- Veeam Support Knowledge Base
- "Access is Denied." When Using a Local Account to Add a Windows Machine to Veeam Backup & Replication
"Access is Denied." When Using a Local Account to Add a Windows Machine to Veeam Backup & Replication
| KB ID: | 4185 |
| Product: |
Veeam Backup & Replication | 13 Veeam Agent for Microsoft Windows | 13 |
| Published: | 2021-06-23 |
| Last Modified: | 2026-01-12 |
| Languages: | JP |
Cheers for trusting us with the spot in your mailbox!
Now you’re less likely to miss what’s been brewing in our knowledge base with this weekly digest
Oops! Something went wrong.
Please, try again later.
This article relates to an error that only occurs when Veeam Backup & Replication is deployed on a Windows machine.
With the Veeam Software Appliance, to add a Windows machine using credentials, it requires that both the appliance and the Windows machine are added to the same domain to enable Kerberos authentication. Alternatively, the new Veeam Deployment Kit can be used to eliminate the need to provide remote credentials, instead allowing for certificate-based authentication.
Attempting to add a Windows machine to the Veeam Software Appliance using local credentials will cause it to throw the error:
Cannot find the specified domain. Ensure Kerberos credentials are
specified in FQDN\USER or USER@FQDN format. Local user
accounts are not supported. Samba failed with error:
NT_STATUS_NO_SUCH_DOMAIN [stdout: session setup failed:
NT_STATUS_NO_SUCH_DOMAIN. stderr: Kinit for
administrator@{hostname} to access {hostname} failed: Cannot find KDC
for requested realm. ]
Challenge
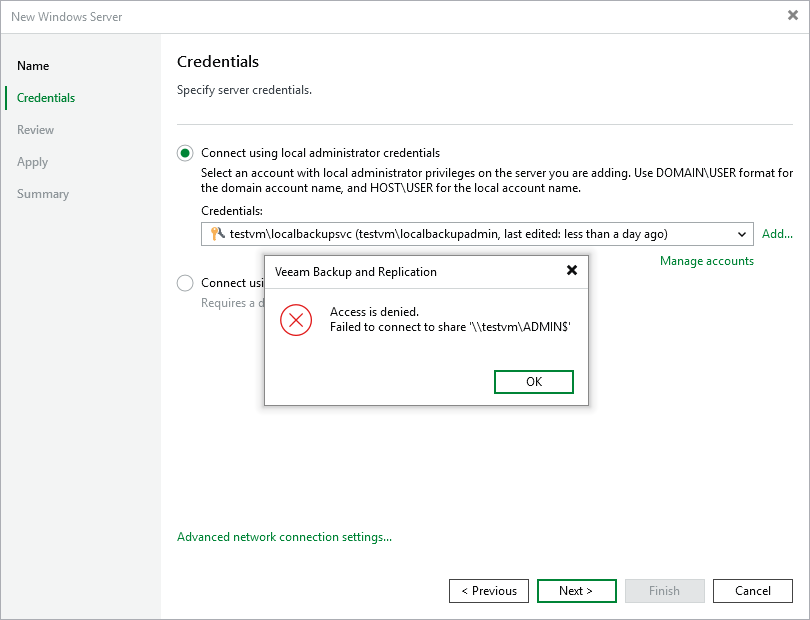
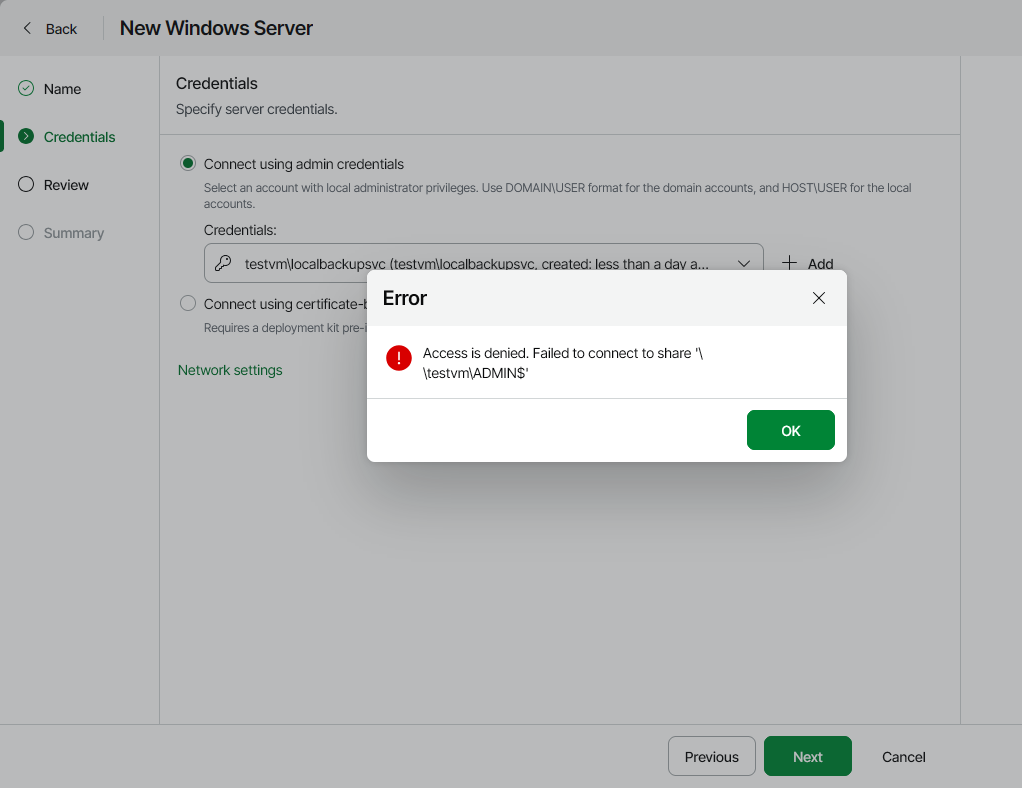
While attempting to perform one of the following actions the error "Access is Denied." occurs:
- When attempting to add a Windows server to Veeam Backup & Replication using a Local Administrator account.
