Key Takeaways:
- SIEM platforms collect, correlate, and analyze security data for faster, more accurate threat detection and response.
- Integration with diverse data sources, including endpoints, identity systems, cloud workloads, and backup platforms like Veeam, provides unified visibility for your SOC teams.
- Advanced analytics, threat intelligence, and machine learning enable proactive detection of ransomware precursors, anomalous logins, insider threats, and policy violations.
- Pairing SIEM with immutable backups and zero trust controls ensures you have clean, recoverable data if a cyberattack occurs.
- Compliance support: SIEM platforms delivers audit‑ready logs and dashboards to help meet frameworks like NIST CSF, ISO 27001, GDPR, HIPAA, and PCI‑DSS.
Security Information and Event Management (SIEM) is a cybersecurity solution that collects, correlates, and analyzes security data from across your IT environment to help your security operations center (SOC) detect, investigate, and respond to threats in real time.
This critical tool helps cybersecurity teams perform security operations while maintaining rapid, optimal incident response.
What is SIEM?
In the early days of IT, security was simpler; a firewall and basic access controls could keep most threats out. However, as organizations embraced cloud, mobility, and connected systems, attack surfaces expanded far beyond the traditional network edge.
As organizations become increasingly digital, their attack surfaces expand, and so does the challenge for cybersecurity teams. Today’s environments are complex, distributed, and constantly changing, making it harder to monitor activity and respond to threats. This problem is compounded by a global cybersecurity talent shortage and the growing sophistication of attackers.
Modern organizations may operate dozens of servers, applications, and cloud workloads, each accepting connections through multiple ports, ranging from file servers and databases to VPNs and collaboration tools. With so much data in motion and at rest, the risk isn’t limited to just external attackers. Insider threats, misconfigurations, and unmonitored endpoints can be just as damaging. That’s why organizations need centralized visibility, automation, and analytics to detect, correlate, and respond to incidents before they impact operations.
SIEM evolved to help security teams manage this volume of data and cybersecurity threats by correlating events across systems, simplifying investigations, and accelerating threat detection and incident response.
What are the Components of SIEM?
SIEM platforms collect, process, and analyze information about security-related events and incidents across your environment. While SIEM systems can include many moving parts, they’re generally divided into two key categories:
- Security Information Management (SIM): Centralized log management and long-term storage of security data for analysis, trend reporting, and compliance.
- Security Event Management (SEM): Real-time processing, correlation, and alerting on security events as they occur.
By combining SIM and SEM, SIEM provides full visibility, aggregating logs, telemetry, and threat data from across firewalls, endpoints, identity systems, and even data protection platforms like Veeam. It then applies analytics to distinguish meaningful security incidents from everyday noise.
How Does SIEM Integration Work?
At its core, SIEM integration is about creating unified visibility. Instead of investigating alerts across multiple tools, your SOC can access a consolidated view of your entire IT and backup environment.
Here’s how it typically works:
- Data collection:
SIEM continuously gathers log and event data from sources like firewalls, identity providers, endpoint protection, and cloud workloads. Modern SIEM solutions also integrate with data protection platforms, such as Veeam Data Platform, to include backup events in the security posture. - Normalization and correlation:
Once collected, SIEM normalizes data into a consistent format and correlates it across systems. For example, it might detect a sequence where failed logins, privilege escalation, and backup deletions occur within minutes, which could signal a potential ransomware event. - Analysis and detection:
Advanced analytics, threat intelligence feeds, and machine learning help the SIEM evaluate the context and detect suspicious behavior or policy violations. It prioritizes alerts based on severity and risk. - Response and automation:
When integrated with Security Orchestration, Automation, and Response (SOAR) tools, SIEM can trigger automated actions, such as isolating endpoints, to lock accounts or notify administrators to reduce response times and human error. - Reporting and compliance:
SIEM tools generate detailed audit logs, compliance dashboards, and incident reports to meet frameworks like NIST, ISO 27001, and GDPR. These insights help security leaders verify security posture, governance, and resilience readiness.
