not provide customers access to the background infrastructure and used datastores.
For proper operation, you can select the specific areas marked as “Workload” or “Compute.” Avoid using the non-accessible areas, for example:- vsanDatastore datastore
- Management VMs folder
- Mgmt-ResourcePool resource pool
- Veeam Backup & Replication stops working after VMware Cloud on AWS is automatically updated.
Please check this article for the minimum required Veeam Backup & Replication version or Patches.
For customers with socket-based licensing, ensure that the automatically generated new ESXi hosts can receive Veeam licenses. Potentially, older ESXi hosts need to be revoked from the license. We recommend using Veeam Universal Licensing to avoid any license-specific issues with VMware Cloud on AWS.
Some of the Veeam Backup & Replication Features are not working correctly because of limitations of the VMware Cloud on AWS environments (compared with a standard vSphere environment).
| Affected Veeam Feature | Limitation | Workaround |
|
Instant VM Recovery |
Currently, VMware Cloud on AWS (VMC) does not allow for NFS usage |
Use a combination of a Veeam backup job and replication job for proactive restore capabilities |
|
Other OS File Level Recovery |
Currently, VMC does not allow for NFS usage |
Start Linux File Level Recovery with a Linux server helper host, instead of using a temporary helper appliance |
|
SureBackup, Sure Replica, OnDemand Labs, Virtual Lab |
Currently, VMC does not allow NFS and network manipulation |
As for SureReplica, you can perform it if the replication target is a non-VMC vSphere environment (e.g., replicate VM from VMC to on-premises) |
|
VM Replication ReIP |
ReIP is not available on VMC |
|
|
Non-Unicode VM names |
Currently, VMC does not allow non-Unicode characters for VM names within their APIs used ad VMC |
|
|
VM Replication-based File Level Recovery |
|
Use file restore from backups or use a VM replica on a non VMC environment to start the File recovery |
| Replication (where EC2-based repository is used to store replica metadata) | Due to lack of permissions, the repository Data Mover is not able to connect to the Veeam Server | Enable "Run server on this side" option for the repository. For Windows repositories it can be found under Ports configuration, for Linux - under Advanced settings in the server configuration wizard. |
| Continuous Data Protection (CDP) | Currently, VMware Cloud on AWS (VMC) does not allow for CDP |
If this KB article did not resolve your issue or you need further assistance with Veeam software, please create a Veeam Support Case.
To submit feedback regarding this article, please click this link: Send Article Feedback
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
Spelling error in text
Thank you!
Your feedback has been received and will be reviewed.
Oops! Something went wrong.
Please, try again later.
You have selected too large block!
Please try select less.
KB Feedback/Suggestion
This form is only for KB Feedback/Suggestions, if you need help with the software open a support case
Thank you!
Your feedback has been received and will be reviewed.
Oops! Something went wrong.
Please, try again later.
