How to Review Password Requirements of Veeam Software Appliance
Purpose
This article documents how to review the specific password requirements for a Veeam Software Appliance.
Solution
The Veeam Software Appliance adopts the DISA STIG password requirement standard. These password requirements may change between releases and as part of OS updates.
View Current Password Requirements
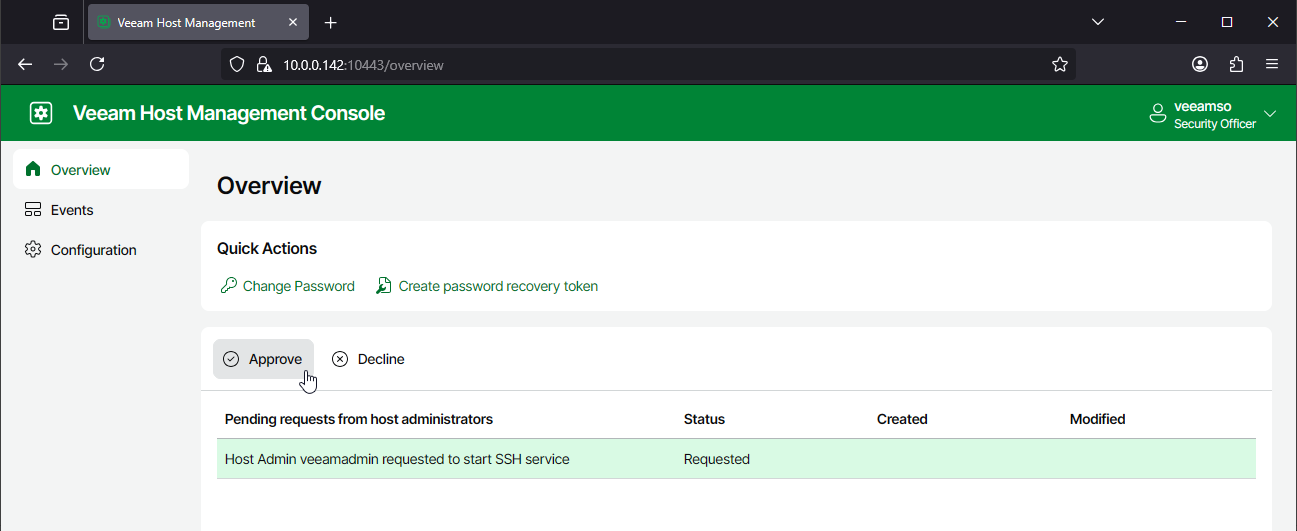
- Log in to the Veeam Host Management Console (port 10443) using a Host Admin account (e.g., veeamadmin).
- Switch to the Remote Access section.
- Click the toggle for SSH Server.
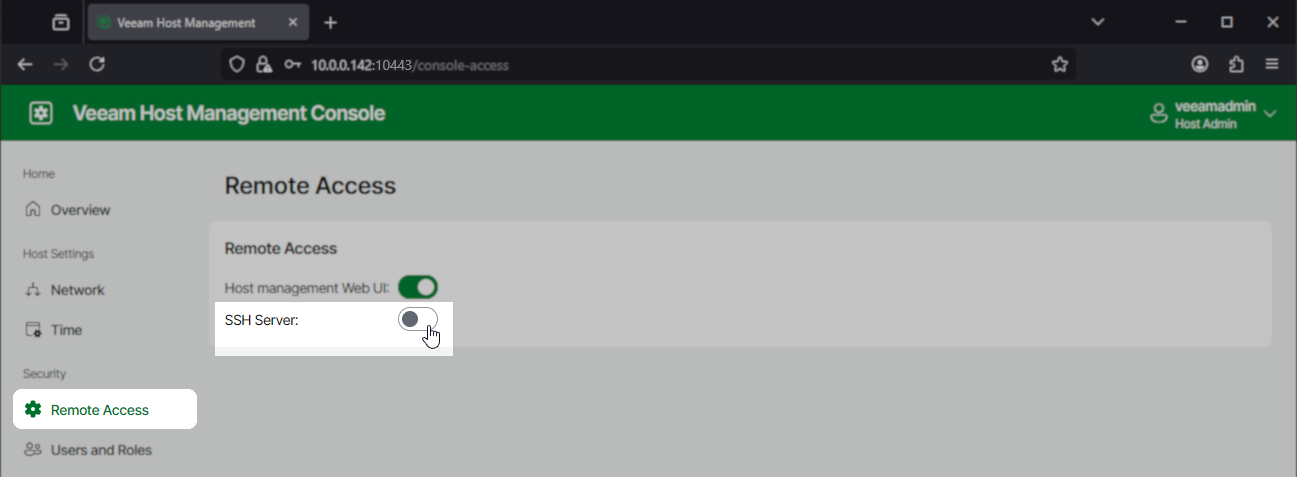
- If the Security Officer role is enabled, you'll see a pop-up stating, "Request has been submitted to Security Officer."