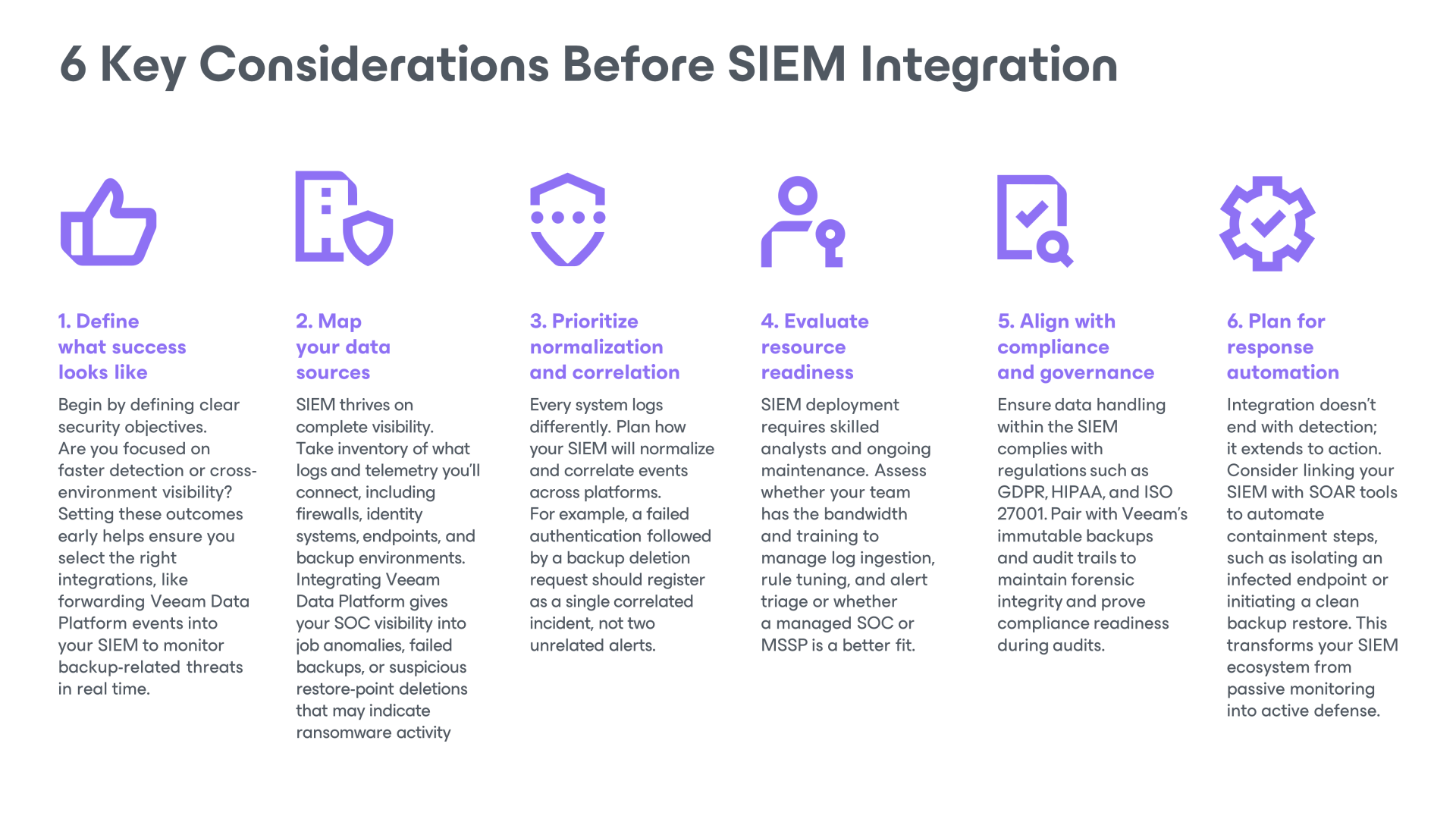
What Do You Need to Consider Before SIEM Integration
Integrating SIEM is a strategic move that defines how your organization detects, investigates, and responds to threats. Review these key areas to ensure your SIEM delivers maximum visibility and long-term value.
