- Veeam Glossary
- What Is CryptoLocker Ransomware?
What Is CryptoLocker Ransomware?
Ransomware is a billion-dollar industry. Modern computing has a tumultuous history marred with countless viruses and malware. In recent years, bad actors began focusing on the promise of profits in the form of ransoms. By encrypting data and preventing victims from accessing it, these actors profit from those who can't afford to lose critical data.
Organizations without ransomware protection are the most vulnerable to this growing criminal industry. Veeam’s 2023 Data Protection Trends Report found that 85% of organizations across the globe had experienced at least one ransomware attack. What’s worse is that more than half of those businesses paid the ransom to regain access to data — a choice that a secure backup replica could have made unnecessary.
Many organizations simply aren’t prepared for the growing threat of ransomware. While it’s existed for more than 30 years, it wasn’t the profitable cybercrime industry it is today until about a decade ago. One of the most prominent is the CryptoLocker virus.
CryptoLocker Ransomware Explained
The emergence of CryptoLocker in 2013 marked the beginning of the scourge of ransomware. Once infected with CryptoLocker, the ransomware encrypts a victim’s files and then demands payment for the decryption key, often amounting to hundreds or even thousands of dollars.
CryptoLocker became infamous practically overnight, partly due to its powerful encryption algorithm that made data recovery without the original decryption key almost impossible. Additionally, the attackers behind the ransomware would threaten to delete the victim’s data if the ransom wasn’t paid within a specified timeframe. Due to its aggression and costly impacts, CryptoLocker remains a CISA alert. Though modern systems aren't vulnerable to the aging CryptoLocker ransomware, it pioneered the tools and strategies approach that many cyber criminals employ today.
How Does It Work?
In most cases, CryptoLocker is delivered through phishing emails that attempt to trick victims into downloading and executing the ransomware. When it first appeared, CryptoLocker attackers used emails designed to look like tracking notices from UPS and FedEx. Once a victim downloaded and ran the ransomware, it would start encrypting files on the infected system.
CryptoLocker would also attempt to spread to other computers by propagating through file systems. On vulnerable systems, it can spread to external USB drives, thumb drives and network storage, including mapped drives and cloud storage platforms.
The ransomware specifically targeted Microsoft Windows systems, many of which are still vulnerable, including:
- Windows XP
- Windows Vista
- Windows 7
- Windows 8
Once CryptoLocker begins infecting one of these systems and propagating, it locks files using RSA public-key encryption. This approach utilizes two sets of ciphers for encrypting and decrypting data, which is far more secure than a single key method when sharing and transmitting data. At the time, asymmetrical encryption was less common for legitimate use, let alone in ransomware.
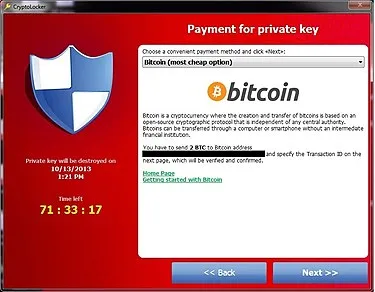
History
When it emerged in September 2013, CryptoLocker caused significant damage, impacting systems and data across the globe. Unprecedented in its effectiveness and high monetary demands, CryptoLocker became infamous overnight. The actors behind this new threat were the GameOver ZeuS gang, a cybercrime gang notorious for using the ZeuS trojan to steal banking credentials.
At that time, CryptoLocker became one of the most effective and nefarious forms of ransomware, emblematic in this history of ransomware case study. The method drew the attention of authorities for its ability to encrypt a victim’s data using strong encryption methods, which was unheard of for ransomware at the time. The extortions were also much higher than conventional ransomware demands, amounting to hundreds or even thousands of dollars. To make matters worse, part of CryptoLocker’s strategy was threatening the deletion of files if the ransoms weren’t paid.
Within months, CryptoLocker caused serious disruption to businesses and government agencies, many of which were forced to pay ransoms to regain data access. It wasn’t until June 2014 that a U.S.-led multinational operation overthrew the GameOver ZeuS botnet. Known as Operation Tovar, the international crackdown happened simultaneously across several countries.
CryptoLocker might have been the incident that put ransomware in the spotlight, effectively drawing the focus of cybercriminals across the globe.
Is CryptoLocker Still a Threat?
