Impact of tmux on Veeam Interactions With Linux OS
Purpose
This article documents a known incompatibility between Veeam applications that initiate SSH connections to remote Linux machines and those Linux machines being configured to have tmux autorun when users connect.
Connection Examples
As stated, this issue affects all interactions wherein a Veeam application makes an SSH connection to a remote Linux server that has tmux automatically start during account login. The list below is not exhaustive and presents the most commonly impacted scenarios.
- Adding a Linux machine to Veeam Backup & Replication as a managed server.
- Adding a Linux machine to a Protection Group.
- Viewing In-Guest Processes and Services from Veeam ONE Client.
Known Limitation
Veeam Backup & Replication does not support SSH connections to a server where when the user Veeam logs in as is configured to have tmux automatically start.
- For persistent agents, automatic tmux at login must be disabled during the initial deployment of the Veeam Data Mover services that are installed when the Linux Machine is first added to Veeam Backup & Replication.
- For Hardened Repositories, review: https://www.veeam.com/kb4250
- For non-persistent agents, automatic tmux must be disabled completely for the user Veeam Backup & Replication is configured to connect as.
Note: This use scenario is rare as it only occurs when the account supplied to Veeam Backup & Replication does not have sudo rights.
While this specific example is from RHEL 8 using the NIST 800-171 security profile, which includes tmux automatic startup system-wide, the same concept applies to other distros.
To disable the automatic launching of tmux, edit the /etc/bashrc file and comment (#) out the line with tmux, as shown in the grep output below.
More Information
For non-persistent configurations, or customers seeking to ensure Veeam Backup & Replication can SSH into the Linux machine as needed for operations such as upgrading the Data Mover Services, an exemption could be created to prevent tmux from starting for the specific user account provided to Veeam Backup & Replication.
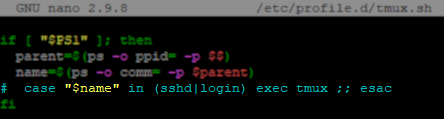
For example, below is the default if statement used to start tmux automatically.
if [ "$PS1" ];then parent=$(ps -o ppid= -p $$) name=$(ps -o comm= -p $parent) case "$name" in (sshd|login) exec tmux ;; esac fi
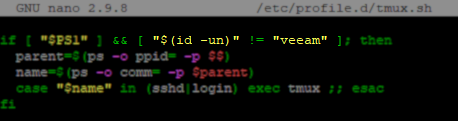
By adding a qualifier to the initial if statement to check for a specific username, it is possible to exempt a single user from having tmux start automatically. (In this example, that user account is named 'veeam'.)
if [ "$PS1" ] && [ "$(id -un)" != "veeam" ];then
parent=$(ps -o ppid= -p $$)
name=$(ps -o comm= -p $parent)
case "$name" in (sshd|login) exec tmux ;; esac
fi
If this KB article did not resolve your issue or you need further assistance with Veeam software, please create a Veeam Support Case.
To submit feedback regarding this article, please click this link: Send Article Feedback
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
Spelling error in text
KB Feedback/Suggestion
This form is only for KB Feedback/Suggestions, if you need help with the software open a support case