Fundamentals of SIEM Integration
Data Collection and Event Correlation
To build a resilient data-driven defense, your SIEM must ingest clean, well-labeled telemetry across identity, endpoints, network, cloud, and data protection layers. Normalize that data into a consistent schema so rules and machine learning can accurately detect anomalies.
| What to collect: | Authentication successes and failures, privilege changes, process starts, network flows, cloud control-plane calls, plus backup signals such as job status, restore-point creation or deletion, immutability changes, repository configuration edits, malware-detection flags, and admin actions (e.g., mass encryption detected during backup). |
| How to get it in: | Use syslog, REST APIs, agents, or cloud-native pipelines. From the data-protection side, Veeam platforms expose rich operational telemetry and alarms (e.g., from Veeam ONE and Veeam Backup & Replication) that can be forwarded to a SIEM. |
| Correlate for context: | Write rules that join backup anomalies with endpoint or identity events (e.g., detecting both a spike in encrypted file entropy and recent privileged token misuse to increase detection confidence and reduce noise). |
Proactive Threat Detection with Behavioral Analytics
Signature detections still matter, but today’s attacks evolve quickly. By layering behavioral analytics, your SIEM can recognize patterns early, before encryption or data destruction begins.
| Ransomware precursors: | Unusual file change spikes, rapid entropy increase in backup streams, deletion attempts on restore points, sudden immutability policy edits, or mass credential failures. |
| Lateral movement hints: | New service installations, suspicious remote management activity, or off-hours admin activity correlated with backup admin changes. |
| Model tuning: | Baseline “known good” behavior for each repository or workload, then alert on meaningful drift rather than static thresholds. Mapping detections to MITRE ATT&CK aids triage and reporting consistency. |
Real-Time Alerts and Dashboard Visualization
Make risk visibility instant and action-oriented
| Tiered alerting: | Route critical, time-sensitive events (e.g., restore-point deletions, repository state changes, malware flags) to on-call responders, while routine hygiene alerts flow to ticketing systems. |
| Role-based views: | Provide role-based dashboards. SOC analysts view threat signals (e.g., IOC hits, anomalous backup activity, risky restores); while IT and backup dashboards monitor resilience metrics like service level agreement (SLA) compliance, success rates, and immutability coverage. |
| Drill-downs: | Each alert should link to the raw event, correlated context (e.g., identity, endpoint, cloud), and recommended next steps. Many Veeam alarms include remediation guidance that can be surfaced inside SIEM notes. |
Integration with Existing Security Frameworks
Keep detection, response, and recovery aligned to your broader security program.
| Control mapping: | Map backup and recovery signals to frameworks like NIST CSF (Protect/Detect/Recover), CIS Controls, and MITRE ATT&CK/D3FEND so findings feed into existing governance and audit processes. |
| Policy enforcement: | Reinforces zero-trust principles like least privilege for backup admins, MFA on management consoles, change-control on repositories, and clear separation of duties. Monitor these controls through SIEM to verify continuous enforcement. |
| Evidence & audit: | Preserve configuration-change logs, restore validations (e.g., SureBackup/Secure Restore results), and incident timelines so compliance teams can export audit-ready evidence on demand. |
This alignment ensures your SIEM supports the Protect, Detect, and Recover pillars of a cyber-resilient strategy.
SIEM Use Cases
Here are a few real-world examples of how SIEM helps security and IT teams detect threats early and respond with confidence:
- Compromised accounts: If an employee logs in at the office and then logs in 20 minutes later from another state, the account is likely compromised.
- Insider threats: A privileged admin accessing systems after hours or from an unusual location could trigger a potential insider threat alert. This helps teams respond before data leaves the environment.
- Brute force attempts: Classic attack patterns like brute force, Pass the Hash, or Golden Ticket stand out clearly when correlated across authentication logs, which allows for faster detection and account lockdown
- Phishing attempts: By analyzing email, endpoint, and identity telemetry, SIEM can identify who received phishing messages and whether any links were clicked, enabling faster response and targeted user awareness training.
- Remediation following a breach: If a breach does occur, SIEM can alert administrators to unexpected configuration changes or performance spikes, which gives teams time to isolate affected systems and begin recovery.
- Malware: SIEM can monitor unusual file-access patterns or mass encryption events, which serves as an extra layer of defense that helps detect ransomware activity in progress before it reaches backup data.
What is SIEM’s Role in Compliance?
