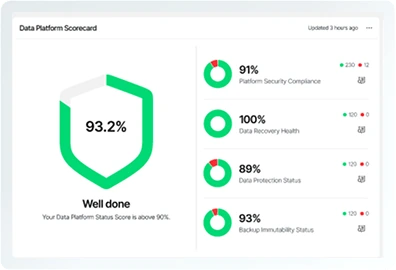
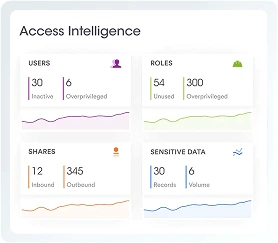
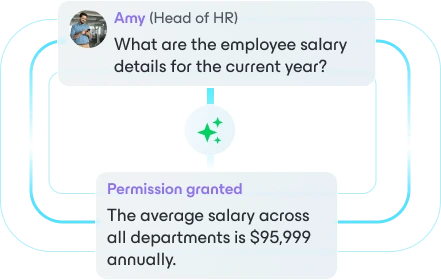
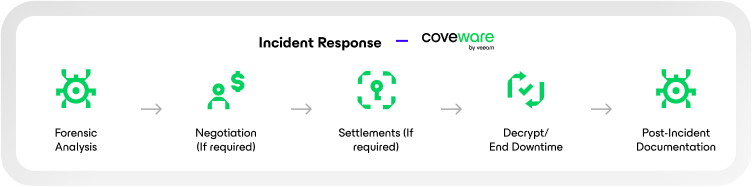
The Data Command Graph maps all your data—structured, unstructured, primary, and secondary—and provides rich context by connecting it to every identity, AI model, and system that touches it across its lifecycle.
Bring dark data into the light. Spot hidden exposure, cut ROT data, and operate with precision with one source of truth.