Veeam Availability Suite consists of two components— the Veeam Backup & Replication we all know and love, and Veeam ONE, our powerful monitoring and analytics solution. Since Veeam Backup & Replication is so powerful and feature-rich, it can very easily overshadow the unique capabilities of Veeam ONE. And with over 145 pre-built reports and 340+ individual alarms, some Veeam ONE users get overwhelmed by the number of capabilities they have at their disposal and therefore occasionally overlook and miss out on critical capabilities they can use daily to help better manage the health and wellness of their datacenters.
So, as a reminder, now and then, I like to highlight certain Veeam ONE features you can leverage to be proactive when it comes to identifying threats that could significantly impact the integrity of your data. This leads me to one of the most common threats that is the catalyst for many sleepless nights of datacenter professionals today ― ransomware.
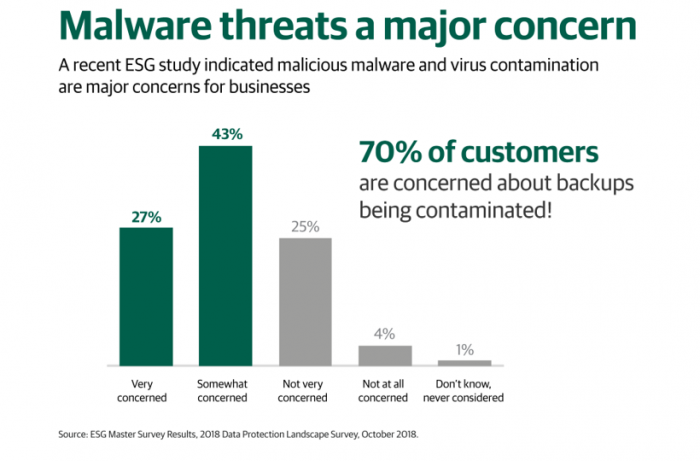
Unfortunately, for the foreseeable future, ransomware is here to stay. In fact, if anything, you can expect attacks to not only increase in volume but also in complexity as malicious actors work to prey on unprepared businesses with new variants of attacks appearing almost daily. And the threat and concern are real. Recently, ESG conducted a study that found that 70% of our customers are concerned about their backups being contaminated.
With this in mind, it’s important to recognize the tools you already have in your arsenal to help identify abnormal activity occurring in your data center that may alert you to the presence of malware. Veeam ONE can help detect this activity allowing you to be proactive when working to neutralize a ransomware attack. Let’s take a closer look.
Leveraging Veeam ONE to help combat ransomware
Veeam ONE is a great tool to utilize when it comes to providing visibility into your virtual, physical and backup environment. It can notify you if any of your backups have failed or if they backed up with a warning, allowing you to quickly address and fix the issue. Having a backup to restore from, especially after being hit by a ransomware attack is essential because ultimately, having access to a malware-free copy of your data is the best way to recover from an incident.
With all the ransomware buzz in the industry, we should all consider tips that can help prevent ransomware from infecting all of our files. One obvious solution is to closely monitor your environment and be aware of any suspicious or abnormal activity. When monitoring activity in your environment you should already be familiar with what is normal behavior and what is not. One way Veeam ONE can help notify you there is suspicious activity occurring in your datacenter is through the Possible Ransomware Activity alarm.
By analyzing CPU usage, datastore write rate, and network transmit rate, Veeam ONE can help you identify if there are higher than normal amounts of activity on a particular machine. When the alarm is triggered, this immediately notifies you to inspect the machine, look at the resource counters and determine for yourself whether or not the activity is normal. If it’s not normal, this is a good indicator that more steps should be taken to determine if ransomware is the culprit.
As I’m sure you noticed, this alarm includes the word ‘possible.’ This is because it tracks indirect signs of ransomware — typical activities and behavior we have seen that occur in a datacenter when malware is present. By analyzing CPU usage, disk I/O and network activity, it can be beneficial in identifying a “potential” ransomware attack. However, if you have a machine that normally experiences a high resource usage, such as a database server, it can trigger the alarm during times of busy activity. In this case, you can easily modify the alarm to be excluded during specific time periods when the machine typically experiences high activity or edit the resource thresholds to be more suitable for your environment.
