Unable to Interact with Some Hypervisors and Cloud Platforms
| KB ID: | 4687 |
| Product: |
Veeam Backup & Replication | 12.2 | 12.3 | 12.3.1 | 12.3.2 | 13 Veeam Backup for Nutanix AHV Veeam Backup for AWS Veeam Backup for Microsoft Azure Veeam Backup for Google Cloud Veeam Backup for Oracle Linux Virtualization Manager and Red Hat Virtualization Veeam Kasten for Kubernetes Veeam Plug-In for Proxmox VE Veeam Plug-in for Scale Computing HyperCore |
| Published: | 2024-11-19 |
| Last Modified: | 2026-02-05 |
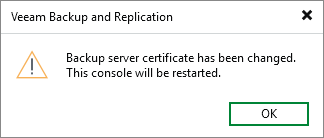
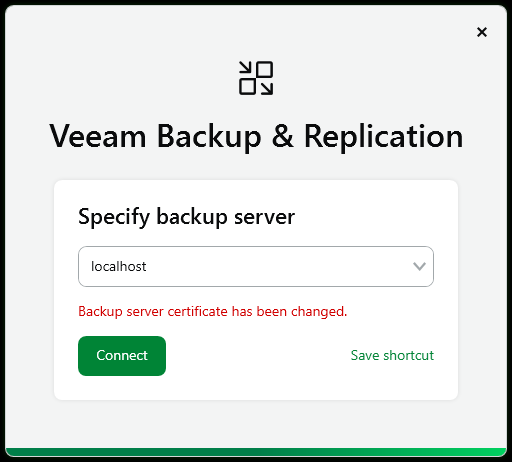
During the upgrade to Veeam Backup & Replication 13.0.1 or higher, the following warning may be displayed:
Incompatible backup server certificate The certificate does not support child certificates creation and must be replaced for virtualization and cloud plug-ins to function, see KB4687 for instructions.
The resolution for this issue can be found below in the section:
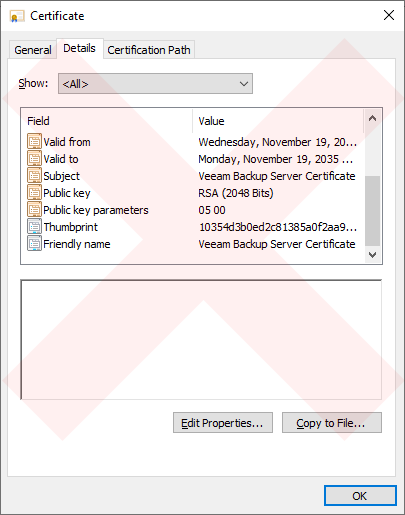
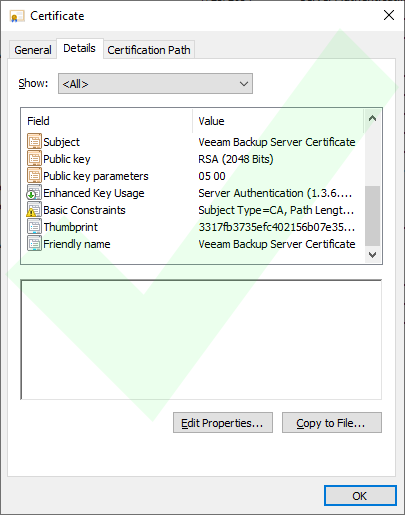
Issue 2: The Veeam Backup Server Certificate is missing the field "Basic Constraints".
Challenge
After deploying or upgrading to Veeam Backup & Replication 12.2 or higher, Veeam Backup & Replication may be unable to communicate with Virtualization and Cloud Platforms that are added to Veeam Backup & Replication via a Plug-In module (i.e., Nutanix AHV, Red Hat Virtualization, and Oracle Linux Virtualization Manager, Veeam Backup for AWS, Veeam Backup for Google Cloud, Veeam Backup for Microsoft Azure).
For Virtualization Platforms, this behavior will manifest as an inability to see these platforms listed when attempting to add them to Veeam Backup & Replication (as shown below).
