Azure Storage Account Key Security Advisory
Purpose
Cause
The ListKeys permission allows "control plane" users, who are not supposed to be able to modify data, to list access keys. These access keys can then be used to read and write data to the storage accounts. An example of a role with the ListKeys permissions is Storage Account Contributor.
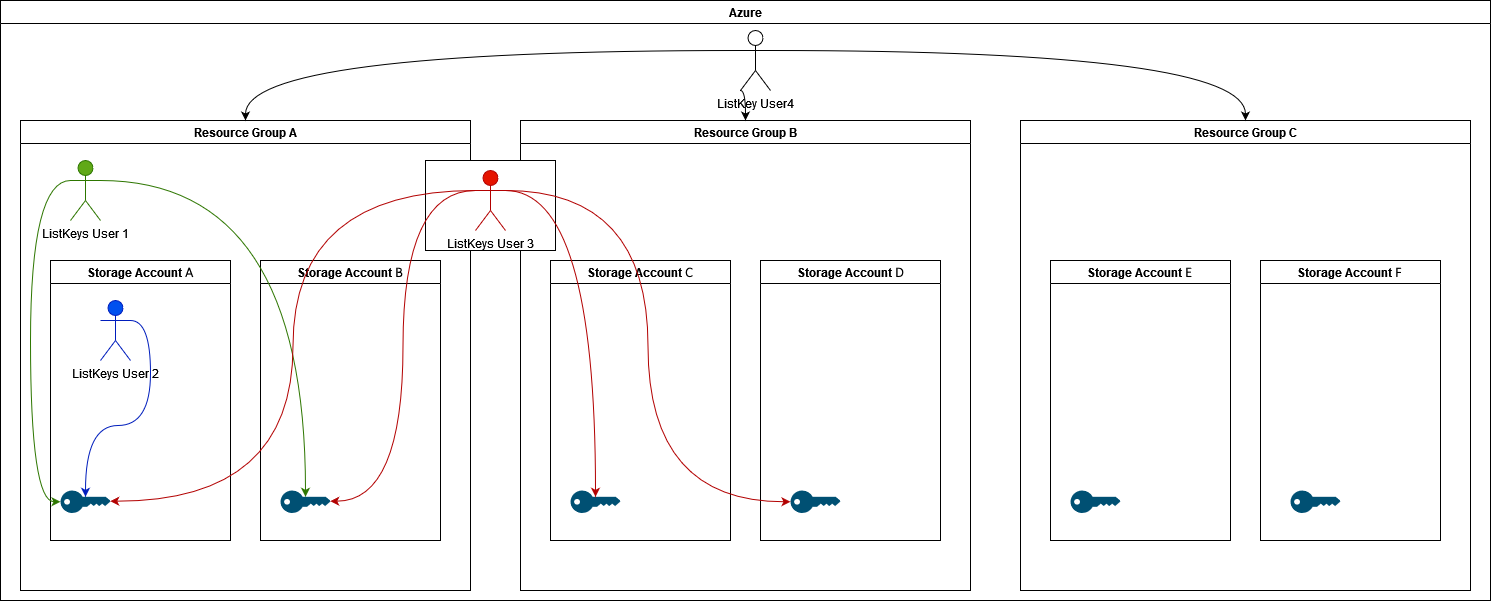
Example Diagram:
- User1 belongs to Resource Group A and can list all keys within that Resource Group.
- Storage Account A
- Storage Account B
- User2 belongs to Storage Account A and can only list the key for that Storage Account.
- Storage Account A.
- User3 belongs to Resource Group A and Resource Group B. and can list all keys within both groups.
- Storage Account A
- Storage Account B
- Storage Account C
- Storage Account D
- User4 is a top-level account and can list Keys within all Resource Groups.
- Storage Account A
- Storage Account B
- Storage Account C
- Storage Account D
- Storage Account E
- Storage Account F
Solution
We strongly encourage customers to review:
- Best practices regarding Azure Storage Keys, Azure Functions, and Azure Role Based Access
- Recommended Actions for Customers
Veeam's Additional Recommendations:
- Limit the number of users that have access to your storage accounts.
- Storage accounts used to store sensitive data should be placed in separate resource groups.
More Information
- Microsoft Documentation — Best practices regarding Azure Storage Keys, Azure Functions, and Azure Role Based Access
- Microsoft Documentation — Recommended Actions for Customers
- Orca Security — From listKeys to Glory: How We Achieved a Subscription Privilege Escalation and RCE by Abusing Azure Storage Account Keys
If this KB article did not resolve your issue or you need further assistance with Veeam software, please create a Veeam Support Case.
To submit feedback regarding this article, please click this link: Send Article Feedback
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
Spelling error in text
KB Feedback/Suggestion
This form is only for KB Feedback/Suggestions, if you need help with the software open a support case