Although Operation Tovar neutralized the attackers responsible for the original CryptoLocker ransomware and significantly lowered the number of attacks, new variants have emerged in the following years. Individuals and organizations without proper measures in place to mitigate or offset ransomware attacks are still vulnerable.
These days, the descendants of CryptoLocker are more disruptive and damaging. Many rely on new distribution methods and encryption techniques, making it increasingly difficult to detect and prevent attacks that utilize them. In many cases, the attackers behind these attacks demand much higher ransom payments accompanied by more intense threats. Locky, WannaCry and Petya are some of the newest variants.
It’s also common for these attacks to demand payment in Bitcoin and other cryptocurrencies, which was another pioneering move by CryptoLocker. The rise of cryptocurrency has made it easier to demand and receive ransom payments anonymously, which adds to the appeal of ransomware attacks for cybercriminals.
How to Mitigate CryptoLocker
Ransomware poses a significant threat to any system that accesses or stores critical data. Without secure backups, data is continuously at risk since ransomware is often difficult to spot until it’s too late. The same goes for CryptoLocker, which is difficult for most tools to detect until it’s already encrypted data.
Organizations can mitigate the threat of CryptoLocker by ensuring all systems are using the latest operating systems, though this won’t necessarily protect from newer CryptoLocker variants. Companies need a multifaceted approach that includes strategies encompassing network security, account management and continuous monitoring. Most importantly, they need a dependable and secure backup strategy in the event of infection.
Detection
The first step in mitigating CryptoLocker is to detect any signs of an attack as early as possible. Some ways individuals monitor for signs of ransomware threats like CryptoLocker include:
- Close monitoring of network traffic for suspicious transfers
- Checking system logs regularly for unusual processes or activity
- Using security software to detect and block ransomware-related processes
Meanwhile, most attackers attempt to infect victims with ransomware via phishing emails, so a strange or suspicious email with an attachment could indicate an attack. For this reason, vigilance in email management is the most reliable defense against ransomware.
Prevention
The first and perhaps most important step to mitigate CryptoLocker is to ensure systems stay updated with the latest patches, fixes and updates, including the operating system, any applications and security software. Organizations should focus on preventative measures such as:
- Implementing strong access controls and user permissions to limit the impact of vulnerabilities
- Using strong email policies and security systems to block malicious emails and filter suspicious attachments
- Educating employees on recognizing and avoiding common phishing attacks
Lastly, the most effective way to protect against ransomware data loss is by implementing a sound backup strategy. Even highly secure systems and networks are compromised by ransomware attacks. In this sense, the only real prevention is avoiding the possibility of data loss.
Removal
If a CryptoLocker attack does occur, it’s important to prevent the spread of the ransomware by completely disconnecting the infected system from any networks and shared storage devices. Rapid removal of the malware is paramount to prevent any further encryption.
The steps to remove CryptoLocker include:
- Isolate the infected systems to prevent the malware from spreading, including any systems that could have been impacted
- Safely remove the malware from the system with reputable security tools
- Conduct thorough scans on the systems within the sphere of impact
- Restore affected files from a secure backup
- Report the incident to the Internet Crime Complaint Center, or IC3, a division of the FBI
Catching CryptoLocker early in the encryption process can mitigate any data damage it causes, and removal of the malware itself is relatively easy. But it’s worth noting that any files that were encrypted prior to detection aren’t recoverable.
Recovery
Decrypting and recovering infected files from CryptoLocker or other types of ransomware is exceedingly difficult. Victims have no access to the key necessary to access encrypted data. Since this kind of malware uses strong encryption keys, breaking the cipher is nearly impossible. In a few cases, it’s possible to use tools developed by cybersecurity firms to decrypt files. These tools exploit vulnerabilities in the encryption algorithm and provide decryption keys that victims can use to decrypt data.
The only reliable method of fully recovering from a ransomware attack, regardless of the variant used, is a secure backup. By establishing a secure backup routine, if the worst comes to pass, recovery is complete and expedient.
How Veeam Can Help
From day one, the most effective ransomware solution is a data backup strategy. Veeam’s secure backup and recovery tools are built with this in mind, helping enterprises and individuals protect valuable and critical data from ransomware threats of any variety.
Using Veeam’s powerful and secure solutions ensures data is always safe, regardless of the effectiveness of the attacks that emerge from the cybercrime underworld. Veeam solutions are comprehensive in their protection, providing robust backup and encryption tools across multiple platforms, including on-premises, hybrid and cloud environments, ensuring your data is safe and available, no matter where you store it.