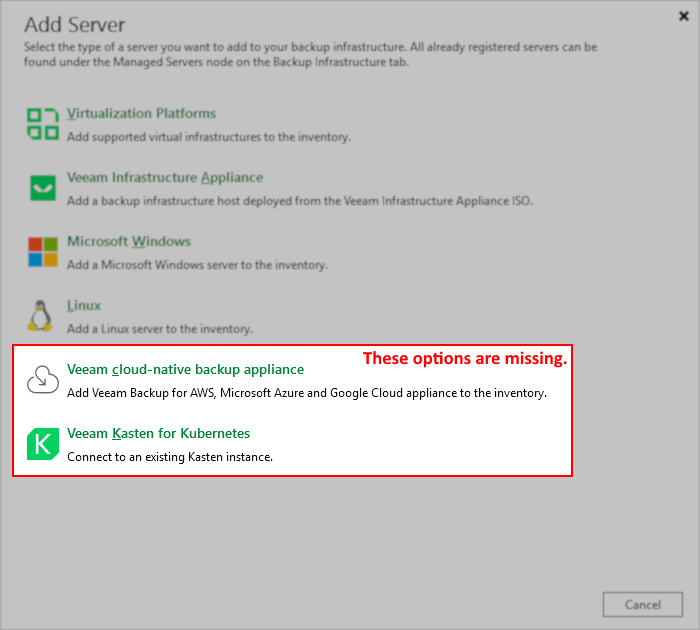
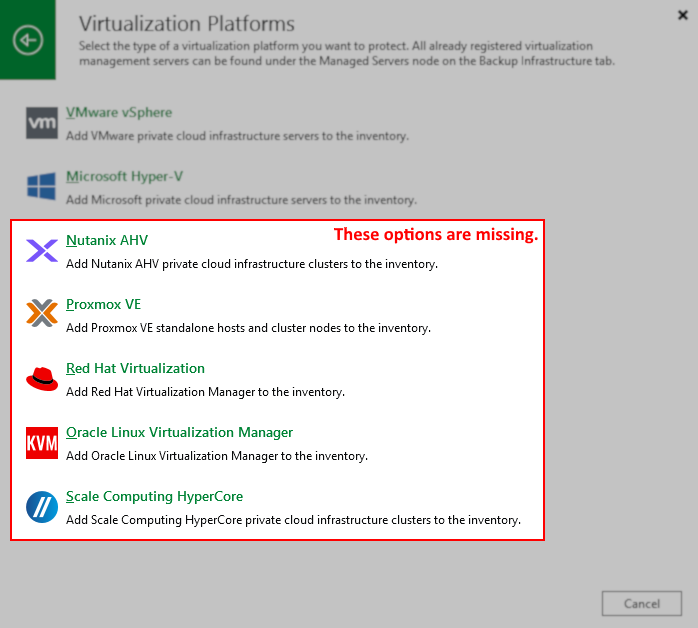
Solution
Starting with version Veeam Backup & Replication 13.0.1.180, there are three identified possible causes for this problem.
Please review each issue's description, which details the logs to check, the specific error to look for, and provides an expandable section with the solution.
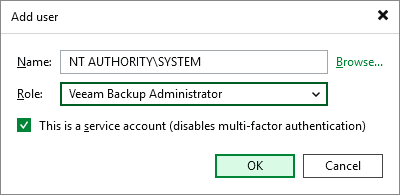
Issue 1: MFA Blocking Platform and Cloud Plug-Ins
- Related Log File: C:\ProgramData\Veeam\Backup\Utils\Util.InfrastructureStatistic.log
- Error Example:
Error (1) Failed to login to platform service (ID: [{guid}]): Failed to execute VeeamAuth: 'Veeam.Backup.Identity.Client.TokenAuthenticationException: Unable to perform authorization: The client does not have access permissions for the resource.
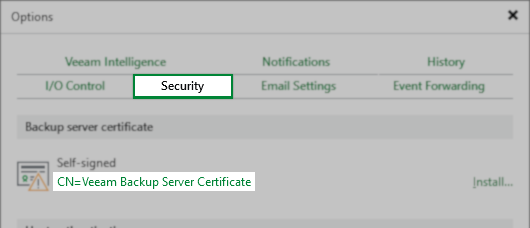
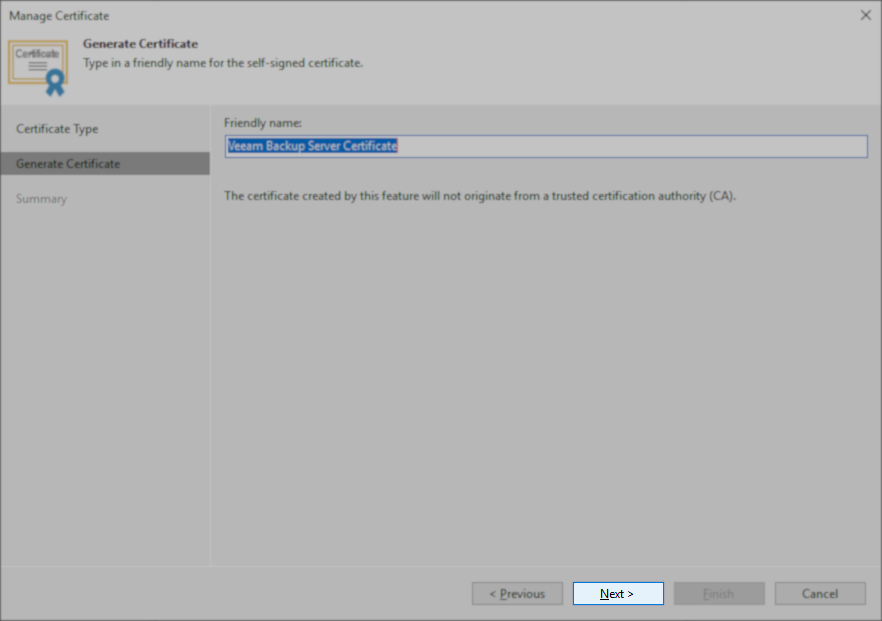
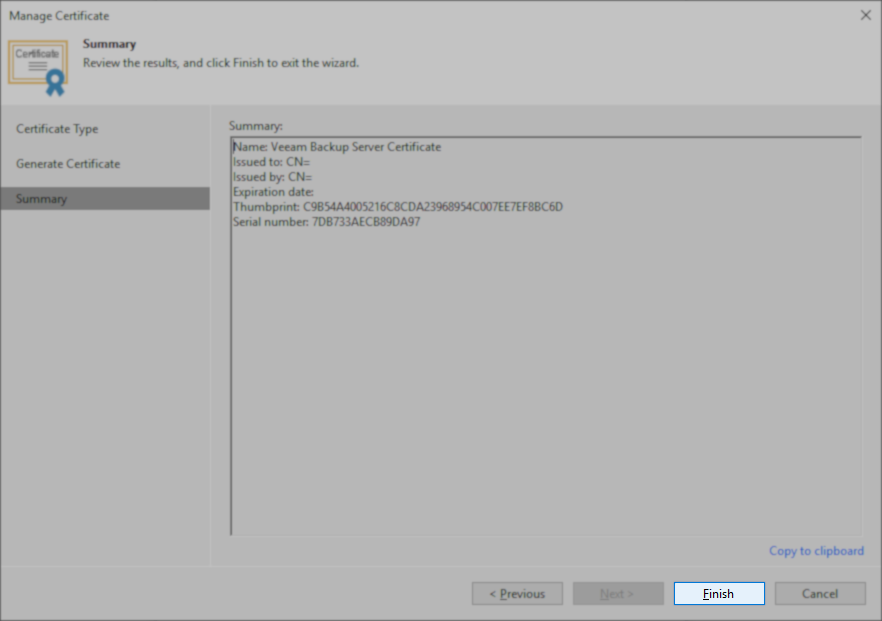
Issue 2: The Veeam Backup Server Certificate is missing the field "Basic Constraints".
- Related Log File: C:\ProgramData\Veeam\Backup\Svc.PlatformDbProvider.log
- Error Example:
Error (1) Failed to generate certificate. Error (1) The issuer certificate does not have a Basic Constraints extension. (Parameter 'issuerCertificate') (System.ArgumentException)
- Secondary Logged Message:
Failed to generate child certificate from Veeam backup server certificate.