If the Security Officer role was disabled during initial deployment, skip to Step 6.
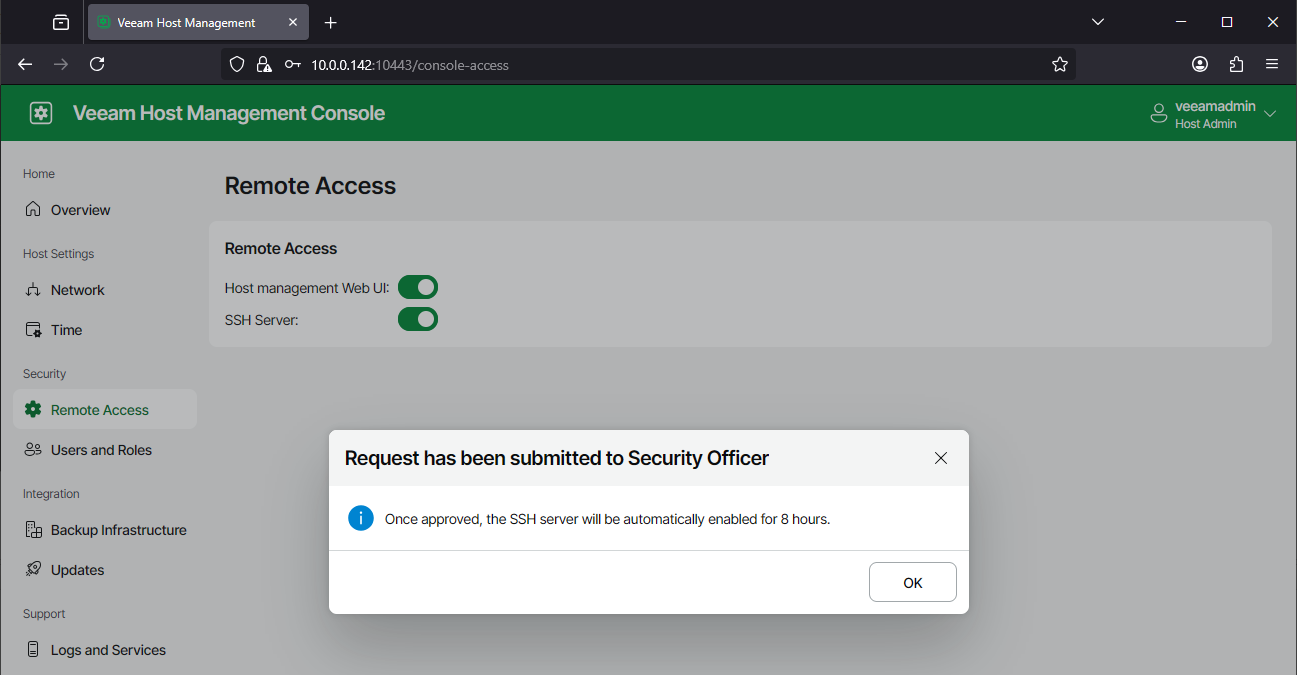
- Have the Security Officer log in and approve the SSH request.
"Host Admin veeamadmin requested to start SSH service."
- With the SSH service now started on the Veeam Software Appliance, connect to it using an SSH client.
- Review the following files:
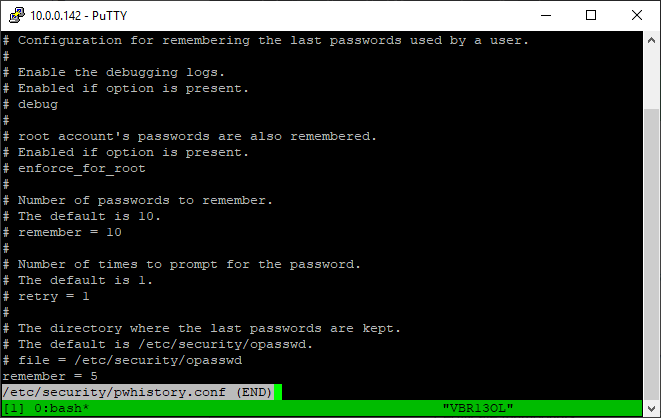
- /etc/security/pwhistory.conf
- /etc/security/pwquality.conf
More Information
Please note that some settings are appended to the end of the configuration files, and the explanations of these settings and their default values remain, but are commented out.
As of 2025-12-30, the default content of those files is as follows:
pwhistory.conf
pwquality.conf
If this KB article did not resolve your issue or you need further assistance with Veeam software, please create a Veeam Support Case.
To submit feedback regarding this article, please click this link: Send Article Feedback
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
Spelling error in text
KB Feedback/Suggestion
This form is only for KB Feedback/Suggestions, if you need help with the software open a support case