Access is denied. Failed to connect to share '\\{hostname-ip}\ADMIN$'
- Rescanning a Protection Group that contains a Windows server that has been set to use a Local Administrator account for connection credentials.
Failed : Unable to install backup agent: failed to connect to testvm Error: Failed to connect with deployment kit. (Failed to connect with deployment kit on {hostname-ip}:6160: Access is denied. Failed to connect to share '\\{hostname-ip}\ADMIN$'. ) (Failed to connect with deployment kit on {hostname-ip}:11731: Access is denied. Failed to connect to share '\\{hostname-ip}\ADMIN$'. ).

Cause
When a Windows Server is added as a Managed Server or added to a Protection Group and configured to use credentials-based authentication, Veeam Backup & Replication checks if the Veeam Installer Service (VeeamDeploySvc) is present on the server. If the service is not accessible, Veeam Backup & Replication will attempt to connect to the machine via the admin$ share to deploy the service.
Example: \\localhost\admin$
The "Access is Denied" error occurs because the user account specified is a local account, and UAC restricts remote access for local accounts.
Solution
When attempting to add a remote Windows machine as a managed server or as part of a Protection Group using credentials-based authentication, the user account used to connect to that remote machine must work with the UAC remote restrictions. That account must be either:
- A domain account that is a member of the Local Administrators group.
- The built-in account named Administrator.
Note: The built-in Administrator account may fail if the "User Account Control: Admin Approval Mode for the Built-in Administrator account" policy is enabled on the remote machine.
Alternate Option
As an alternative to adding the Windows server to Veeam Backup & Replication using credentials-based authentication, the new Veeam Deployment Kit can be installed on the Windows machine before adding it to Veeam Backup & Replication. This will allow you to select the "Connect using certificate-based authentication" option, eliminating the need to provide credentials to Veeam Backup & Replication to establish a connection to the remote machine.
Use Case Examples when Using Credentials-based Authentication
- If the Windows machine being added to Veeam Backup & Replication is joined to a domain, a domain account that is a member of the Local Administrators group on the remote machine should be used to add the server to Veeam Backup & Replication.
- If the Windows server being added to Veeam Backup & Replication is not joined to a domain, or there is a need to avoid using a domain account, the built-in account named Administrator is the only account that can be used to add the server to Veeam Backup & Replication remotely. Other local accounts will be restricted by UAC, even if they are members of the Administrators group.
Note: If the Administrator account has been renamed, it can be used as the unique SID that bypasses Remote UAC Restrictions is still valid. - If the Windows machine being added to Veeam Backup & Replication is not joined to a domain and is not a server OS, the built-in Administrator account will have to be enabled and a password set for it. Then, that account should be used to add the machine to Veeam Backup & Replication.
More Information
If none of the provided solutions are viable, it is possible to disable UAC remote restrictions. This will allow local accounts other than Administrator to be used for remote access. This option should be considered a last resort as it involves disabling a Microsoft Windows OS security feature.
We highly recommend simply using the Veeam Deployment Kit instead of disabling UAC remote restrictions.
If this KB article did not resolve your issue or you need further assistance with Veeam software, please create a Veeam Support Case.
To submit feedback regarding this article, please click this link: Send Article Feedback
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
Spelling error in text
Thank you!
Your feedback has been received and will be reviewed.
Oops! Something went wrong.
Please, try again later.
You have selected too large block!
Please try select less.
KB Feedback/Suggestion
This form is only for KB Feedback/Suggestions, if you need help with the software open a support case
Thank you!
Your feedback has been received and will be reviewed.
Oops! Something went wrong.
Please, try again later.