SIEM combines centralized logging and contextualized analysis to help organizations protect their systems, validate compliance posture, and detect suspicious activity tied to regulated data . While SIEM is not in itself a compliance tool, it’s dashboards provide early visibility into unauthorized access and help maintain continuous audit readiness.
Some of the most common frameworks companies are required to abide by include:
- HIPAA: Healthcare organizations governed by HIPAA can face steep fines per violation, so using SIEM to detect access anomalies and unauthorized disclosures is vital for compliance assurance.
- PCI-DSS: Financial and retail organizations must comply with PCI-DSS to ensure secure payment and cardholder data processing. SIEM supports this by monitoring access logs and transaction anomalies that could indicate breaches.
- GDPR: Organizations operating in the EU or handling EU citizen data must comply with GDPR, where fines can reach 20 million euros or 4% of annual revenue. SIEM helps organizations maintain proof of access control and breach notification compliance.
- Regional regulations: U.S. states like California (CCPA/CPRA) and other jurisdictions have their own privacy mandates. SIEM helps unify compliance visibility across these frameworks.
Organizations should map SIEM logging and reporting to the specific frameworks that are relevant to their industry and region to ensure consistent data governance across all regulatory environments.
While SIEM can’t prevent every breach, it plays a critical role in early detection and forensic investigation, thus helping limit damage, support remediation, and demonstrate regulatory diligence.
Consider the following hypothetical scenario: Your SIEM tool flags an unusual login attempt on a forgotten server. Upon investigation, your team discovers and contains a breach before data exfiltration occurs, preventing potential regulatory fines and brand damage. Without SIEM’s early alert, attackers could have lingered undetected for months, escalating the impact dramatically.
SIEM Best Practices
To get the most value from your SIEM, tailor its implementation to your organization’s environment, data sources, and workflows. Define what you’ll log, how that data will be normalized for analysis, and which tasks you can safely automate to avoid alert fatigue and keep your SOC focused on true threats.
Here are some best practices to consider:
- Clearly define your detection, investigation, and compliance objectives before deployment.
- Maintain a centralized log repository with streamlined ingestion pipelines for all telemetry sources.
- Ensure your SIEM captures all complete and relevant data from endpoint, network, identity, and data protection systems like Veeam.
- Establish clear retention policies so analysts can trace long-term patterns and support forensic investigations.
- Align logging and auditing configurations with the regulatory standards your organization must meet.
- Automate repetitive workflows wherever possible to reduce human error and accelerate response.
- Leverage APIs and platform integrations (like Veeam’s syslog and REST APIs) to unify visibility across your ecosystem.
- Train and brief all relevant staff on how SIEM integrates with your incident response playbooks.
- Reassess your SIEM rules, thresholds, and response policies regularly to stay aligned with evolving threats.
- Include immutable backup and configuration logs to ensure forensic accuracy and verify clean recovery during investigations.
Effective SIEM depends on quality data and precise tuning. Too many false positives can cause alert fatigue, so continually refine your correlation rules and response thresholds. The goal is a system that filters out noise, prioritizes true risks, and empowers your SOC to respond decisively.
Unleash the Potential of SIEM
SIEM is more than just log aggregation. It’s a proactive approach to detecting, analyzing, and responding to threats before they impact operations. Modern, next‑generation SIEM solutions now leverage machine learning and deep learning to identify abnormal behavior, correlate events across systems, and flag potential breaches in real time.
With interactive dashboards and real‑time alerts, SIEM enables security teams to quickly investigate suspicious activity, ranging from unusual login attempts to data exfiltration patterns, and take immediate corrective action. As highlighted in Your Guide to Data Resilience and SIEM Solutions, this combination of speed, visibility, and intelligence is critical for stopping cyberattacks in their tracks.
However, even the best SIEM cannot prevent every attack. When defenses are breached, you need a last line of protection: Immutable, air‑gapped backups that cannot be altered or deleted by malicious actors. This ensures you can recover clean data quickly and get operations back online.
The Veeam Data Security Ecosystem shows how pairing SIEM with immutable backups, advanced monitoring, and zero trust controls creates a complete cyber resilience strategy that both detects threats early and ensures recovery if you end up being affected. that both detects threats early and ensures recovery if they succeed.
Want to see how SIEM and data protection can work together in your environment?
Watch this demo to see our SIEM solutions in action
Related resources: