Key Takeaways:
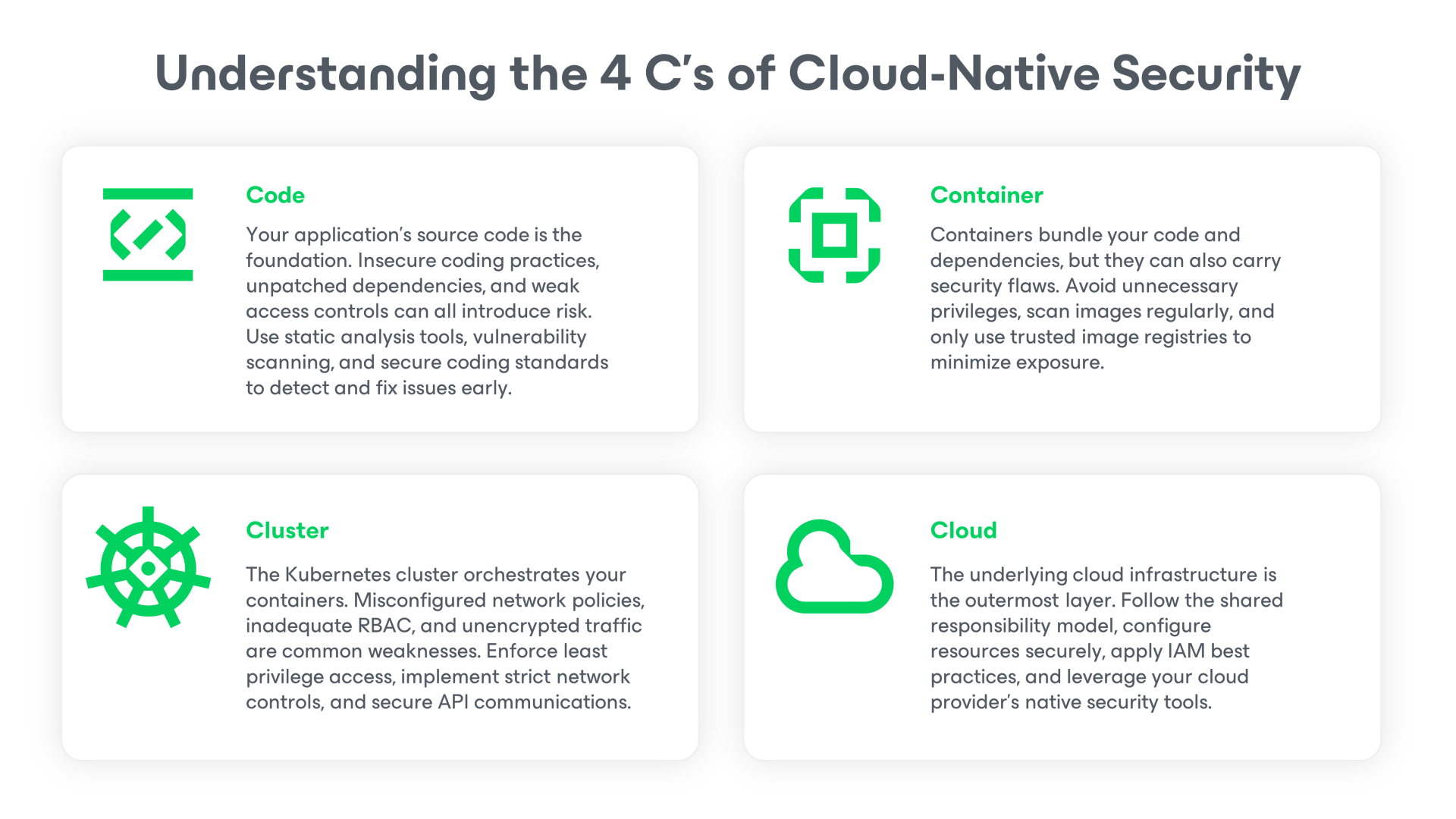
- The 4 C’s of cloud-native security: Code (e.g,. secure coding, patch vulnerabilities), Container (e.g., scan images, limit privileges), Cluster (e.g., RBAC, network policies, encryption), and Cloud (e.g., IAM, secure configurations, provider controls).
- Secure by design. Apply security controls from the start of development through deployment.
- Harden access controls. Use role-based access control (RBAC), enforce least privilege access, and integrate with identity providers for authentication.
- Protect workloads in motion and at rest. Encrypt traffic, secure container images, and scan for vulnerabilities.
- Monitor and respond in real time. Implement runtime security and anomaly detection to catch threats quickly.
- Ensure data resilience. Combine security measures with Kubernetes-native backup and recovery solutions like Veeam Kasten for full protection.
What is cloud-native security as it applies to Kubernetes? Cloud-native security is a modern way to protect applications that’s designed specifically for cloud environments. These applications often use containers and microservices, which help make them flexible and scalable.
How does cloud-native apply to Kubernetes-native, what is Kubernetes-native, and how is it different from cloud-native? When it comes to Kubernetes, which is a popular system for managing containers, cloud-native security means applying practices that fit the unique way Kubernetes organizes and runs these containers. It’s about protecting the whole environment while keeping up with its fast-paced, dynamic nature.
These solutions leverage the unique features of Kubernetes, such as its APIs, orchestration capabilities, and extensibility, to provide enhanced security and operational efficiency that traditional tools often cannot match.
While Kubernetes-native solutions align closely with cloud-native principles that emphasize agility, scalability, and flexibility in application deployment, they focus specifically on the nuances of Kubernetes architecture. In contrast, cloud-native encompasses a broader range of technologies and methodologies, including microservices, containers, and serverless computing, that can operate across various platforms and environments.
Although the advantages of cloud-native architectures, such as increased speed, scalability, and portability, are well recognized, securing these environments necessitates a departure from conventional security models. Traditional security tools frequently fall short when addressing the unique challenges posed by cloud-native deployments, particularly those orchestrated by Kubernetes. In these environments, workloads are highly ephemeral, which means containers can be created, scaled, or terminated in seconds, and dynamic, with IP addresses, node assignments, and configurations constantly changing. This rapid churn makes static, perimeter‑focused security approaches ineffective, since they cannot track or enforce policies consistently across short‑lived resources. Effective protection needs tools that integrate directly with Kubernetes’s orchestration layer, thus applying security controls that can adapt in real time.
What Are the 4 C’s of Cloud-Native Security?
A practical way to approach Kubernetes and cloud-native protection is through the 4 C’s framework. It’s a layered model that effectively addresses vulnerabilities from the inside out.
By understanding and securing each layer, you can prioritize security controls where they will have the most impact and build a resilient Kubernetes environment that is protected against threats from code to cloud.
Security in Design
Cloud Provider Considerations
- The shared responsibility model: Understand that even with managed Kubernetes services like EKS/GKE, you are still responsible for securing your applications and data.
- Leverage native features: Cloud providers offer powerful security tools like IAM, network security groups, and encryption services. Integrating your security solution with these features further strengthens your posture. For instance, your backup and recovery solution could leverage cloud provider IAM roles to ensure that your backups are protected by strict access controls.
Security Beyond the Container
While protecting individual containers is vital, a comprehensive cloud-native security strategy must consider your entire supply chain and your cloud environment’s role as well.
Secure Supply Chain
- Trusted registries: Use only private registries or trusted public ones with rigorous security checks. Ensure that your container images come from known and verified sources to prevent supply chain attacks.
- Image provenance: Track the origin and history of your images. This provides valuable context in the event you find vulnerabilities or evidence of potential tampering.
- Workflow integration: Your security solution should seamlessly integrate with your image build and deployment processes for continuous verification. It should also provide the tools you need to scan for vulnerabilities and enforce policies before an image even reaches production.
Security in Development
Proactive Security: The “Shift Left” Approach
In cloud-native environments, security can’t be an afterthought. The most effective approach is “Shift Left,” which means integrating security directly into your development and deployment pipeline (i.e., DevSecOps). This means security becomes a shared responsibility throughout the entire software lifecycle.
- Embed security in development: Incorporate vulnerability scanning early in your image-building process to catch and fix issues before they hit production. Enforce secure coding standards and ensure the use of approved and trusted container images.
- Policy-driven protection: Define clear security policies that govern aspects like RBAC, network segmentation, encryption, and resource usage. Then, utilize tools that automatically enforce these policies across your clusters and applications. This provides consistency, reduces human error, and adapts protection methods as applications scale and change.
Benefits of Automation and Consistency
- Minimized risk: Prevents common vulnerabilities and misconfigurations from ever being introduced.
- Faster deployment: Frees your teams from manual security checks and accelerates release cycles.
- Scalability: Consistent policies maintain security postures even as your environment grows in complexity
Safeguarding the Application Context
Think of the application context as a complete snapshot of how your workloads are running in Kubernetes. It’s not just the data, but the configuration details, resource dependencies, and relationships between components. In cloud‑native environments, these elements are ephemeral and dynamic: Containers can be created, moved, or terminated in seconds, and service endpoints can change constantly. Capturing that context is essential for both recovery and security.
- Disaster recovery: In any outage, whether it’s a cyberattack or a storage failure, preserving the application context enables rapid, precise restores. You can recover not just the data, but also how the application was configured, connected to other services, and deployed across the cluster. This means less downtime and a smoother return to normal operations.
- Security response: Tracking the application context over time helps identify anomalies that could signal a breach. For example, detecting an unexpected change to a container image configuration can trigger immediate investigation and containment before attackers gain a foothold.
By protecting the full application context, Kubernetes‑native data protection solutions like Veeam Kasten provide recovery and security workflows can keep pace with the speed and volatility of modern cloud‑native environments.
Security in Production
Resilience Against Attacks
Ransomware is one of the most critical threats to Kubernetes environments and targets the very heart of your data and applications. Building a defense against these attacks must be a central pillar of your cloud-native security strategy.
- Ransomware defense: Immutable and air-gapped backups
- Immutable backups: These backups cannot be altered or deleted, even by attackers who gain access. This guarantees a clean recovery point.
- Air-gapped backups: Storing backups offline or in isolated environments protects them from network-based attacks and insider threats.
- Beyond just data: Application-centric recovery
- Restoring data alone is not enough. Your solution must be able to restore applications with their configurations, dependencies, and metadata intact. This minimizes downtime and ensures a full recovery.
The Power of the Right Tools
Purpose-built cloud-native security solutions provide specialized capabilities and integrations that maximize your protection while streamlining operations. Look for the following hallmarks:
- Ecosystem integrations: Your solution should complement — not replace — best-in-breed security tools. Seamless integration with monitoring solutions, threat detection engines, and policy enforcement frameworks amplifies visibility and enables more comprehensive protection. Ideally, your solution should help you orchestrate and automate workflows, like blocking the deployment of a vulnerable image if flagged by a scanner.
- Compliance through design: Achieving compliance in regulated industries (e.g., healthcare, finance) requires specific features. Look for end-to-end encryption both at-rest and in-transit and find fine-grained access controls, comprehensive audit trails, and reporting too. A Kubernetes-aware solution should understand how to meet these requirements within the complex landscape of cloud-native environments and make compliance easier to maintain.
- Deep Kubernetes expertise: Cloud-native environments are intricate. Opt for a solution that’s built by a team that deeply understands Kubernetes architecture, common attack vectors, and evolving threat landscapes. This expertise translates into features that are designed to protect the unique components of Kubernetes and the support you need to confidently address vulnerabilities and quickly adapt your security strategy as usage evolves.
Cloud-native security demands a fresh perspective. A proactive approach that uses policy-driven automation and prioritizes ransomware resilience can significantly strengthen your Kubernetes environment’s defenses. These defenses span the lifecycle of Kubernetes applications from design through to production. After reading this blog, you should have a general idea of key elements that should be included in a security plan that’s intended to protect your cloud-native environments.
Experience the power of purpose-built Kubernetes protection first-hand! Start your free Veeam Kasten trial today and see how easy it is to implement proactive security, ransomware resilience, and application-centric backups.
How Veeam Supports Cloud-native Security for Kubernetes
Veeam Kasten, formerly known as Veeam Kasten, is one of Veeam’s solutions for Kubernetes environments. It is a data management platform that’s specifically designed for Kubernetes and provides data backup, recovery, and application mobility capabilities for both cloud-native and on-premises deployments. Veeam Kasten focuses on providing data protection and compliance for stateful applications that run on Kubernetes.
Veeam Kasten offers the following features for Kubernetes-based data management:
Backup and recovery: Facilitates the backup and recovery of Kubernetes applications, including their persistent volumes and associated metadata. Veeam Kasten also supports various storage options and can back up data from multiple clusters, namespaces, or individual applications.
Application mobility: Allows users to move Kubernetes applications seamlessly across clusters or cloud providers. It provides a consistent approach to migrating or replicating applications to ensure data portability and disaster recovery (DR) readiness.
Policy-based automation: Enables the creation of policies to automate data management tasks like backups, snapshots, and restorations. These policies can be defined based on specific criteria, such as namespace, labels, or schedules.
Application-centric operations: Provides a user-friendly interface to manage and monitor your data protection and management operations. Veeam Kasten also offers visibility into application-level metadata, allowing you to easily search, browse, and restore data.
Veeam Kasten focuses on providing comprehensive data management capabilities for Kubernetes environments by ensuring data protection, application mobility, and automation. It is specifically built to address the unique requirements of cloud-native deployments.
Protect Kubernetes from code to cloud. Try Veeam Kasten free and see how application‑aware backups and ransomware‑proof recovery keep you running no matter what.
FAQs
1. What is cloud-native security in Kubernetes?
Cloud-native security in Kubernetes is the practice of protecting applications, containers, clusters, and cloud infrastructure in a Kubernetes environment using security controls designed for dynamic, distributed systems. It covers securing the application code, container images, Kubernetes configurations, and the underlying cloud platform.
2. How do you secure a Kubernetes cluster?
To secure a Kubernetes cluster, apply layered controls across code, container, cluster, and cloud:
- RBAC and least privilege for access control
- Network policies to restrict pod-to-pod communication
- Secrets encryption and secure API communication
- Regular vulnerability scanning of images and configurations
- Audit logging to track changes and detect anomalies
Security should be enforced from development through production and follow the 4 C’s framework.
3. What are the biggest security risks in Kubernetes?
The biggest Kubernetes security risks include:
- Misconfigured RBAC that allows excessive permissions
- Unsecured container images with vulnerabilities or malicious code
- Lack of network segmentation that expose workloads to lateral movement
- Unpatched clusters that are vulnerable to known exploits
- Leaked secrets in code repositories or environment variables
4. What is shift-left security and how does it apply to Kubernetes?
Shift-left security means integrating security checks earlier in the development process instead of waiting until deployment. In Kubernetes, this involves:
- Scanning container images for vulnerabilities before pushing them to a registry
- Validating YAML configurations against security policies
- Embedding security tests into CI/CD pipelines
5. How do you protect container images from vulnerabilities?
You can protect container images from vulnerabilities by starting with trusted base images from verified sources and keeping them as minimal as possible to reduce the attack surface. Regular image scanning with security tools helps detect known vulnerabilities early, while timely updates to dependencies and packages ensure that images remain secure. Signing container images before deployment adds an extra layer of verification, ensuring only validated and uncompromised images run in your Kubernetes environment.