When using this alarm, a capability you can use to supplement your efforts is setting a remediation action. Remediation Actions were introduced with Veeam ONE 9.5 Update 4 and enable you to set a predefined action or run a custom script when an alarm is triggered. In this case, for the Possible Ransomware Activity alarm you could set the remediation action to run a custom script separating the infected machine from other computers on the network, move the machine from shared storage or power off the machine. The action can be set to happen automatically or manually when the alarm is triggered based on warning or error alerts. This can be configured in the alarm settings, under the actions tab.
With Veeam ONE you can also create alarms based on tasks, event performance counters and in-guest processes and services. You can create rules based on these counters to help identify abnormal activity occurring in your virtual environment. For example, when monitoring applications, you can create alarms based on the services and processes running in the VM. If one or more services are added, the alarm can be triggered to notify you. This could be an unwanted service running or unauthorized software install which could be an indicator of a possible ransomware service on the VM.
To create an alarm, start in the alarm management tab of Veeam ONE Monitor. From there, choose an object type you want the alarm to apply to, whether host, cluster, virtual machine, etc. Object types are listed on the left side of the monitor. In this example, we are going to choose to apply the alarm to virtual machines. After selecting the object type, go to the Actions pane and select “New.” From there you will be able to choose an alarm name, create rules, assign the alarm based on your infrastructure or business view groups, establish actions when the alarm is triggered and set up notifications.
Closely monitoring the change rates on your VMs is another means to detect abnormal activity. If there is a high change rate being experienced on one of your backups this could indicate a potential threat. So how does Veeam ONE detect this? There are a few reports you can run and analyze.
One particularly helpful report is VM Change Rate History, which can be run daily to identify how your VMs are changing based on the amount of data that has changed after its been read from the virtual disk. The report looks at the changes occurring on the VM disks to provide information on the backup’s total incremental changes and file size. If there is an abnormal change occurring during an incremental run of a backup job, this is a red flag that should be examined more closely. Along with this report, the Veeam Backup Files Growth report will show you the total space used by the backup file. This report identifies the backup file type, whether full or incremental and then also the restore point’s size. This report is good to run when it comes to capacity planning for Veeam repositories but can help with recognizing any unusual activity occurring on a machine. By taking a look at the size of the restore point, you can tell if the change rate of this machine, or the backup file growth, is abnormal or higher than usual. This can be an indicator that you should take a closer look at this particular machine.
One obvious way organizations recover from a ransomware attack is restoring from a backup, but what if your last backup failed or a VM wasn’t backed up at all? Veeam ONE has ways to identify this through a couple of features to ensure the latest copy of your data is safe and secure. When it comes to staying vigilant and informed on the status of your backups, the VM with no backups alarm can be leveraged to notify you if a backup is not meeting your recovery point objectives. An additional report, the Protected VMs Report, also comes in handy to let you know which machines are protected and which lack a backup. The Job History Report provides an overall view of all the jobs running in your environment and gives detailed statistics based on these jobs.
Veeam ONE ― your first line of defense
With ransomware and malware activity on the rise, Veeam ONE is the perfect first line of defense that will help alert you to many of the classic warning signs associated with malicious activity within your datacenter. From helping detect suspicious activity to notifying you if one of your VMs is not backed up properly, Veeam ONE provides a comprehensive view of your entire IT environment that can help you be proactive in maintaining a healthy data center.
Try Veeam ONE Free for 30-days!
Ready to give it a try? Try Veeam ONE Free for 30-days and experience clear visibility into your entire IT environment while safeguarding the data that is critical to your business. Download the trial now!
Related content:
- Identify and protect yourself against ransomware
- Try our Ransomware Prevention Kit
- Read Beat ransomware. 3 Ultimate strategies white paper
- Watch 3 Ultimate Strategies for Ransomware Prevention webinar
- Read our How Should Companies Handle Ransomware? blog