Issue 3: PlatformDbProvider Service Using Wrong Port
- Related Log Files and Examples:
- C:\ProgramData\Veeam\Backup\Plugins\PVE\Veeam.PVE.PlatformSvc.log
ERROR | [PlatformService]: Failed to start PlatformService: System.Net.Http.HttpRequestException: No connection could be made because the target machine actively refused it. (localhost:6172) ERROR | [PlatformService]: ---> System.Net.Sockets.SocketException (10061): No connection could be made because the target machine actively refused it.
-
C:\ProgramData\Veeam\Backup\Plugins\RHV\Veeam.RHV.PlatformSvc.log C:\ProgramData\Veeam\Backup\Plugins\AHV\Veeam.AHV.PlatformSvc.log
ERROR | [StorageClient]: ==> Response "Get" "https://localhost:6172/api", "status: Error", duration: "2 sec 32 msec", body: """" ERROR | [StorageClient]: Exception accrued during connection attempt: No connection could be made because the target machine actively refused it. (localhost:6172)
- C:\ProgramData\Veeam\Backup\Plugins\PVE\Veeam.PVE.PlatformSvc.log
If this KB article did not resolve your issue or you need further assistance with Veeam software, please create a Veeam Support Case.
To submit feedback regarding this article, please click this link: Send Article Feedback
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
Spelling error in text
KB Feedback/Suggestion
This form is only for KB Feedback/Suggestions, if you need help with the software open a support case